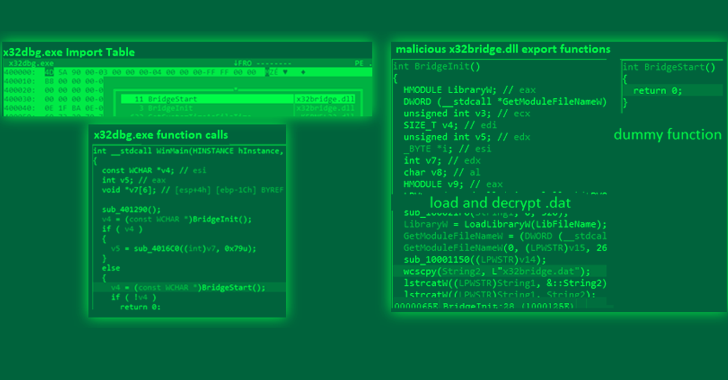
The PlugX remote access trojan has been observed masquerading as an open source Windows debugger tool called x64dbg in an attempt to circumvent security protections and gain control of a target system.
"This file is a legitimate open-source debugger tool for Windows that is generally used to examine kernel-mode and user-mode code, crash dumps, or CPU registers," Trend Micro researchers Buddy
http://dlvr.it/Sk6VVr
Tuesday, February 28, 2023
Monday, February 27, 2023
Dutch Police Arrest 3 Hackers Involved in Massive Data Theft and Extortion Scheme
The Dutch police announced the arrest of three individuals in connection with a "large-scale" criminal operation involving data theft, extortion, and money laundering.
The suspects include two 21-year-old men from Zandvoort and Rotterdam and an 18-year-old man without a permanent residence. The arrests were made on January 23, 2023.
It's estimated that the hackers stole personal data belonging
http://dlvr.it/Sk3ZR3
http://dlvr.it/Sk3ZR3
Sunday, February 26, 2023
Palo Alto Networks Is the Leading Cyber Security Play - Investing.com
Palo Alto Networks Is the Leading Cyber Security Play Investing.com
http://dlvr.it/Sk1Q2s
http://dlvr.it/Sk1Q2s
Saturday, February 25, 2023
Some Indigo employee data was stolen in ransomware attack, retailer now says - CBC News
Some Indigo employee data was stolen in ransomware attack, retailer now says CBC News
http://dlvr.it/SjzD2q
http://dlvr.it/SjzD2q
Friday, February 24, 2023
SSU alumnus launches career in cybersecurity - The Highland County Press
SSU alumnus launches career in cybersecurity The Highland County Press
http://dlvr.it/SjwK4q
http://dlvr.it/SjwK4q
Thursday, February 23, 2023
Hydrochasma: New Threat Actor Targets Shipping Companies and Medical Labs in Asia
Shipping companies and medical laboratories in Asia have been the subject of a suspected espionage campaign carried out by a never-before-seen threat actor dubbed Hydrochasma.
The activity, which has been ongoing since October 2022, "relies exclusively on publicly available and living-off-the-land tools," Symantec, by Broadcom Software, said in a report shared with The Hacker News.
There is no
http://dlvr.it/SjsCSR
http://dlvr.it/SjsCSR
Wednesday, February 22, 2023
Election, cybersecurity officials warn about foreign threats ahead of 2024 - KTAR.com
Election, cybersecurity officials warn about foreign threats ahead of 2024 KTAR.com
http://dlvr.it/Sjp6p9
http://dlvr.it/Sjp6p9
Tuesday, February 21, 2023
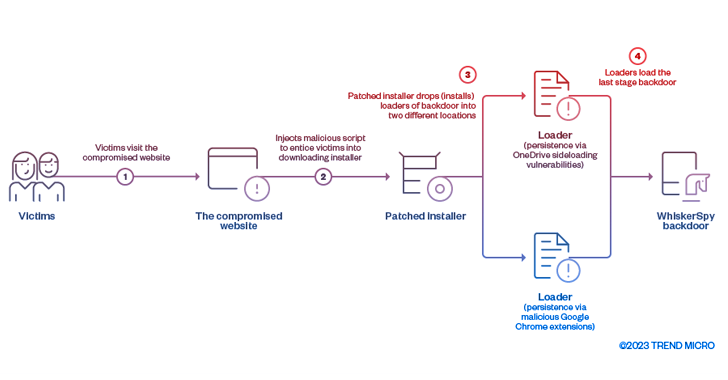
Cyber Espionage Group Earth Kitsune Deploys WhiskerSpy Backdoor in Latest Attacks
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign.
