This is why 2024 will be a good year for social workers, quantity surveyors and cyber security managers Daily Mail
http://dlvr.it/T0q032
Sunday, December 31, 2023
When Predatory Sparrow Strikes: Israel-Iran Shadow War Awakens - National Security & Cyber - Haaretz
When Predatory Sparrow Strikes: Israel-Iran Shadow War Awakens - National Security & Cyber Haaretz
http://dlvr.it/T0pGFS
http://dlvr.it/T0pGFS
Saturday, December 30, 2023
Cybersecurity: American Business Council, Stakeholders Unveil Cyber Hub - TechCabal
Cybersecurity: American Business Council, Stakeholders Unveil Cyber Hub TechCabal
http://dlvr.it/T0n9dc
http://dlvr.it/T0n9dc
Uncovering Cyber Threats through Code Analysis: A New Approach to Cybersecurity - Medriva
Uncovering Cyber Threats through Code Analysis: A New Approach to Cybersecurity Medriva
http://dlvr.it/T0n9RC
http://dlvr.it/T0n9RC
First American says system has been restored; perpetrator stole data - HousingWire
First American says system has been restored; perpetrator stole data HousingWire
http://dlvr.it/T0n9Hz
http://dlvr.it/T0n9Hz
Cyberattack on Massachusetts hospital disrupted records system, emergency services - The Record from Recorded Future News
Cyberattack on Massachusetts hospital disrupted records system, emergency services The Record from Recorded Future News
http://dlvr.it/T0n97S
http://dlvr.it/T0n97S
Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks
Cybersecurity researchers are warning about an increase in phishing attacks that are capable of draining cryptocurrency wallets.
"These threats are unique in their approach, targeting a wide range of blockchain networks, from Ethereum and Binance Smart Chain to Polygon, Avalanche, and almost 20 other networks by using a crypto wallet-draining technique," Check Point researchers Oded Vanunu,
http://dlvr.it/T0mjxV
"These threats are unique in their approach, targeting a wide range of blockchain networks, from Ethereum and Binance Smart Chain to Polygon, Avalanche, and almost 20 other networks by using a crypto wallet-draining technique," Check Point researchers Oded Vanunu,
http://dlvr.it/T0mjxV
Friday, December 29, 2023
CERT-UA Uncovers New Malware Wave Distributing OCEANMAP, MASEPIE, STEELHOOK
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign orchestrated by the Russia-linked APT28 group to deploy previously undocumented malware such as OCEANMAP, MASEPIE, and STEELHOOK to harvest sensitive information.
The activity, which was detected by the agency between December 15 and 25, 2023, targets government entities
http://dlvr.it/T0kx2B
The activity, which was detected by the agency between December 15 and 25, 2023, targets government entities
http://dlvr.it/T0kx2B
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks
Nation-state actors affiliated to North Korea have been observed using spear-phishing attacks to deliver an assortment of backdoors and tools such as AppleSeed, Meterpreter, and TinyNuke to seize control of compromised machines.
South Korea-based cybersecurity company AhnLab attributed the activity to an advanced persistent threat group known as Kimsuky.
“A notable point about attacks that
http://dlvr.it/T0kwbB
South Korea-based cybersecurity company AhnLab attributed the activity to an advanced persistent threat group known as Kimsuky.
“A notable point about attacks that
http://dlvr.it/T0kwbB
Microsoft Disables MSIX App Installer Protocol Widely Used in Malware Attacks
Microsoft on Thursday said it’s once again disabling the ms-appinstaller protocol handler by default following its abuse by multiple threat actors to distribute malware.
“The observed threat actor activity abuses the current implementation of the ms-appinstaller protocol handler as an access vector for malware that may lead to ransomware distribution,” the Microsoft Threat Intelligence
http://dlvr.it/T0kwDr
“The observed threat actor activity abuses the current implementation of the ms-appinstaller protocol handler as an access vector for malware that may lead to ransomware distribution,” the Microsoft Threat Intelligence
http://dlvr.it/T0kwDr
Thursday, December 28, 2023
Social media users warned against oversharing amid ‘Get to know me on Instagram’ challenge - WION
Social media users warned against oversharing amid ‘Get to know me on Instagram’ challenge WION
http://dlvr.it/T0j8XK
http://dlvr.it/T0j8XK
Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service
Google Cloud has addressed a medium-severity security flaw in its platform that could be abused by an attacker who already has access to a Kubernetes cluster to escalate their privileges.
