N.J. hospital halts admitting patients after cybersecurity issue NJ.com
http://dlvr.it/Sg9yCW
Saturday, December 31, 2022
Researcher Uncovers Potential Wiretapping Bugs in Google Home Smart Speakers
A security researcher was awarded a bug bounty of $107,500 for identifying security issues in Google Home smart speakers that could be exploited to install backdoors and turn them into wiretapping devices.
The flaws "allowed an attacker within wireless proximity to install a 'backdoor' account on the device, enabling them to send commands to it remotely over the internet, access its microphone
http://dlvr.it/Sg9y2S
http://dlvr.it/Sg9y2S
Friday, December 30, 2022
APT Hackers Turn to Malicious Excel Add-ins as Initial Intrusion Vector
Microsoft's decision to block Visual Basic for Applications (VBA) macros by default for Office files downloaded from the internet has led many threat actors to improvise their attack chains in recent months.
Now according to Cisco Talos, advanced persistent threat (APT) actors and commodity malware families alike are increasingly using Excel add-in (.XLL) files as an initial intrusion vector.
http://dlvr.it/Sg7bfr
http://dlvr.it/Sg7bfr
BlueNoroff APT Hackers Using New Ways to Bypass Windows MotW Protection
BlueNoroff, a subcluster of the notorious Lazarus Group, has been observed adopting new techniques into its playbook that enable it to bypass Windows Mark of the Web (MotW) protections.
This includes the use of optical disk image (.ISO extension) and virtual hard disk (.VHD extension) file formats as part of a novel infection chain, Kaspersky disclosed in a report published today.
"BlueNoroff
http://dlvr.it/Sg7bPy
http://dlvr.it/Sg7bPy
Thursday, December 29, 2022
Wednesday, December 28, 2022
As Cybersecurity Threats Increase, Lawyers Have Practical Advice ... - Morrison Foerster
As Cybersecurity Threats Increase, Lawyers Have Practical Advice ... Morrison Foerster
http://dlvr.it/Sg2Syl
http://dlvr.it/Sg2Syl
Tuesday, December 27, 2022
2022 Top Five Immediate Threats in Geopolitical Context
As we are nearing the end of 2022, looking at the most concerning threats of this turbulent year in terms of testing numbers offers a threat-based perspective on what triggers cybersecurity teams to check how vulnerable they are to specific threats. These are the threats that were most tested to validate resilience with the Cymulate security posture management platform between January 1st and
http://dlvr.it/SfzxP2
http://dlvr.it/SfzxP2
PrivateLoader PPI Service Found Distributing Info-Stealing RisePro Malware
The pay-per-install (PPI) malware downloader service known as PrivateLoader is being used to distribute a previously documented information-stealing malware dubbed RisePro.
Flashpoint spotted the newly identified stealer on December 13, 2022, after it discovered "several sets of logs" exfiltrated using the malware on an illicit cybercrime marketplace called Russian Market.
A C++-based malware,
http://dlvr.it/SfzxCm
http://dlvr.it/SfzxCm
Monday, December 26, 2022
Google Heads Top Cybersecurity Acquisitions of 2022 - SDxCentral
Google Heads Top Cybersecurity Acquisitions of 2022 SDxCentral
http://dlvr.it/SfxljR
http://dlvr.it/SfxljR
Sunday, December 25, 2022
Despite physical threats to the U.S. power grid, cybersecurity has remained the focus - Yahoo News
Despite physical threats to the U.S. power grid, cybersecurity has remained the focus Yahoo News
http://dlvr.it/Sfvzg7
http://dlvr.it/Sfvzg7
Cyber Security Today, Week in Review for Friday, December 23, 2022 - IT World Canada
Cyber Security Today, Week in Review for Friday, December 23, 2022 IT World Canada
http://dlvr.it/SfvzPJ
http://dlvr.it/SfvzPJ
W4SP Stealer Discovered in Multiple PyPI Packages Under Various Names
Threat actors have published yet another round of malicious packages to Python Package Index (PyPI) with the goal of delivering information-stealing malware on compromised developer machines.