Earth Kitsune, active since at least 2019, is known to primarily target individuals interested in North Korea with self-developed malware such as dneSpy and agfSpy. Previously documented intrusions have entailed the use of watering holes
http://dlvr.it/Sjl4y6
http://dlvr.it/Sjl4y6
Monday, February 20, 2023
Cyber security breaches are up multiple times as Internet penetration grows - Business Standard
Cyber security breaches are up multiple times as Internet penetration grows Business Standard
http://dlvr.it/SjhF0x
http://dlvr.it/SjhF0x
Samsung Introduces New Feature to Protect Users from Zero-Click Malware Attacks
Samsung has announced a new feature called Message Guard that comes with safeguards to protect users from malware and spyware via what's referred to as zero-click attacks.
The South Korean chaebol said the solution "preemptively" secures users' devices by "limiting exposure to invisible threats disguised as image attachments."
The security feature, available on Samsung Messages and Google
http://dlvr.it/SjhDZs
http://dlvr.it/SjhDZs
Sunday, February 19, 2023
GoDaddy Discloses Multi-Year Security Breach Causing Malware Installations and Source Code Theft
Web hosting services provider GoDaddy on Friday disclosed a multi-year security breach that enabled unknown threat actors to install malware and siphon source code related to some of its services.
The company attributed the campaign to a "sophisticated and organized group targeting hosting services."
GoDaddy said in December 2022, it received an unspecified number of customer complaints about
http://dlvr.it/Sjf74z
http://dlvr.it/Sjf74z
Saturday, February 18, 2023
New Mirai Botnet Variant 'V3G4' Exploiting 13 Flaws to Target Linux and IoT Devices
A new variant of the notorious Mirai botnet has been found leveraging several security vulnerabilities to propagate itself to Linux and IoT devices.
Observed during the second half of 2022, the new version has been dubbed V3G4 by Palo Alto Networks Unit 42, which identified three different campaigns likely conducted by the same threat actor.
"Once the vulnerable devices are compromised, they
http://dlvr.it/Sjc5PF
http://dlvr.it/Sjc5PF
Friday, February 17, 2023
CAGS students impress in national cyber security competition - Shepparton News
CAGS students impress in national cyber security competition Shepparton News
http://dlvr.it/SjYPbP
http://dlvr.it/SjYPbP
Thursday, February 16, 2023
Cyber security for telecom - Pakistan Observer
Cyber security for telecom Pakistan Observer
http://dlvr.it/SjVSPn
http://dlvr.it/SjVSPn
Wednesday, February 15, 2023
Hackers Create Malicious Dota 2 Game Modes to Secretly Access Players' Systems
An unknown threat actor created malicious game modes for the Dota 2 multiplayer online battle arena (MOBA) video game that could have been exploited to establish backdoor access to players' systems.
The modes exploited a high-severity flaw in the V8 JavaScript engine tracked as CVE-2021-38003 (CVSS score: 8.8), which was exploited as a zero-day and addressed by Google in October 2021.
