Updated TSA Directive for Cybersecurity for Pipelines The National Law Review
http://dlvr.it/SVqn5f
Sunday, July 31, 2022
Week in review: Attackers abandoning malicious macros, average data breach cost soars - Help Net Security
Week in review: Attackers abandoning malicious macros, average data breach cost soars Help Net Security
http://dlvr.it/SVqHpS
http://dlvr.it/SVqHpS
Saturday, July 30, 2022
Self-promotion in cybersecurity: Why you should do it, and how - Help Net Security
Self-promotion in cybersecurity: Why you should do it, and how Help Net Security
http://dlvr.it/SVnZX0
http://dlvr.it/SVnZX0
Cyber Security Insurance Market May See a Big Move : Major Giants AXA, Beazley, Allianz - Insurance News Net
Cyber Security Insurance Market May See a Big Move : Major Giants AXA, Beazley, Allianz Insurance News Net
http://dlvr.it/SVnMjx
http://dlvr.it/SVnMjx
Stop Putting Your Accounts At Risk, and Start Using a Password Manager
Image via Keeper
Right Now, Get 30% Off Keeper, the Most Trusted Name in Password Management.
In one way or another, almost every aspect of our lives is online, so it’s no surprise that hackers target everything from email accounts to banks to smart home devices, looking for vulnerabilities to exploit. One of the easiest exploits is cracking a weak password. That’s why using a strong, unique
http://dlvr.it/SVn5hv
http://dlvr.it/SVn5hv
Just Why Are So Many Cyber Breaches Due to Human Error? - Security Today
Just Why Are So Many Cyber Breaches Due to Human Error? Security Today
http://dlvr.it/SVmnbr
http://dlvr.it/SVmnbr
CISA Warns of Atlassian Confluence Hard-Coded Credential Bug Exploited in Attacks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added the recently disclosed Atlassian security flaw to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation.
The vulnerability, tracked as CVE-2022-26138, concerns the use of hard-coded credentials when the Questions For Confluence app is enabled in Confluence Server and Data Center
http://dlvr.it/SVmQGZ
http://dlvr.it/SVmQGZ
Friday, July 29, 2022
US Departments of Labor, Commerce announce 120-Day Cybersecurity Apprenticeship Sprint to promote Registered Apprenticeships - US Department of Labor
US Departments of Labor, Commerce announce 120-Day Cybersecurity Apprenticeship Sprint to promote Registered Apprenticeships US Department of Labor
http://dlvr.it/SVl2V9
http://dlvr.it/SVl2V9
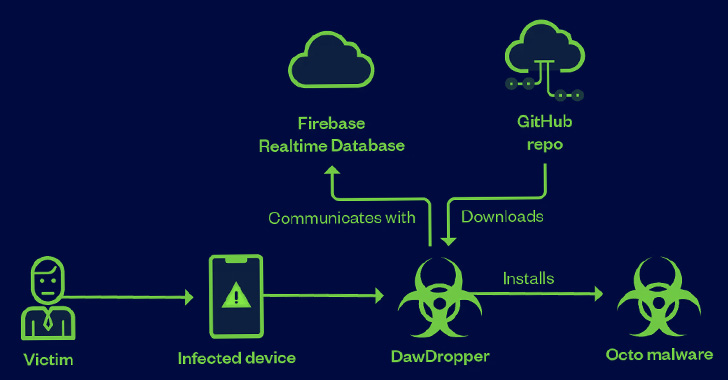
Over a Dozen Android Apps on Google Play Store Caught Dropping Banking Malware
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware.
These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others. All these apps in question have been
http://dlvr.it/SVkJSV
http://dlvr.it/SVkJSV
Latest Critical Atlassian Confluence Vulnerability Under Active Exploitation
A week after Atlassian rolled out patches to contain a critical flaw in its Questions For Confluence app for Confluence Server and Confluence Data Center, the shortcoming has now come under active exploitation in the wild.