Interestingly, while the malware goes by a variety of names like ANGEL Stealer, Celestial Stealer, Fade Stealer, Leaf $tealer, PURE Stealer, Satan Stealer, and @skid Stealer, cybersecurity company Phylum
http://dlvr.it/Sfvytk
http://dlvr.it/Sfvytk
Saturday, December 24, 2022
France Fines Microsoft €60 Million for Using Advertising Cookies Without User Consent
France's privacy watchdog has imposed a €60 million ($63.88 million) fine against Microsoft's Ireland subsidiary for dropping advertising cookies in users' computers without their explicit consent in violation of data protection laws in the European Union.
The Commission nationale de l'informatique et des libertés (CNIL) noted that users visiting the home page of its Bing search engine did not
http://dlvr.it/Sft3QM
http://dlvr.it/Sft3QM
Friday, December 23, 2022
Two New Security Flaws Reported in Ghost CMS Blogging Software
Cybersecurity researchers have detailed two security flaws in the JavaScript-based blogging platform known as Ghost, one of which could be abused to elevate privileges via specially crafted HTTP requests.
Tracked as CVE-2022-41654 (CVSS score: 8.5), the authentication bypass vulnerability allows unprivileged users (i.e., members) to make unauthorized modifications to newsletter settings.
Cisco
http://dlvr.it/SfqTWD
http://dlvr.it/SfqTWD
Zerobot Botnet Emerges as a Growing Threat with New Exploits and Capabilities
The Zerobot DDoS botnet has received substantial updates that expand on its ability to target more internet-connected devices and scale its network.
Microsoft Threat Intelligence Center (MSTIC) is tracking the ongoing threat under the moniker DEV-1061, its designation for unknown, emerging, or developing activity clusters.
Zerobot, first documented by Fortinet FortiGuard Labs earlier this month,
http://dlvr.it/SfqTDr
http://dlvr.it/SfqTDr
Thursday, December 22, 2022
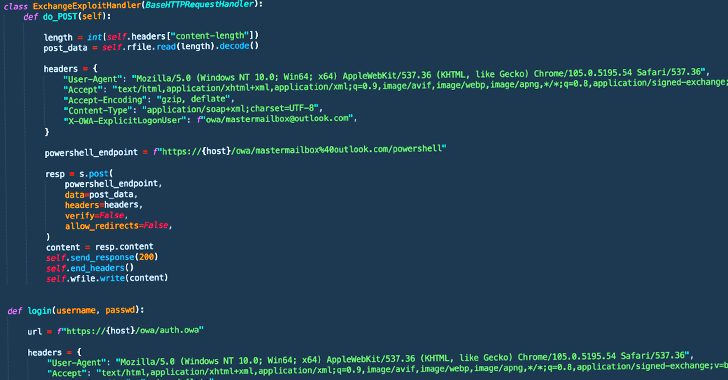
Ransomware Hackers Using New Way to Bypass MS Exchange ProxyNotShell Mitigations
Threat actors affiliated with a ransomware strain known as Play are leveraging a never-before-seen exploit chain that bypasses blocking rules for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution (RCE) through Outlook Web Access (OWA).
"The new exploit method bypasses URL rewrite mitigations for the Autodiscover endpoint," CrowdStrike researchers Brian Pitchford,
http://dlvr.it/SfmZDh
http://dlvr.it/SfmZDh
Wednesday, December 21, 2022
KmsdBot Botnet Suspected of Being Used as DDoS-for-Hire Service
An ongoing analysis of the KmsdBot botnet has raised the possibility that it's a DDoS-for-hire service offered to other threat actors.
This is based on the different industries and geographies that were attacked, web infrastructure company Akamai said. Among the notable targets included FiveM and RedM, which are game modifications for Grand Theft Auto V and Red Dead Redemption 2, as well as
http://dlvr.it/SfjZ5K
http://dlvr.it/SfjZ5K
Tuesday, December 20, 2022
Facebook Cracks Down on Spyware Vendors from U.S., China, Russia, Israel, and India
Meta Platforms disclosed that it took down no less than 200 covert influence operations since 2017 spanning roughly 70 countries across 42 languages.
