MinterEllison leans on AI in cyber security ops CRN Australia
http://dlvr.it/Sy9sWl
Tuesday, October 31, 2023
Monday, October 30, 2023
Hackers Using MSIX App Packages to Infect Windows PCs with GHOSTPULSE Maware
A new cyber attack campaign has been observed using spurious MSIX Windows app package files for popular software such as Google Chrome, Microsoft Edge, Brave, Grammarly, and Cisco Webex to distribute a novel malware loader dubbed GHOSTPULSE.
"MSIX is a Windows app package format that developers can leverage to package, distribute, and install their applications to Windows users," Elastic
http://dlvr.it/Sy7KGx
"MSIX is a Windows app package format that developers can leverage to package, distribute, and install their applications to Windows users," Elastic
http://dlvr.it/Sy7KGx
Sunday, October 29, 2023
Google Expands Its Bug Bounty Program to Tackle Artificial Intelligence Threats
Google has announced that it's expanding its Vulnerability Rewards Program (VRP) to compensate researchers for finding attack scenarios tailored to generative artificial intelligence (AI) systems in an effort to bolster AI safety and security.
"Generative AI raises new and different concerns than traditional digital security, such as the potential for unfair bias, model manipulation or
http://dlvr.it/Sy5WCY
"Generative AI raises new and different concerns than traditional digital security, such as the potential for unfair bias, model manipulation or
http://dlvr.it/Sy5WCY
Saturday, October 28, 2023
CISA targets software identification in push to boost supply chain ... - Cybersecurity Dive
CISA targets software identification in push to boost supply chain ... Cybersecurity Dive
http://dlvr.it/Sy3mh6
http://dlvr.it/Sy3mh6
Friday, October 27, 2023
Thursday, October 26, 2023
Continued cybersecurity woes plague Clark County School District amid leaked student data fears - News3LV
Continued cybersecurity woes plague Clark County School District amid leaked student data fears News3LV
http://dlvr.it/SxymhH
http://dlvr.it/SxymhH
Taumata Rau Conversation pushes cybersecurity up the agenda - The University of Auckland
Taumata Rau Conversation pushes cybersecurity up the agenda The University of Auckland
http://dlvr.it/SxymPp
http://dlvr.it/SxymPp
Wednesday, October 25, 2023
Backdoor Implanted on Hacked Cisco Devices Modified to Evade Detection
The backdoor implanted on Cisco devices by exploiting a pair of zero-day flaws in IOS XE software has been modified by the threat actor so as to escape visibility via previous fingerprinting methods.
"Investigated network traffic to a compromised device has shown that the threat actor has upgraded the implant to do an extra header check," NCC Group's Fox-IT team said. "Thus, for a lot of devices
http://dlvr.it/Sxw6VX
"Investigated network traffic to a compromised device has shown that the threat actor has upgraded the implant to do an extra header check," NCC Group's Fox-IT team said. "Thus, for a lot of devices
http://dlvr.it/Sxw6VX
Tuesday, October 24, 2023
Mohamed El Guindy | Global Initiative - Global Initiative Against Transnational Organized Crime
Mohamed El Guindy | Global Initiative Global Initiative Against Transnational Organized Crime
http://dlvr.it/SxsSPK
http://dlvr.it/SxsSPK
Monday, October 23, 2023
Chambersburg School District releases update on August cyber-attack - WPMT FOX 43
Chambersburg School District releases update on August cyber-attack WPMT FOX 43
http://dlvr.it/SxpwpC
http://dlvr.it/SxpwpC
Sunday, October 22, 2023
International Criminal Court heightens security after espionage cyber-attack - ETTelecom
International Criminal Court heightens security after espionage cyber-attack ETTelecom
http://dlvr.it/Sxn3V4
http://dlvr.it/Sxn3V4
Saturday, October 21, 2023
Cybersecurity risks continue to grow for municipalities, school districts - The Derby Informer
Cybersecurity risks continue to grow for municipalities, school districts The Derby Informer
http://dlvr.it/SxlFkV
http://dlvr.it/SxlFkV
Friday, October 20, 2023
Iran-Linked OilRig Targets Middle East Governments in 8-Month Cyber Campaign
The Iran-linked OilRig threat actor targeted an unnamed Middle East government between February and September 2023 as part of an eight-month-long campaign.
The attack led to the theft of files and passwords and, in one instance, resulted in the deployment of a PowerShell backdoor called PowerExchange, the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News
http://dlvr.it/SxhnBG
The attack led to the theft of files and passwords and, in one instance, resulted in the deployment of a PowerShell backdoor called PowerExchange, the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News
http://dlvr.it/SxhnBG
Microsoft Warns of North Korean Attacks Exploiting JetBrains TeamCity Flaw
North Korean threat actors are actively exploiting a critical security flaw in JetBrains TeamCity to opportunistically breach vulnerable servers, according to Microsoft.