The bug in question is CVE-2022-26138, which concerns the use of a hard-coded password in the app that could be exploited by a remote, unauthenticated attacker to gain
http://dlvr.it/SVjn87
http://dlvr.it/SVjn87
Thursday, July 28, 2022
Bridging the Cybersecurity Careers Guidance Gap - ComputerWeekly.com
Bridging the Cybersecurity Careers Guidance Gap ComputerWeekly.com
http://dlvr.it/SVhBsP
http://dlvr.it/SVhBsP
CyberCX introduces the 'largest' private sector cyber security training academy - Cyber Security Connect
CyberCX introduces the 'largest' private sector cyber security training academy Cyber Security Connect
http://dlvr.it/SVgw3p
http://dlvr.it/SVgw3p
Google Delays Blocking 3rd-Party Cookies in Chrome Browser Until 2024
Google on Wednesday said it's once again delaying its plans to turn off third-party cookies in the Chrome web browser from late 2023 to the second half of 2024.
"The most consistent feedback we've received is the need for more time to evaluate and test the new Privacy Sandbox technologies before deprecating third-party cookies in Chrome," Anthony Chavez, vice president of Privacy Sandbox, said.
http://dlvr.it/SVg5mH
http://dlvr.it/SVg5mH
CVE-2022-35628
A SQL injection issue was discovered in the lux extension before 17.6.1, and 18.x through 24.x before 24.0.2, for TYPO3. (CVSS:7.5) (Last Update:2022-07-27)
http://dlvr.it/SVfYQH
http://dlvr.it/SVfYQH
Wednesday, July 27, 2022
Global Cyber Security Services Market to Reach $390 Billion | Increasing Cybercrimes are expected to Hit Value of 10.5 trillion - Yahoo Finance
Global Cyber Security Services Market to Reach $390 Billion | Increasing Cybercrimes are expected to Hit Value of 10.5 trillion Yahoo Finance
http://dlvr.it/SVcv33
http://dlvr.it/SVcv33
Talking Public Sector Cybersecurity with Nclose - ITNA Digital Innovation Podcast EP 6 - IT News Africa
Talking Public Sector Cybersecurity with Nclose - ITNA Digital Innovation Podcast EP 6 IT News Africa
http://dlvr.it/SVcbmD
http://dlvr.it/SVcbmD
Minimizing Cybersecurity Risks that Can Leave Your Customers Uninsurable, Podcast - Telecom Reseller
Minimizing Cybersecurity Risks that Can Leave Your Customers Uninsurable, Podcast Telecom Reseller
http://dlvr.it/SVcDrB
http://dlvr.it/SVcDrB
These 28+ Android Apps with 10 Million Downloads from the Play Store Contain Malware
As many as 30 malicious Android apps with cumulative downloads of nearly 10 million have been found on the Google Play Store distributing adware.
"All of them were built into various programs, including image-editing software, virtual keyboards, system tools and utilities, calling apps, wallpaper collection apps, and others," Dr.Web said in a Tuesday write-up.
While masquerading as innocuous
http://dlvr.it/SVbnHq
http://dlvr.it/SVbnHq
Malicious IIS Extensions Gaining Popularity Among Cyber Criminals for Persistent Access
Threat actors are increasingly abusing Internet Information Services (IIS) extensions to backdoor servers as a means of establishing a "durable persistence mechanism."
That's according to a new warning from the Microsoft 365 Defender Research Team, which said that "IIS backdoors are also harder to detect since they mostly reside in the same directories as legitimate modules used by target
http://dlvr.it/SVbFM3
http://dlvr.it/SVbFM3
Tuesday, July 26, 2022
Assured Cyber Security Consultancy - NCSC.GOV.UK - National Cyber Security Centre
Assured Cyber Security Consultancy - NCSC.GOV.UK National Cyber Security Centre
http://dlvr.it/SVYd6f
http://dlvr.it/SVYd6f
Policybazaar admits cyber security incident, says customer data safe - Telangana Today
Policybazaar admits cyber security incident, says customer data safe Telangana Today
http://dlvr.it/SVYLcg
http://dlvr.it/SVYLcg
Relentless vulnerabilities and patches induce cybersecurity burnout - Cybersecurity Dive
Relentless vulnerabilities and patches induce cybersecurity burnout Cybersecurity Dive
http://dlvr.it/SVY0R6
http://dlvr.it/SVY0R6
Hackers Increasingly Using WebAssembly Coded Cryptominers to Evade Detection
As many as 207 websites have been infected with malicious code designed to launch a cryptocurrency miner by leveraging WebAssembly (Wasm) on the browser.
Web security company Sucuri, which published details of the campaign, said it launched an investigation after one of its clients had their computer slowed down significantly every time upon navigating to their own WordPress portal.
This
http://dlvr.it/SVXYr5
http://dlvr.it/SVXYr5
SmokeLoader Infecting Targeted Systems with Amadey Info-Stealing Malware
An information-stealing malware called Amadey is being distributed by means of another backdoor called SmokeLoader.
The attacks hinge on tricking users into downloading SmokeLoader that masquerades as software cracks, paving the way for the deployment of Amadey, researchers from the AhnLab Security Emergency Response Center (ASEC) said in a report published last week.
Amadey, a
http://dlvr.it/SVX3Bf
http://dlvr.it/SVX3Bf
Monday, July 25, 2022
‘Some staff work behind armoured glass’: a cybersecurity expert on The Undeclared War - The Guardian
‘Some staff work behind armoured glass’: a cybersecurity expert on The Undeclared War The Guardian
http://dlvr.it/SVVVnZ
http://dlvr.it/SVVVnZ
NCUA cyber breach rule would give credit unions longer reporting window than banks - Banking Dive
NCUA cyber breach rule would give credit unions longer reporting window than banks Banking Dive
http://dlvr.it/SVVF51
http://dlvr.it/SVVF51
Google backs federal review board's Log4j, open source security push - Cybersecurity Dive
Google backs federal review board's Log4j, open source security push Cybersecurity Dive
http://dlvr.it/SVTvyT
http://dlvr.it/SVTvyT
Experts Uncover New 'CosmicStrand' UEFI Firmware Rootkit Used by Chinese Hackers
An unknown Chinese-speaking threat actor has been attributed to a new kind of sophisticated UEFI firmware rootkit called CosmicStrand.
"The rootkit is located in the firmware images of Gigabyte or ASUS motherboards, and we noticed that all these images are related to designs using the H81 chipset," Kaspersky researchers said in a new report published today. "This suggests that a common
http://dlvr.it/SVTVTS
http://dlvr.it/SVTVTS
Roaming Mantis Financial Hackers Targeting Android and iPhone Users in France
The mobile threat campaign tracked as Roaming Mantis has been linked to a new wave of compromises directed against French mobile phone users, months after it expanded its targeting to include European countries.
No fewer than 70,000 Android devices are said to have been infected as part of the active malware operation, Sekoia said in a report published last week.
Attack chains involving Roaming
http://dlvr.it/SVT0fM
http://dlvr.it/SVT0fM
Sunday, July 24, 2022
NSA Cybersecurity - National Security Agency
NSA Cybersecurity National Security Agency
http://dlvr.it/SVRJnK
http://dlvr.it/SVRJnK
Fantastic Open Source Cybersecurity Tools and Where to Find Them - Data Center Knowledge
Fantastic Open Source Cybersecurity Tools and Where to Find Them Data Center Knowledge
http://dlvr.it/SVQpLJ
http://dlvr.it/SVQpLJ
CVE-2022-34598
The udpserver in H3C Magic R100 V200R004 and V100R005 has the 9034 port opened, allowing attackers to execute arbitrary commands. (CVSS:7.5) (Last Update:2022-07-14)
http://dlvr.it/SVQV6Q
http://dlvr.it/SVQV6Q
Monday, July 4, 2022
China Cybersecurity and Data Protection: Monthly Update - June 2022 Issue - Lexology
China Cybersecurity and Data Protection: Monthly Update - June 2022 Issue Lexology
http://dlvr.it/STLddQ
http://dlvr.it/STLddQ
How organisations can implement a successful cybersecurity strategy - Gulf Business
How organisations can implement a successful cybersecurity strategy Gulf Business
http://dlvr.it/STLLzQ
http://dlvr.it/STLLzQ
Automotive Cyber Security Market Size And Forecast | Arilou technologies, Cisco systems, Harman (TowerSec), SBD Automotive & Ncc Group, Argus, BT Security, Intel Corporation, ESCRYPT Embedded Systems, NXP Semiconductors, Trillium – Designe - Designer Women
Automotive Cyber Security Market Size And Forecast | Arilou technologies, Cisco systems, Harman (TowerSec), SBD Automotive & Ncc Group, Argus, BT Security, Intel Corporation, ESCRYPT Embedded Systems, NXP Semiconductors, Trillium – Designe Designer Women
http://dlvr.it/STL0Ld
http://dlvr.it/STL0Ld
HackerOne Employee Caught Stealing Vulnerability Reports for Personal Gains
Vulnerability coordination and bug bounty platform HackerOne on Friday disclosed that a former employee at the firm improperly accessed security reports submitted to it for personal gain.
"The person anonymously disclosed this vulnerability information outside the HackerOne platform with the goal of claiming additional bounties," it said. "In under 24 hours, we worked quickly to contain the
http://dlvr.it/STKXDT
http://dlvr.it/STKXDT
Sunday, July 3, 2022
Cyber Innovation Fellows Initiative - CISA
Cyber Innovation Fellows Initiative CISA
http://dlvr.it/STHGmc
http://dlvr.it/STHGmc
Saturday, July 2, 2022
5 Real-World AI Cybersecurity Applications That May Benefit Your Business - Hashed Out by The SSL Store™
5 Real-World AI Cybersecurity Applications That May Benefit Your Business Hashed Out by The SSL Store™
http://dlvr.it/STF9mv
http://dlvr.it/STF9mv
TikTok Assures U.S. Lawmakers it's Working to Safeguard User Data From Chinese Staff
Following heightened worries that U.S. users' data had been accessed by TikTok engineers in China between September 2021 and January 2022, the company sought to assuage U.S. lawmakers that it's taking steps to "strengthen data security."
The admission that some China-based employees can access information from U.S. users came in a letter sent to nine senators, which further noted that the
http://dlvr.it/STDrGQ
http://dlvr.it/STDrGQ
Friday, July 1, 2022
CVE-2022-32535
The Bosch Ethernet switch PRA-ES8P2S with software version 1.01.05 runs its web server with root privilege. In combination with CVE-2022-23534 this could give an attacker root access to the switch. (CVSS:10.0) (Last Update:2022-07-01)
http://dlvr.it/STCRKT
http://dlvr.it/STCRKT
CVE-2022-32534
The Bosch Ethernet switch PRA-ES8P2S with software version 1.01.05 and earlier was found to be vulnerable to command injection through its diagnostics web interface. This allows execution of shell commands. (CVSS:10.0) (Last Update:2022-07-01)
http://dlvr.it/STCRHm
http://dlvr.it/STCRHm
CISA and Coast Guard Cyber Command Warn About Hackers Leveraging Log4Shell Vulnerability on VMware Servers - CPO Magazine
CISA and Coast Guard Cyber Command Warn About Hackers Leveraging Log4Shell Vulnerability on VMware Servers CPO Magazine
http://dlvr.it/STC6zg
http://dlvr.it/STC6zg
Google Improves Its Password Manager to Boost Security Across All Platforms
Google on Thursday announced a slew of improvements to its password manager service aimed at creating a more consistent look and feel across different platforms.
Central to the changes is a "simplified and unified management experience that's the same in Chrome and Android settings," Ali Sarraf, Google Chrome product manager, said in a blog post.
The updates are also expected to automatically
http://dlvr.it/STBhnn
http://dlvr.it/STBhnn
Amazon Quietly Patches 'High Severity' Vulnerability in Android Photos App
Amazon, in December 2021, patched a high severity vulnerability affecting its Photos app for Android that could have been exploited to steal a user's access tokens.
"The Amazon access token is used to authenticate the user across multiple Amazon APIs, some of which contain personal data such as full name, email, and address," Checkmarx researchers João Morais and Pedro Umbelino said. "Others,
http://dlvr.it/STB9jg
http://dlvr.it/STB9jg
Subscribe to:
Posts (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...

































/cloudfront-us-east-2.images.arcpublishing.com/reuters/Z7ENANJTO5MQDFBM7VLPGSUHA4.jpg)


/cloudfront-us-east-1.images.arcpublishing.com/gray/JHBZUR7MPZHTNJTZVPQ22I7ISQ.PNG)