The social media conglomerate also took steps to disable accounts and block infrastructure operated by spyware vendors, including in China, Russia, Israel, the U.S. and India, that targeted individuals in about 200 countries.
"The global
http://dlvr.it/SffVNW
http://dlvr.it/SffVNW
Monday, December 19, 2022
AI-armed cyberattacks may get lethal in next 5 years, warns report - Interesting Engineering
AI-armed cyberattacks may get lethal in next 5 years, warns report Interesting Engineering
http://dlvr.it/SfbSxN
http://dlvr.it/SfbSxN
Sunday, December 18, 2022
UW-Stout professor among 'strong community of women' leading the ... - University of Wisconsin System
UW-Stout professor among 'strong community of women' leading the ... University of Wisconsin System
http://dlvr.it/SfYHjD
http://dlvr.it/SfYHjD
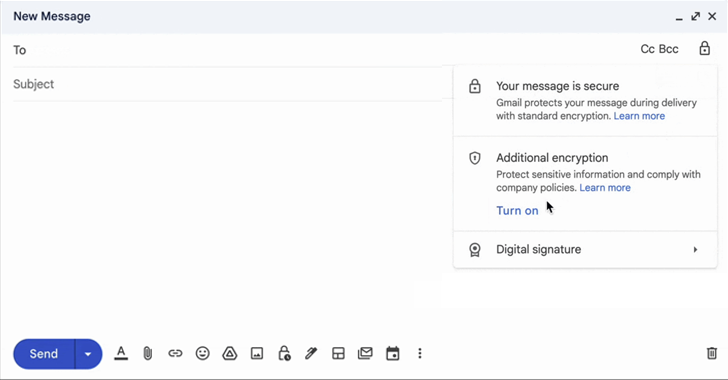
Google Takes Gmail Security to the Next Level with Client-Side Encryption
Google on Friday announced that its client-side encryption for Gmail is in beta to its Workspace and education customers to secure emails sent using the web version of the platform.
This development comes at a time when concerns about online privacy and data security are at an all-time high, and it is certainly welcomed by users who value the protection of their personal data.
To that end,
http://dlvr.it/SfYHV2
http://dlvr.it/SfYHV2
Saturday, December 17, 2022
Goodbye SHA-1: NIST Retires 27-Year-Old Widely Used Cryptographic Algorithm
The U.S. National Institute of Standards and Technology (NIST), an agency within the Department of Commerce, announced Thursday that it's formally retiring the SHA-1 cryptographic algorithm.
SHA-1, short for Secure Hash Algorithm 1, is a 27-year-old hash function used in cryptography and has since been deemed broken owing to the risk of collision attacks.
While hashes are designed to be
http://dlvr.it/SfW9zd
http://dlvr.it/SfW9zd
Friday, December 16, 2022
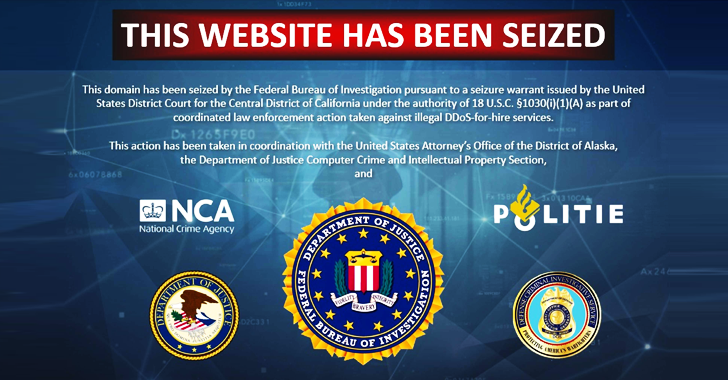
FBI Charges 6, Seizes 48 Domains Linked to DDoS-for-Hire Service Platforms
The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48 domains that offered services to conduct distributed denial-of-service (DDoS) attacks on behalf of other threat actors, effectively lowering the barrier to entry for malicious activity.