"Since V8
http://dlvr.it/SjRWpW
http://dlvr.it/SjRWpW
Tuesday, February 14, 2023
Philadelphia Orchestra, Kimmel Center ticketing systems remain hampered after cyber attack - The Philadelphia Inquirer
Philadelphia Orchestra, Kimmel Center ticketing systems remain hampered after cyber attack The Philadelphia Inquirer
http://dlvr.it/SjNdSd
http://dlvr.it/SjNdSd
Monday, February 13, 2023
Chinese Tonto Team Hackers' Second Attempt to Target Cybersecurity Firm Group-IB Fails
The advanced persistent threat (APT) actor known as Tonto Team carried out an unsuccessful attack on cybersecurity company Group-IB in June 2022.
The Singapore-headquartered firm said that it detected and blocked malicious phishing emails originating from the group targeting its employees. It's also the second attack aimed at Group-IB, the first of which took place in March 2021.
Tonto Team,
http://dlvr.it/SjL9Nf
http://dlvr.it/SjL9Nf
Hackers Targeting U.S. and German Firms Monitor Victims' Desktops with Screenshotter
A previously unknown threat actor has been targeting companies in the U.S. and Germany with bespoke malware designed to steal confidential information.
Enterprise security company Proofpoint, which is tracking the activity cluster under the name Screentime, said the group, dubbed TA866, is likely financially motivated.
"TA866 is an organized actor able to perform well thought-out attacks at
http://dlvr.it/SjKpHk
http://dlvr.it/SjKpHk
Sunday, February 12, 2023
Enigma, Vector, and TgToxic: The New Threats to Cryptocurrency Users
Suspected Russian threat actors have been targeting Eastern European users in the crypto industry with fake job opportunities as bait to install information-stealing malware on compromised hosts.
The attackers "use several highly obfuscated and under-development custom loaders in order to infect those involved in the cryptocurrency industry with Enigma stealer," Trend Micro researchers Aliakbar
http://dlvr.it/SjHp1P
http://dlvr.it/SjHp1P
Saturday, February 11, 2023
U.K. and U.S. Sanction 7 Russians for TrickBot, Ryuk, and Conti Ransomware Attacks
In a first-of-its-kind coordinated action, the U.K. and U.S. governments on Thursday levied sanctions against seven Russian nationals for their affiliation to the TrickBot, Ryuk, and Conti cybercrime operation.
The individuals designated under sanctions are Vitaly Kovalev (aka Alex Konor, Bentley, or Bergen), Maksim Mikhailov (aka Baget), Valentin Karyagin (aka Globus), Mikhail Iskritskiy (aka
http://dlvr.it/SjFrsj
http://dlvr.it/SjFrsj
Friday, February 10, 2023
OpenSSL Fixes Multiple New Security Flaws with Latest Update
The OpenSSL Project has released fixes to address several security flaws, including a high-severity bug in the open source encryption toolkit that could potentially expose users to malicious attacks.
Tracked as CVE-2023-0286, the issue relates to a case of type confusion that may permit an adversary to "read memory contents or enact a denial-of-service," the maintainers said in an advisory.
The
http://dlvr.it/SjCFdv
http://dlvr.it/SjCFdv
Thursday, February 9, 2023
(ISC)² Makes Certified in Cybersecurity Exam Available in More ... - Dark Reading
(ISC)² Makes Certified in Cybersecurity Exam Available in More ... Dark Reading
http://dlvr.it/Sj8XYK
http://dlvr.it/Sj8XYK
Wednesday, February 8, 2023
VMware Finds No Evidence of 0-Day in Ongoing ESXiArgs Ransomware Spree
VMware on Monday said it found no evidence that threat actors are leveraging an unknown security flaw, i.e., a zero-day, in its software as part of an ongoing ransomware attack spree worldwide.
"Most reports state that End of General Support (EoGS) and/or significantly out-of-date products are being targeted with known vulnerabilities which were previously addressed and disclosed in VMware
http://dlvr.it/Sj5pF0
http://dlvr.it/Sj5pF0
Tuesday, February 7, 2023
OpenSSH Releases Patch for New Pre-Auth Double Free Vulnerability
The maintainers of OpenSSH have released OpenSSH 9.2 to address a number of security bugs, including a memory safety vulnerability in the OpenSSH server (sshd).