"An attacker who has compromised the Fluent Bit logging container could combine that access with high privileges required by Anthos Service Mesh (on clusters that have enabled it) to
http://dlvr.it/T0hpdt
"An attacker who has compromised the Fluent Bit logging container could combine that access with high privileges required by Anthos Service Mesh (on clusters that have enabled it) to
http://dlvr.it/T0hpdt
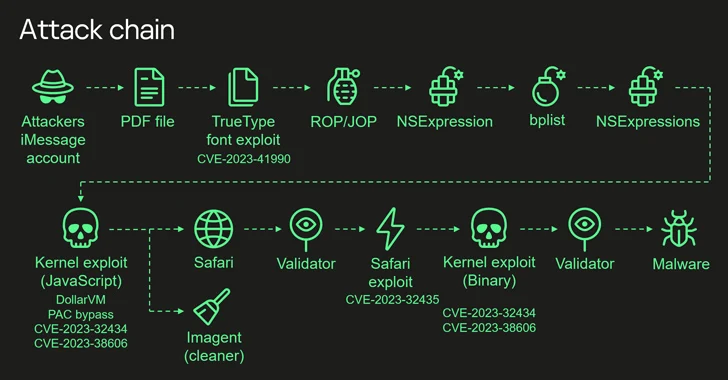
Most Sophisticated iPhone Hack Ever Exploited Apple's Hidden Hardware Feature
The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections erected by the company.
Russian cybersecurity firm Kaspersky, which discovered the campaign at the beginning of 2023 after becoming one of the targets, described it as
http://dlvr.it/T0hpGP
Russian cybersecurity firm Kaspersky, which discovered the campaign at the beginning of 2023 after becoming one of the targets, described it as
http://dlvr.it/T0hpGP
New Rugmi Malware Loader Surges with Hundreds of Daily Detections
A new malware loader is being used by threat actors to deliver a wide range of information stealers such as Lumma Stealer (aka LummaC2), Vidar, RecordBreaker (aka Raccoon Stealer V2), and Rescoms.
Cybersecurity firm ESET is tracking the trojan under the name Win/TrojanDownloader.Rugmi.
"This malware is a loader with three types of components: a downloader that downloads an
http://dlvr.it/T0hnvn
Cybersecurity firm ESET is tracking the trojan under the name Win/TrojanDownloader.Rugmi.
"This malware is a loader with three types of components: a downloader that downloads an
http://dlvr.it/T0hnvn
Wednesday, December 27, 2023
Ubisoft Investigates Cyber Attack: Possible Data Exfiltration by Hackers - GBHackers
Ubisoft Investigates Cyber Attack: Possible Data Exfiltration by Hackers GBHackers
http://dlvr.it/T0g0Yn
http://dlvr.it/T0g0Yn
Uncrewed traffic management cybersecurity model gets green light from FAA - Military Embedded Systems
Uncrewed traffic management cybersecurity model gets green light from FAA Military Embedded Systems
http://dlvr.it/T0g0Qd
http://dlvr.it/T0g0Qd
5G Network Security Market is estimated to reach US$16.159 billion by 2028 at a CAGR of 41.82% - EIN News
5G Network Security Market is estimated to reach US$16.159 billion by 2028 at a CAGR of 41.82% EIN News
http://dlvr.it/T0ffjn
http://dlvr.it/T0ffjn
Man says fraudulent accounts opened, home purchased in his name after city ransomware hack - WLS-TV
Man says fraudulent accounts opened, home purchased in his name after city ransomware hack WLS-TV
http://dlvr.it/T0ffQR
http://dlvr.it/T0ffQR
California man says fraudulent accounts opened, home purchased in his name since city of Oakland ransomware attack - WPVI-TV
California man says fraudulent accounts opened, home purchased in his name since city of Oakland ransomware attack WPVI-TV
http://dlvr.it/T0ff8x
http://dlvr.it/T0ff8x
Tuesday, December 26, 2023
CMS IT Services: Helping Organizations with Industry-leading Cybersecurity Excellence - Siliconindia
CMS IT Services: Helping Organizations with Industry-leading Cybersecurity Excellence Siliconindia
http://dlvr.it/T0ccSl
http://dlvr.it/T0ccSl
Carbanak Banking Malware Resurfaces with New Ransomware Tactics
The banking malware known as Carbanak has been observed being used in ransomware attacks with updated tactics.
"The malware has adapted to incorporate attack vendors and techniques to diversify its effectiveness," cybersecurity firm NCC Group said in an analysis of ransomware attacks that took place in November 2023.
"Carbanak returned last month through new
http://dlvr.it/T0cbWm
"The malware has adapted to incorporate attack vendors and techniques to diversify its effectiveness," cybersecurity firm NCC Group said in an analysis of ransomware attacks that took place in November 2023.
"Carbanak returned last month through new
http://dlvr.it/T0cbWm
Monday, December 25, 2023
Infosecurity Magazine's Most Read Cybersecurity Stories of 2023 - Infosecurity Magazine
Infosecurity Magazine's Most Read Cybersecurity Stories of 2023 Infosecurity Magazine
http://dlvr.it/T0Zx52
http://dlvr.it/T0Zx52
Cloud Atlas' Spear-Phishing Attacks Target Russian Agro and Research Companies - The Hacker News
Cloud Atlas' Spear-Phishing Attacks Target Russian Agro and Research Companies The Hacker News
http://dlvr.it/T0ZwcG
http://dlvr.it/T0ZwcG
Cloud Atlas' Spear-Phishing Attacks Target Russian Agro and Research Companies
The threat actor referred to as Cloud Atlas has been linked to a set of spear-phishing attacks on Russian enterprises.
Targets included a Russian agro-industrial enterprise and a state-owned research company, according to a report from F.A.C.C.T., a standalone cybersecurity company formed after Group-IB's formal exit from Russia earlier this year.
Cloud Atlas, active since at
http://dlvr.it/T0ZwCK
Targets included a Russian agro-industrial enterprise and a state-owned research company, according to a report from F.A.C.C.T., a standalone cybersecurity company formed after Group-IB's formal exit from Russia earlier this year.
Cloud Atlas, active since at
http://dlvr.it/T0ZwCK
Sunday, December 24, 2023
Managing Cybersecurity Risks Related to AI in Developing Countries: Strategies and Solutions - Part II - Modern Diplomacy
Managing Cybersecurity Risks Related to AI in Developing Countries: Strategies and Solutions - Part II Modern Diplomacy
http://dlvr.it/T0YM4Q
http://dlvr.it/T0YM4Q
British LAPSUS$ Teen Members Sentenced for High-Profile Attacks - The Hacker News
British LAPSUS$ Teen Members Sentenced for High-Profile Attacks The Hacker News
http://dlvr.it/T0YLt6
http://dlvr.it/T0YLt6
Monday, December 4, 2023
Microsoft Warns of Malvertising Scheme Spreading CACTUS Ransomware
Microsoft has warned of a new wave of CACTUS ransomware attacks that leverage malvertising lures to deploy DanaBot as an initial access vector.
The DanaBot infections led to "hands-on-keyboard activity by ransomware operator Storm-0216 (Twisted Spider, UNC2198), culminating in the deployment of CACTUS ransomware," the Microsoft Threat Intelligence team said in a series of posts on X (
http://dlvr.it/SzhFT9
The DanaBot infections led to "hands-on-keyboard activity by ransomware operator Storm-0216 (Twisted Spider, UNC2198), culminating in the deployment of CACTUS ransomware," the Microsoft Threat Intelligence team said in a series of posts on X (
http://dlvr.it/SzhFT9
Sunday, December 3, 2023
Oduma Solutions Limited hosts participants of global conference on ... - Myjoyonline
Oduma Solutions Limited hosts participants of global conference on ... Myjoyonline
http://dlvr.it/Szfnvy
http://dlvr.it/Szfnvy
Week in review: PoC for Splunk Enterprise RCE flaw released, scope of Okta breach widens - Help Net Security
Week in review: PoC for Splunk Enterprise RCE flaw released, scope of Okta breach widens Help Net Security
http://dlvr.it/SzfnkV
http://dlvr.it/SzfnkV
Low wages, lack of exposure among factors country lacks cyber ... - The Star Online
Low wages, lack of exposure among factors country lacks cyber ... The Star Online
http://dlvr.it/Szfnc5
http://dlvr.it/Szfnc5
So, You Think of Cybersecurity Only as a Cost Center? Think Again. - Foley & Lardner LLP
So, You Think of Cybersecurity Only as a Cost Center? Think Again. Foley & Lardner LLP
http://dlvr.it/Szf6mL
http://dlvr.it/Szf6mL
Saturday, December 2, 2023
Ransomware attack in US: Dozens of credit unions experience outrages due to cyberattack on Trellance, federal ... - WABC-TV
Ransomware attack in US: Dozens of credit unions experience outrages due to cyberattack on Trellance, federal ... WABC-TV
http://dlvr.it/Szd4tB
http://dlvr.it/Szd4tB
Cybersecurity Spending Is Slowing: 2 Top Stocks That Can Weather the Storm - The Motley Fool
Cybersecurity Spending Is Slowing: 2 Top Stocks That Can Weather the Storm The Motley Fool
http://dlvr.it/Szd4lK
http://dlvr.it/Szd4lK
Subscribe to:
Posts (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...