It also charged six suspects – Jeremiah Sam Evans Miller (23), Angel Manuel Colon Jr. (37), Shamar Shattock (19), Cory Anthony Palmer
http://dlvr.it/SfSKQ6
http://dlvr.it/SfSKQ6
Thursday, December 15, 2022
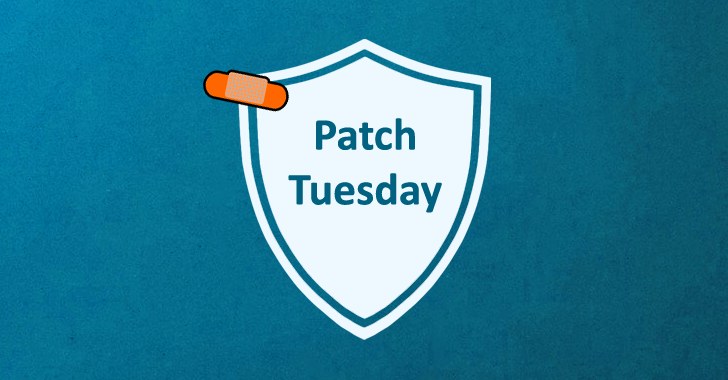
December 2022 Patch Tuesday: Get Latest Security Updates from Microsoft and More
Tech giant Microsoft released its last set of monthly security updates for 2022 with fixes for 49 vulnerabilities across its software products.
Of the 49 bugs, six are rated Critical, 40 are rated Important, and three are rated Moderate in severity. The updates are in addition to 24 vulnerabilities that have been addressed in the Chromium-based Edge browser since the start of the month.
http://dlvr.it/SfP9h5
http://dlvr.it/SfP9h5
Wednesday, December 14, 2022
Cybersecurity Experts Uncover Inner Workings of Destructive Azov Ransomware
Cybersecurity researchers have published the inner workings of a new wiper called Azov Ransomware that's deliberately designed to corrupt data and "inflict impeccable damage" to compromised systems.
Distributed through another malware loader known as SmokeLoader, the malware has been described as an "effective, fast, and unfortunately unrecoverable data wiper," by Israeli cybersecurity company
http://dlvr.it/SfL56r
http://dlvr.it/SfL56r
Tuesday, December 13, 2022
Keep Your Grinch at Bay: Here's How to Stay Safe Online this Holiday Season
As the holiday season approaches, online shopping and gift-giving are at the top of many people's to-do lists. But before you hit the "buy" button, it's important to remember that this time of year is also the peak season for cybercriminals.
In fact, cybercriminals often ramp up their efforts during the holidays, taking advantage of the influx of online shoppers and the general hustle and bustle
http://dlvr.it/SfGyrD
http://dlvr.it/SfGyrD
Royal Ransomware Threat Takes Aim at U.S. Healthcare System
The U.S. Department of Health and Human Services (HHS) has cautioned of ongoing Royal ransomware attacks targeting healthcare entities in the country.
"While most of the known ransomware operators have performed Ransomware-as-a-Service, Royal appears to be a private group without any affiliates while maintaining financial motivation as their goal," the agency's Health Sector Cybersecurity
http://dlvr.it/SfGybB
http://dlvr.it/SfGybB
Monday, December 12, 2022
Sunday, December 11, 2022
Hack-for-Hire Group Targets Travel and Financial Entities with New Janicab Malware Variant
Travel agencies have emerged as the target of a hack-for-hire group dubbed Evilnum as part of a broader campaign aimed at legal and financial investment institutions in the Middle East and Europe.
The attacks targeting law firms throughout 2020 and 2021 involved a revamped variant of a malware called Janicab that leverages a number of public services like YouTube as dead drop resolvers,
http://dlvr.it/Sf9q6S
http://dlvr.it/Sf9q6S
Saturday, December 10, 2022
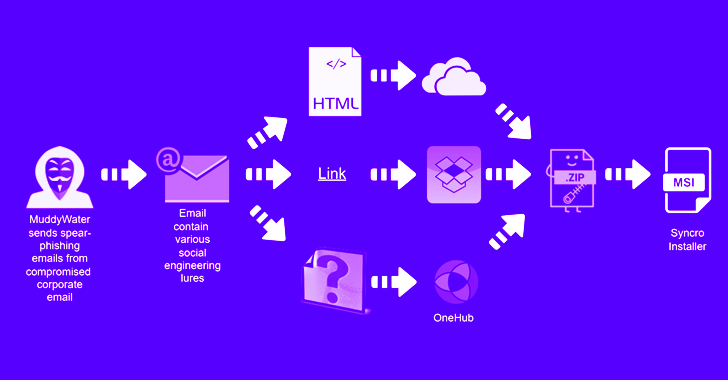
MuddyWater Hackers Target Asian and Middle East Countries with Updated Tactics
The Iran-linked MuddyWater threat actor has been observed targeting several countries in the Middle East as well as Central and West Asia as part of a new spear-phishing activity.
"The campaign has been observed targeting Armenia, Azerbaijan, Egypt, Iraq, Israel, Jordan, Oman, Qatar, Tajikistan, and the United Arab Emirates," Deep Instinct researcher Simon Kenin said in a technical write-up.
http://dlvr.it/Sf7n17
http://dlvr.it/Sf7n17
Friday, December 9, 2022
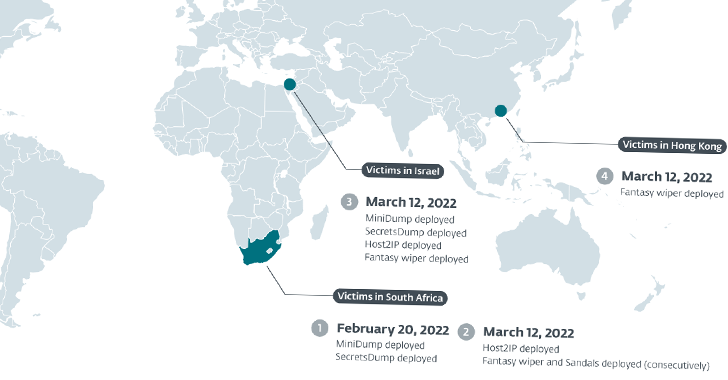
Iranian Hackers Strike Diamond Industry with Data-Wiping Malware in Supply-Chain Attack
An Iranian advanced persistent threat (APT) actor known as Agrius has been attributed as behind a set of data wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong.
The wiper, referred to as Fantasy by ESET, is believed to have been delivered via a supply-chain attack targeting an Israeli software suite developer as part of a campaign that began in February 2022.
http://dlvr.it/Sf4zJm
http://dlvr.it/Sf4zJm
Thursday, December 8, 2022
Microsoft Alerts Cryptocurrency Industry of Targeted Cyberattacks
Cryptocurrency investment companies are the target of a developing threat cluster that uses Telegram groups to seek out potential victims.
Microsoft's Security Threat Intelligence Center (MSTIC) is tracking the activity under the name DEV-0139, and builds upon a recent report from Volexity that attributed the same set of attacks to North Korea's Lazarus Group.
"DEV-0139 joined Telegram groups
http://dlvr.it/Sf21WK
http://dlvr.it/Sf21WK
Wednesday, December 7, 2022
Understanding NIST CSF to assess your organization's Ransomware readiness
Ransomware attacks keep increasing in volume and impact largely due to organizations' weak security controls. Mid-market companies are targeted as they possess a significant amount of valuable data but lack the level of protective controls and staffing of larger organizations.
According to a recent RSM survey, 62% of mid-market companies believe they are at risk of ransomware in the next 12
http://dlvr.it/SdyyLF
http://dlvr.it/SdyyLF
Telcom and BPO Companies Under Attack by SIM Swapping Hackers
A persistent intrusion campaign has set its eyes on telecommunications and business process outsourcing (BPO) companies at lease since June 2022.
"The end objective of this campaign appears to be to gain access to mobile carrier networks and, as evidenced in two investigations, perform SIM swapping activity," CrowdStrike researcher Tim Parisi said in an analysis published last week.
The
http://dlvr.it/Sdyy9D
http://dlvr.it/Sdyy9D
Tuesday, December 6, 2022
When Being Attractive Gets Risky - How Does Your Attack Surface Look to an Attacker?
In the era of digitization and ever-changing business needs, the production environment has become a living organism. Multiple functions and teams within an organization can ultimately impact the way an attacker sees the organization's assets, or in other words, the external attack surface. This dramatically increases the need to define an exposure management strategy.
To keep up with business
http://dlvr.it/Sdvwj1
http://dlvr.it/Sdvwj1
SiriusXM Vulnerability Lets Hackers Remotely Unlock and Start Connected Cars
Cybersecurity researchers have discovered a security vulnerability that exposes cars from Honda, Nissan, Infiniti, and Acura to remote attacks through a connected vehicle service provided by SiriusXM.
The issue could be exploited to unlock, start, locate, and honk any car in an unauthorized manner just by knowing the vehicle's vehicle identification number (VIN), researcher Sam Curry said in a
http://dlvr.it/SdvwZV
http://dlvr.it/SdvwZV
North Korean Hackers Spread AppleJeus Malware Disguised as Cryptocurrency Apps
The Lazarus Group threat actor has been observed leveraging fake cryptocurrency apps as a lure to deliver a previously undocumented version of the AppleJeus malware, according to new findings from Volexity.
"This activity notably involves a campaign likely targeting cryptocurrency users and organizations with a variant of the AppleJeus malware by way of malicious Microsoft Office documents,"
http://dlvr.it/SdvwQN
http://dlvr.it/SdvwQN
Critical Ping Vulnerability Allows Remote Attackers to Take Over FreeBSD Systems
The maintainers of the FreeBSD operating system have released updates to remediate a security vulnerability impacting the ping module that could be potentially exploited to crash the program or trigger remote code execution.
The issue, assigned the identifier CVE-2022-23093, impacts all supported versions of FreeBSD and concerns a stack-based buffer overflow vulnerability in the ping service.
"
http://dlvr.it/SdvwL8
http://dlvr.it/SdvwL8
Monday, December 5, 2022
Space CyberSecurity Resilience: Cyber Risk Meetups with the South Australian Space Sector - Australia Cyber Security Magazine
Space CyberSecurity Resilience: Cyber Risk Meetups with the South Australian Space Sector Australia Cyber Security Magazine
http://dlvr.it/SdrtVp
http://dlvr.it/SdrtVp
Sunday, December 4, 2022
Briefcase: REDW practice names new IT, cybersecurity director - Albuquerque Journal
Briefcase: REDW practice names new IT, cybersecurity director Albuquerque Journal
http://dlvr.it/SdpjQF
http://dlvr.it/SdpjQF
Saturday, December 3, 2022
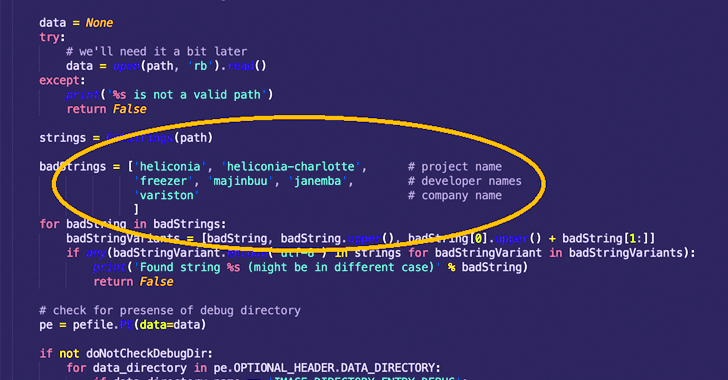
Google Accuses Spanish Spyware Vendor of Exploiting Chrome, Firefox, & Windows Zero-Days
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018.
"Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to
http://dlvr.it/SdmchG
http://dlvr.it/SdmchG
Friday, December 2, 2022
LastPass Suffers Another Security Breach; Exposed Some Customers Information
Popular password management service LastPass said it's investigating a second security incident that involved attackers accessing some of its customer information.
"We recently detected unusual activity within a third-party cloud storage service, which is currently shared by both LastPass and its a...
http://dlvr.it/Sdjm8k
http://dlvr.it/Sdjm8k
Thursday, December 1, 2022
CITE 2022: Overcome Common Cybersecurity Challenges and Prepare for 2023's Growing Threats - EdTech Magazine: Focus on K-12
CITE 2022: Overcome Common Cybersecurity Challenges and Prepare for 2023's Growing Threats EdTech Magazine: Focus on K-12
http://dlvr.it/SdfhFS
http://dlvr.it/SdfhFS
Wednesday, November 30, 2022
Irish Regulator Fines Facebook $277 Million for Leak of Half a Billion Users' Data
Ireland's Data Protection Commission (DPC) has levied fines of €265 million ($277 million) against Meta Platforms for failing to safeguard the personal data of more than half a billion users of its Facebook service, ramping up privacy enforcement against U.S. tech firms.
The fines follow an inquiry initiated by the European regulator on April 14, 2021, close on the heels of a leak of a "collated
http://dlvr.it/SdbXVJ
http://dlvr.it/SdbXVJ
Tuesday, November 29, 2022
The 5 Cornerstones for an Effective Cyber Security Awareness Training
It's not news that phishing attacks are getting more complex and happening more often. This year alone, APWG reported a record-breaking total of 1,097,811 phishing attacks. These attacks continue to target organizations and individuals to gain their sensitive information.
The hard news: they're often successful, have a long-lasting negative impact on your organization and employees, including:
http://dlvr.it/SdXQ99
http://dlvr.it/SdXQ99
Over a Dozen New BMC Firmware Flaws Expose OT and IoT Devices to Remote Attacks
Over a dozen security flaws have been discovered in baseboard management controller (BMC) firmware from Lanner that could expose operational technology (OT) and internet of things (IoT) networks to remote attacks.
BMC refers to a specialized service processor, a system-on-chip (SoC), that's found in server motherboards and is used for remote monitoring and management of a host system, including
http://dlvr.it/SdXPvs
http://dlvr.it/SdXPvs
Monday, November 28, 2022
Elon Musk Confirms Twitter 2.0 will Bring End-to-End Encryption to Direct Messages
Twitter chief executive Elon Musk confirmed plans for end-to-end encryption (E2EE) for direct messages on the platform.
The feature is part of Musk's vision for Twitter 2.0, which is expected to be what's called an "everything app." Other functionalities include longform tweets and payments, according to a slide deck shared by Musk over the weekend.
The company's plans for
http://dlvr.it/SdTM5f
http://dlvr.it/SdTM5f
Sunday, November 27, 2022
Cybersecurity Investments in the EU: Is the Money Enough to Meet the New Cybersecurity Standards? - ENISA
Cybersecurity Investments in the EU: Is the Money Enough to Meet the New Cybersecurity Standards? ENISA
http://dlvr.it/SdR6FF
http://dlvr.it/SdR6FF
All You Need to Know About Emotet in 2022
For 6 months, the infamous Emotet botnet has shown almost no activity, and now it's distributing malicious spam. Let's dive into details and discuss all you need to know about the notorious malware to combat it.
Why is everyone scared of Emotet?
Emotet is by far one of the most dangerous trojans ever created. The malware became a very destructive program as it grew in scale and sophistication.
http://dlvr.it/SdR5vP
http://dlvr.it/SdR5vP
Subscribe to:
Posts (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...