Tracked as CVE-2023-25136, the shortcoming has been classified as a pre-authentication double free vulnerability that was introduced in version 9.1.
"This is not believed to be exploitable, and it occurs in the unprivileged pre-auth
http://dlvr.it/Sj31sD
http://dlvr.it/Sj31sD
FormBook Malware Spreads via Malvertising Using MalVirt Loader to Evade Detection
An ongoing malvertising campaign is being used to distribute virtualized .NET loaders that are designed to deploy the FormBook information-stealing malware.
"The loaders, dubbed MalVirt, use obfuscated virtualization for anti-analysis and evasion along with the Windows Process Explorer driver for terminating processes," SentinelOne researchers Aleksandar Milenkoski and Tom Hegel said in a
http://dlvr.it/Sj31ct
http://dlvr.it/Sj31ct
Monday, February 6, 2023
NFPs “inherently vulnerable” to cyber security attacks - Pro Bono Australia
NFPs “inherently vulnerable” to cyber security attacks Pro Bono Australia
http://dlvr.it/Sj0J6h
http://dlvr.it/Sj0J6h
Sunday, February 5, 2023
Transelectrica Establishing Its Own Operational Security Centre - Energy Industry Review
Transelectrica Establishing Its Own Operational Security Centre Energy Industry Review
http://dlvr.it/ShzWMl
http://dlvr.it/ShzWMl
PixPirate: New Android Banking Trojan Targeting Brazilian Financial Institutions
A new Android banking trojan has set its eyes on Brazilian financial institutions to commit fraud by leveraging the PIX payments platform.
Italian cybersecurity company Cleafy, which discovered the malware between the end of 2022 and the beginning of 2023, is tracking it under the name PixPirate.
"PixPirate belongs to the newest generation of Android banking trojan, as it can perform ATS (
http://dlvr.it/ShyKGj
http://dlvr.it/ShyKGj
Saturday, February 4, 2023
Atlassian's Jira Service Management Found Vulnerable to Critical Vulnerability
Atlassian has released fixes to resolve a critical security flaw in Jira Service Management Server and Data Center that could be abused by an attacker to pass off as another user and gain unauthorized access to susceptible instances.
The vulnerability is tracked as CVE-2023-22501 (CVSS score: 9.4) and has been described as a case of broken authentication with low attack complexity.
"An
http://dlvr.it/ShwQXt
http://dlvr.it/ShwQXt
Friday, February 3, 2023
North Korean Hackers Exploit Unpatched Zimbra Devices in 'No Pineapple' Campaign
A new intelligence gathering campaign linked to the prolific North Korean state-sponsored Lazarus Group leveraged known security flaws in unpatched Zimbra devices to compromise victim systems.
That's according to Finnish cybersecurity company WithSecure (formerly F-Secure), which codenamed the incident No Pineapple in reference to an error message that's used in one of the backdoors.
Targets of
http://dlvr.it/ShsrKB
http://dlvr.it/ShsrKB
Thursday, February 2, 2023
Prilex PoS Malware Evolves to Block Contactless Payments to Steal from NFC Cards
The Brazilian threat actors behind an advanced and modular point-of-sale (PoS) malware known as Prilex have reared their head once again with new updates that allow it to block contactless payment transactions.
Russian cybersecurity firm Kaspersky said it detected three versions of Prilex (06.03.8080, 06.03.8072, and 06.03.8070) that are capable of targeting NFC-enabled credit cards, taking its
http://dlvr.it/Shpz75
http://dlvr.it/Shpz75
Wednesday, February 1, 2023
Researchers Uncover Packer Used by Several Malware to Evade Detection for 6 Years
A shellcode-based packer dubbed TrickGate has been successfully operating without attracting notice for over six years, while enabling threat actors to deploy a wide range of malware such as TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil over the years.
"TrickGate managed to stay under the radar for years because it is transformative – it undergoes changes periodically
http://dlvr.it/Shm4NK
http://dlvr.it/Shm4NK
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr