Monday, February 28, 2022
CVE-2022-25255
http://dlvr.it/SKqs8p
TCS' Cyber Defense Suite PaaS offers integrated security to enterprises - CSO Online
http://dlvr.it/SKqVVx
Cyber Security Testing, Inspection and Certification Market is Booming Worldwide with Bureau Veritas, DNV GL – corporate ethos - corporate ethos
http://dlvr.it/SKq3Xc
Rosenworcel Concerned About Cybersecurity, BGP Vulnerability Amid Ukraine Conflict - Telecompetitor
http://dlvr.it/SKpWcb
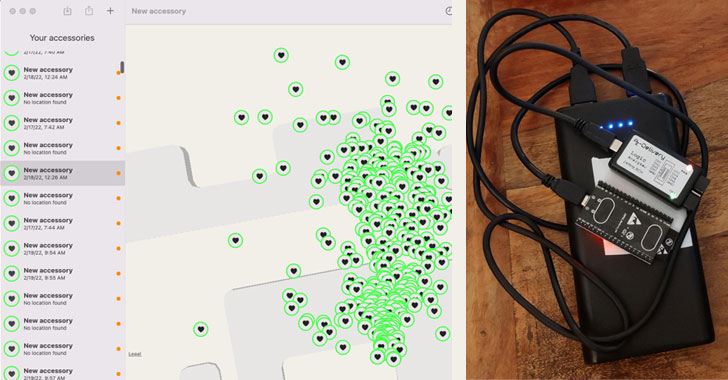
Experts Create Apple AirTag Clone That Can Bypass Anti-Tracking Measures
http://dlvr.it/SKpWBD
Sunday, February 27, 2022
Anonymous Claims Hacks on More Than 300 Russian Cyber Targets in 48 Hours, Including Gas Control System - HS Today - HSToday
http://dlvr.it/SKmXrK
Want to boost your cybersecurity? Here are 10 steps to improve your defences now - ZDNet
http://dlvr.it/SKmFz4
Week in review: Cyber attacks on Ukraine, Help Net Security: Healthcare Cybersecurity Report is out - Help Net Security
http://dlvr.it/SKlYTG
Saturday, February 26, 2022
Russia-Ukraine War: Phishing, Malware and Hacker Groups Taking Sides
http://dlvr.it/SKj7b4
Friday, February 25, 2022
CVE-2022-25235
http://dlvr.it/SKgYNn
Anonymous Hackers Launch Cyber Ops Against Russia, Claim Government Site Takedowns - HS Today - HSToday
http://dlvr.it/SKgB2h
Barracuda Cybersecurity Update, Russian Cyber Threats, Cloudflare M&A - Channel Futures
http://dlvr.it/SKfjs6
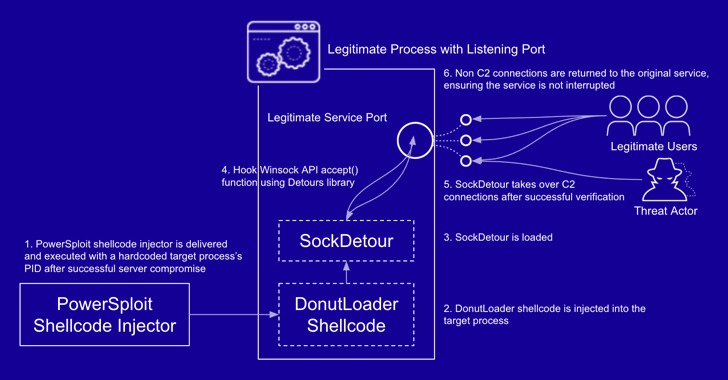
New "SockDetour" Fileless, Socketless Backdoor Targets U.S. Defense Contractors
http://dlvr.it/SKfhww
New Flaws Discovered in Cisco's Network Operating System for Switches
http://dlvr.it/SKf9TN
Thursday, February 24, 2022
CVE-2022-24977
http://dlvr.it/SKc7NB
Cyber Security in Healthcare Market Recovery and Impact Analysis Report – Trend Micro Incorporated, Booz Allen Hamilton, Northrop Grumman Corporation – ZNews Africa - ZNews Africa
http://dlvr.it/SKZhmy
CVE-2022-24646
http://dlvr.it/SKZhjm
25 Malicious JavaScript Libraries Distributed via Official NPM Package Repository
http://dlvr.it/SKZhQT
Friday, February 4, 2022
YOUR SOLUTION TO OFFENSIVE CYBER SECURITY
YOUR SOLUTION TO OFFENSIVE CYBER SECURITY
ReconZ Consulting is a Cyber Security firm specialized in Security Posture Assessment (SPA) / Penetration testing and IT technologies. We provide professional yet cost-effective IT security services and solution. Test with us now and secure your data.
Our job scope covers:
1) Security Posture Assessment (SPA):
* Network Penetration Testing
* Website Penetration Testing
* Mobile Penetration Testing
* IoT Penetration Testing
* Wireless Assessment
* Thick Client Assessment
* Social Engineering
* Source Code Review
* Hose Client Assessment
* Vulnerability Assessment (VA)
* Network Device Review
* WAF Security Audit
* Incident Response and Log Analysis
2)Cyber Security Policy:
* ISMS Cyber Security policy
* ReconZ Cyber Security Policy
3)Cyber Security Training:
* Cyber Security Awareness Training
* SPA Training
4)Others Services :
* Wifi Hotspot Solution
* Web Development
* Software and Apps Development
* Stress Test
* Performance Test
* Intrution Detection Solution
Contact : 03-33100104(Office)
+601124057305(Call/Whatsapp)
Email: samir@reconz.my
Website: https://www.reconz.my
#iot
#cybersecuritytraining
#digitalforensic
#network
#socialengineering
#penetrationtesting
#networkpentest
#IoTpentest
#computer
#SPA
#cybersecurity
#hacking
#websitepentest
#mobilepentest
#securitypostureassessment
#sourcecodereview
#itsecurity
#cybersecuritycompanymalaysia
#pentest
Thursday, February 3, 2022
Hackers Exploited 0-Day Vulnerability in Zimbra Email Platform to Spy on Users
http://dlvr.it/SJMCx3
Axio Joins with Cyber Risk Institute to Deliver Cybersecurity Resilience to Financial Services Institutions Across the Globe - Yahoo Finance
http://dlvr.it/SJKpQb
Critical Flaws Discovered in Cisco Small Business RV Series Routers
http://dlvr.it/SJKFPc
New Variant of UpdateAgent Malware Infects Mac Computers with Adware
http://dlvr.it/SJJhBJ
New Wave of Cyber Attacks Target Palestine with Political Bait and Malware
http://dlvr.it/SJJ9hc
Wednesday, February 2, 2022
CVE-2022-23967
http://dlvr.it/SJHm0t
Check out Episode 9 of The Cybersecurity and Geopolitical Podcast — Russia: The Global Protagonist - Security Magazine
http://dlvr.it/SJGKCd
New Malware Used by SolarWinds Attackers Went Undetected for Years
http://dlvr.it/SJFn0w
Cynet's Keys to Extend Threat Visibility
http://dlvr.it/SJFCLK
Hacker Group 'Moses Staff' Using New StrifeWater RAT in Ransomware Attacks
http://dlvr.it/SJDjs0
Tuesday, February 1, 2022
Critical Bug Found in WordPress Plugin for Elementor with Over a Million Installations
http://dlvr.it/SJDJfV
“Effect of cyber attack on Gold Bond will last for weeks,” warns expert | Ctech - CTech
http://dlvr.it/SJBw2w
German petrol supply firm Oiltanking paralyzed by cyber attack - BleepingComputer
http://dlvr.it/SJBNm6
Cyber Security, Senior Associate job with The MIL Corporation (MIL) | 43480037 - The Washington Post
http://dlvr.it/SJ9qq8
Reasons Why Every Business is a Target of DDoS Attacks
http://dlvr.it/SJ9L91
Columbus won't explain critical cyber service outage hampering 311 for days - The Columbus Dispatch
Columbus won't explain critical cyber service outage hampering 311 for days The Columbus Dispatch http://dlvr.it/TB6t50
-
A cyberespionage group with ties to North Korea has resurfaced with a stealthier variant of its remote access trojan called Konni to attack ...
-
Laravel 9.1.8, when processing attacker-controlled data for deserialization, allows Remote Code Execution via an unserialize pop chain in __...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...

















.jpg?height=635&t=1643748762&width=1200)