The attacks, which entail the exploitation of CVE-2023-42793 (CVSS score: 9.8), have been attributed to Diamond Sleet (aka Labyrinth Chollima) and Onyx Sleet (aka Andariel or Silent Chollima).
It's worth noting that both the
http://dlvr.it/Sxhn1K
The attacks, which entail the exploitation of CVE-2023-42793 (CVSS score: 9.8), have been attributed to Diamond Sleet (aka Labyrinth Chollima) and Onyx Sleet (aka Andariel or Silent Chollima).
It's worth noting that both the
http://dlvr.it/Sxhn1K
Thursday, October 19, 2023
New Admin Takeover Vulnerability Exposed in Synology's DiskStation Manager
A medium-severity flaw has been discovered in Synology's DiskStation Manager (DSM) that could be exploited to decipher an administrator's password and remotely hijack the account.
"Under some rare conditions, an attacker could leak enough information to restore the seed of the pseudorandom number generator (PRNG), reconstruct the admin password, and remotely take over the admin account,"
http://dlvr.it/SxfBlj
"Under some rare conditions, an attacker could leak enough information to restore the seed of the pseudorandom number generator (PRNG), reconstruct the admin password, and remotely take over the admin account,"
http://dlvr.it/SxfBlj
Wednesday, October 18, 2023
The curious role of artificial intelligence in building cyber security structures - The Financial Express
The curious role of artificial intelligence in building cyber security structures The Financial Express
http://dlvr.it/SxbbRM
http://dlvr.it/SxbbRM
Tuesday, October 17, 2023
Julie Collins pledges to work with SMEs on data and cyber security - SmartCompany
Julie Collins pledges to work with SMEs on data and cyber security SmartCompany
http://dlvr.it/SxXzwt
http://dlvr.it/SxXzwt
Monday, October 16, 2023
Sunday, October 15, 2023
FBI, CISA Warn of Rising AvosLocker Ransomware Attacks Against Critical Infrastructure
The AvosLocker ransomware gang has been linked to attacks against critical infrastructure sectors in the U.S., with some of them detected as recently as May 2023.
That's according to a new joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-service (RaaS) operation's
http://dlvr.it/SxSXNJ
That's according to a new joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-service (RaaS) operation's
http://dlvr.it/SxSXNJ
Saturday, October 14, 2023
Springfield cybersecurity center will be ‘teaching hospital for cyber’ - MassLive.com
Springfield cybersecurity center will be ‘teaching hospital for cyber’ MassLive.com
http://dlvr.it/SxQj9q
http://dlvr.it/SxQj9q
Friday, October 13, 2023
Researchers Uncover Malware Posing as WordPress Caching Plugin
Cybersecurity researchers have shed light on a new sophisticated strain of malware that masquerades a WordPress plugin to stealthily create administrator accounts and remotely control a compromised site.
"Complete with a professional looking opening comment implying it is a caching plugin, this rogue code contains numerous functions, adds filters to prevent itself from being included in the list
http://dlvr.it/SxNJXb
"Complete with a professional looking opening comment implying it is a caching plugin, this rogue code contains numerous functions, adds filters to prevent itself from being included in the list
http://dlvr.it/SxNJXb
Thursday, October 12, 2023
CISA Warns of Actively Exploited Adobe Acrobat Reader Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a high-severity flaw in Adobe Acrobat Reader to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
Tracked as CVE-2023-21608 (CVSS score: 7.8), the vulnerability has been described as a use-after-free bug that can be exploited to achieve remote code execution (RCE) with the
http://dlvr.it/SxKjq2
Tracked as CVE-2023-21608 (CVSS score: 7.8), the vulnerability has been described as a use-after-free bug that can be exploited to achieve remote code execution (RCE) with the
http://dlvr.it/SxKjq2
Take an Offensive Approach to Password Security by Continuously Monitoring for Breached Passwords
Passwords are at the core of securing access to an organization's data. However, they also come with security vulnerabilities that stem from their inconvenience. With a growing list of credentials to keep track of, the average end-user can default to shortcuts. Instead of creating a strong and unique password for each account, they resort to easy-to-remember passwords, or use the same password
http://dlvr.it/SxKjfC
http://dlvr.it/SxKjfC
Wednesday, October 11, 2023
Telstra International strengthens global managed cyber security ... - PR Newswire Asia
Telstra International strengthens global managed cyber security ... PR Newswire Asia
http://dlvr.it/SxH78L
http://dlvr.it/SxH78L
Tuesday, October 10, 2023
Monday, October 9, 2023
Gaza-Linked Cyber Threat Actor Targets Israeli Energy and Defense Sectors
A Gaza-based threat actor has been linked to a series of cyber attacks aimed at Israeli private-sector energy, defense, and telecommunications organizations.
Microsoft, which revealed details of the activity in its fourth annual Digital Defense Report, is tracking the campaign under the name Storm-1133.
"We assess this group works to further the interests of Hamas, a Sunni militant group that is
http://dlvr.it/SxB1jY
Microsoft, which revealed details of the activity in its fourth annual Digital Defense Report, is tracking the campaign under the name Storm-1133.
"We assess this group works to further the interests of Hamas, a Sunni militant group that is
http://dlvr.it/SxB1jY
Sunday, October 8, 2023
Territorial Army hires Chinese language interpreters, to induct cyber security experts next - The Indian Express
Territorial Army hires Chinese language interpreters, to induct cyber security experts next The Indian Express
http://dlvr.it/Sx8DTY
http://dlvr.it/Sx8DTY
Beefing up cybersecurity for India’s energy transition - Observer Research Foundation
Beefing up cybersecurity for India’s energy transition Observer Research Foundation
http://dlvr.it/Sx8DHj
http://dlvr.it/Sx8DHj
Saturday, October 7, 2023
GitHub's Secret Scanning Feature Now Covers AWS, Microsoft, Google, and Slack
GitHub has announced an improvement to its secret scanning feature that extends validity checks to popular services such as Amazon Web Services (AWS), Microsoft, Google, and Slack.
Validity checks, introduced by the Microsoft subsidiary earlier this year, alert users whether exposed tokens found by secret scanning are active, thereby allowing for effective remediation measures. It was first
http://dlvr.it/Sx6SQR
Validity checks, introduced by the Microsoft subsidiary earlier this year, alert users whether exposed tokens found by secret scanning are active, thereby allowing for effective remediation measures. It was first
http://dlvr.it/Sx6SQR
Friday, October 6, 2023
2023-10-05 | NDAQ:HUBC | Press Release | Hub Cyber Security Ltd - Stockhouse Publishing
2023-10-05 | NDAQ:HUBC | Press Release | Hub Cyber Security Ltd Stockhouse Publishing
http://dlvr.it/Sx44kM
http://dlvr.it/Sx44kM
Thursday, October 5, 2023
Looney Tunables: New Linux Flaw Enables Privilege Escalation on Major Distributions
A new Linux security vulnerability dubbed Looney Tunables has been discovered in the GNU C library's ld.so dynamic loader that, if successfully exploited, could lead to a local privilege escalation and allow a threat actor to gain root privileges.
Tracked as CVE-2023-4911 (CVSS score: 7.8), the issue is a buffer overflow that resides in the dynamic loader's processing of the GLIBC_TUNABLES
http://dlvr.it/Sx1XZ4
Tracked as CVE-2023-4911 (CVSS score: 7.8), the issue is a buffer overflow that resides in the dynamic loader's processing of the GLIBC_TUNABLES
http://dlvr.it/Sx1XZ4
Wednesday, October 4, 2023
Over 3 Dozen Data-Stealing Malicious npm Packages Found Targeting Developers
Nearly three dozen counterfeit packages have been discovered in the npm package repository that are designed to exfiltrate sensitive data from developer systems, according to findings from Fortinet FortiGuard Labs.
One set of packages – named @expue/webpack, @expue/core, @expue/vue3-renderer, @fixedwidthtable/fixedwidthtable, and @virtualsearchtable/virtualsearchtable – harbored an obfuscated
http://dlvr.it/Swyw2V
One set of packages – named @expue/webpack, @expue/core, @expue/vue3-renderer, @fixedwidthtable/fixedwidthtable, and @virtualsearchtable/virtualsearchtable – harbored an obfuscated
http://dlvr.it/Swyw2V
API Security Trends 2023 – Have Organizations Improved their Security Posture?
APIs, also known as application programming interfaces, serve as the backbone of modern software applications, enabling seamless communication and data exchange between different systems and platforms. They provide developers with an interface to interact with external services, allowing them to integrate various functionalities into their own applications.
However, this increased reliance on
http://dlvr.it/SwyvmY
However, this increased reliance on
http://dlvr.it/SwyvmY
Protecting your IT infrastructure with Security Configuration Assessment (SCA)
Security Configuration Assessment (SCA) is critical to an organization's cybersecurity strategy. SCA aims to discover vulnerabilities and misconfigurations that malicious actors exploit to gain unauthorized access to systems and data. Regular security configuration assessments are essential in maintaining a secure and compliant environment, as this minimizes the risk of cyber attacks. The
http://dlvr.it/Swyvdd
http://dlvr.it/Swyvdd
Researcher Reveals New Techniques to Bypass Cloudflare's Firewall and DDoS Protection
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of these safeguards, it has emerged.
"Attackers can utilize their own Cloudflare accounts to abuse the per-design trust-relationship between Cloudflare and the customers' websites, rendering the
http://dlvr.it/SwyvWq
"Attackers can utilize their own Cloudflare accounts to abuse the per-design trust-relationship between Cloudflare and the customers' websites, rendering the
http://dlvr.it/SwyvWq
Tuesday, October 3, 2023
LUCR-3: Scattered Spider Getting SaaS-y in the Cloud
LUCR-3 overlaps with groups such as Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated attacker that leverages the Identity Provider (IDP) as initial access into an environment with the goal of stealing Intellectual Property (IP) for extortion. LUCR-3 targets Fortune 2000 companies across various sectors, including but not limited to Software, Retail, Hospitality,
http://dlvr.it/SwwL4N
http://dlvr.it/SwwL4N
Silent Skimmer: A Year-Long Web Skimming Campaign Targeting Online Payment Businesses
A financially motivated campaign has been targeting online payment businesses in the Asia Pacific, North America, and Latin America with web skimmers for more than a year.
The BlackBerry Research and Intelligence Team is tracking the activity under the name Silent Skimmer, attributing it to an actor who is knowledgeable in the Chinese language. Prominent victims include online businesses and
http://dlvr.it/SwwKvL
The BlackBerry Research and Intelligence Team is tracking the activity under the name Silent Skimmer, attributing it to an actor who is knowledgeable in the Chinese language. Prominent victims include online businesses and
http://dlvr.it/SwwKvL
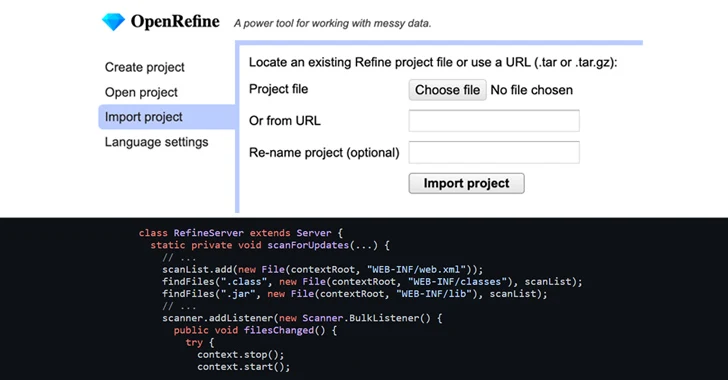
OpenRefine's Zip Slip Vulnerability Could Let Attackers Execute Malicious Code
A high-severity security flaw has been disclosed in the open-source OpenRefine data cleanup and transformation tool that could result in arbitrary code execution on affected systems.
Tracked as CVE-2023-37476 (CVSS score: 7.8), the vulnerability is a Zip Slip vulnerability that could have adverse impacts when importing a specially crafted project in versions 3.7.3 and below.
"Although OpenRefine
http://dlvr.it/SwwKpd
Tracked as CVE-2023-37476 (CVSS score: 7.8), the vulnerability is a Zip Slip vulnerability that could have adverse impacts when importing a specially crafted project in versions 3.7.3 and below.
"Although OpenRefine
http://dlvr.it/SwwKpd
Monday, October 2, 2023
Sunday, October 1, 2023
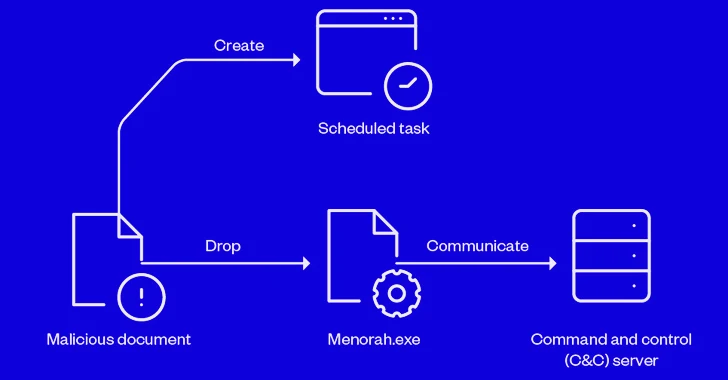
Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims with a new strain of malware called Menorah.
"The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or malware," Trend Micro researchers Mohamed Fahmy and Mahmoud Zohdy
http://dlvr.it/SwqymR
"The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another file or malware," Trend Micro researchers Mohamed Fahmy and Mahmoud Zohdy
http://dlvr.it/SwqymR
Subscribe to:
Posts (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...