Cybersecurity meets AI: Augmenting and accelerating humans VentureBeat
http://dlvr.it/SnJ8y4
Sunday, April 30, 2023
Financial Cyber Security Market May See Big Move | FireEye ... - Digital Journal
Financial Cyber Security Market May See Big Move | FireEye ... Digital Journal
http://dlvr.it/SnJ8hR
http://dlvr.it/SnJ8hR
Saturday, April 29, 2023
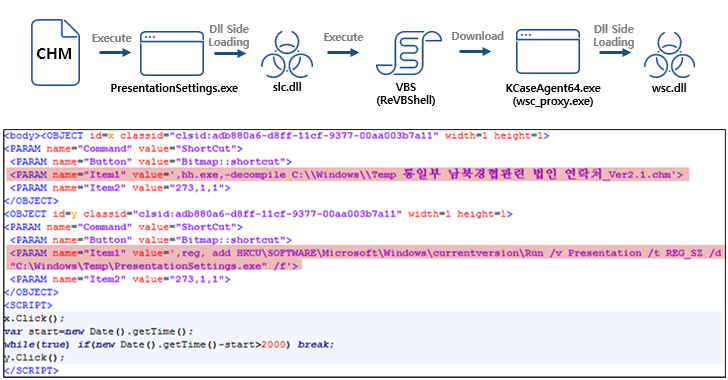
Tonto Team Uses Anti-Malware File to Launch Attacks on South Korean Institutions
South Korean education, construction, diplomatic, and political institutions are at the receiving end of new attacks perpetrated by a China-aligned threat actor known as the Tonto Team.
"Recent cases have revealed that the group is using a file related to anti-malware products to ultimately execute their malicious attacks," the AhnLab Security Emergency Response Center (ASEC) said in a report
http://dlvr.it/SnG0JZ
http://dlvr.it/SnG0JZ
Friday, April 28, 2023
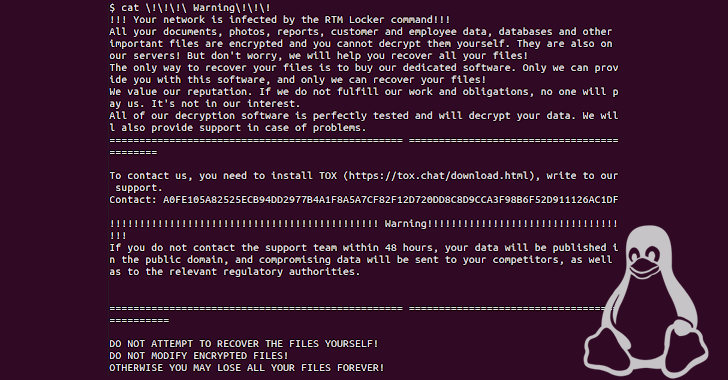
RTM Locker's First Linux Ransomware Strain Targeting NAS and ESXi Hosts
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system.
"Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday. "It uses a combination of ECDH on
http://dlvr.it/SnC7hd
http://dlvr.it/SnC7hd
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware
Microsoft has confirmed that the active exploitation of PaperCut servers is linked to attacks that are designed to deliver Cl0p and LockBit ransomware families.
The tech giant's threat intelligence team is attributing a subset of the intrusions to a financially motivated actor it tracks under the name Lace Tempest (formerly DEV-0950), which overlaps with other hacking groups like FIN11, TA505,
http://dlvr.it/SnC7Th
http://dlvr.it/SnC7Th
Thursday, April 27, 2023
Security experts are jumping ship after cyber incidents - ACS
Security experts are jumping ship after cyber incidents ACS
http://dlvr.it/Sn84S8
http://dlvr.it/Sn84S8
Wednesday, April 26, 2023
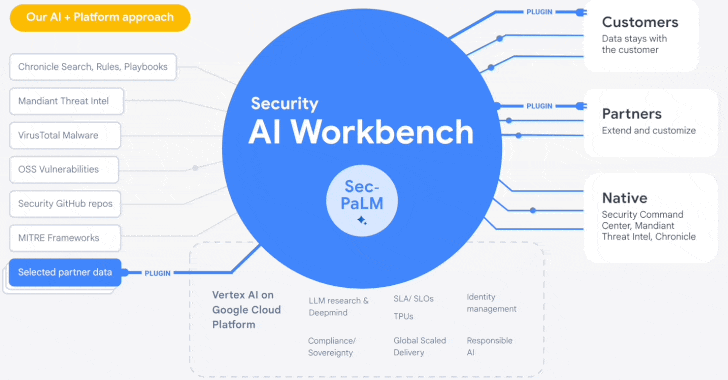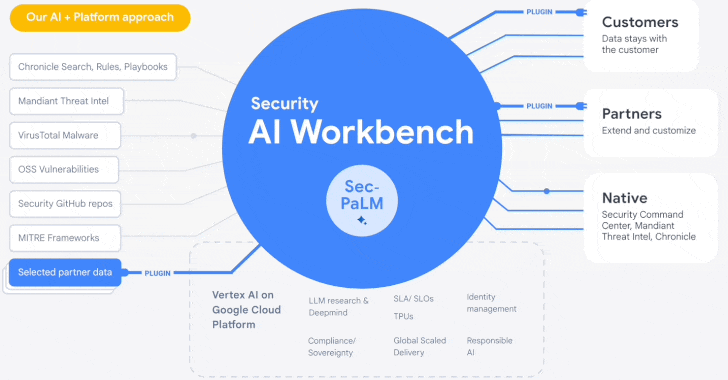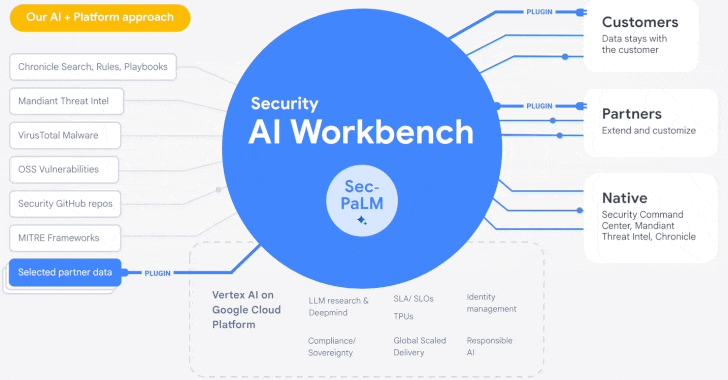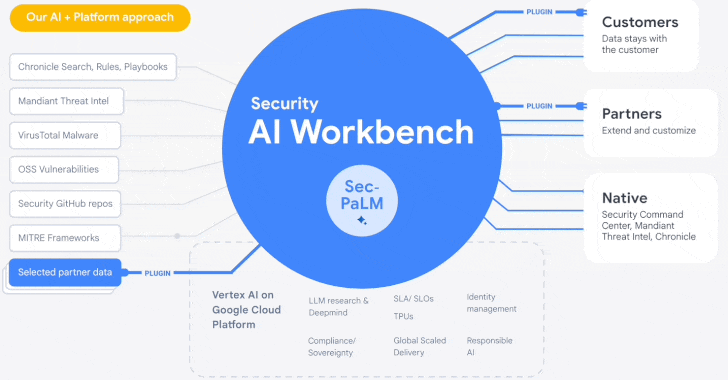
Google Cloud Introduces Security AI Workbench for Faster Threat Detection and Analysis
Google's cloud division is following in the footsteps of Microsoft with the launch of Security AI Workbench that leverages generative AI models to gain better visibility into the threat landscape.
Powering the cybersecurity suite is Sec-PaLM, a specialized large language model (LLM) that's "fine-tuned for security use cases."
The idea is to take advantage of the latest advances in AI to augment
http://dlvr.it/Sn507J
http://dlvr.it/Sn507J
Tuesday, April 25, 2023
Cybersecurity teams should be taking a military approach to winning ... - Federal News Network
Cybersecurity teams should be taking a military approach to winning ... Federal News Network
http://dlvr.it/Sn1zZS
http://dlvr.it/Sn1zZS
Monday, April 24, 2023
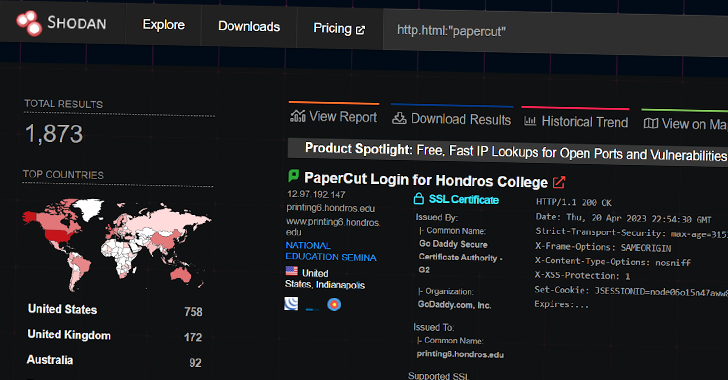
Russian Hackers Suspected in Ongoing Exploitation of Unpatched PaperCut Servers
Print management software provider PaperCut said that it has "evidence to suggest that unpatched servers are being exploited in the wild," citing two vulnerability reports from cybersecurity company Trend Micro.
"PaperCut has conducted analysis on all customer reports, and the earliest signature of suspicious activity on a customer server potentially linked to this vulnerability is 14th April 01
http://dlvr.it/Smz2KP
http://dlvr.it/Smz2KP
Sunday, April 23, 2023
ChatGPT and Cybersecurity: What does it offer for future of small businesses - The Financial Express
ChatGPT and Cybersecurity: What does it offer for future of small businesses The Financial Express
http://dlvr.it/SmwvBK
http://dlvr.it/SmwvBK
Saturday, April 22, 2023
Cyber attack will keep area casinos closed throughout weekend - BradfordToday
Cyber attack will keep area casinos closed throughout weekend BradfordToday
http://dlvr.it/SmtnqL
http://dlvr.it/SmtnqL
Cyber Security Today, Week in Review for the week ending Friday, April 21, 2023 - IT World Canada
Cyber Security Today, Week in Review for the week ending Friday, April 21, 2023 IT World Canada
http://dlvr.it/SmtnbG
http://dlvr.it/SmtnbG
Friday, April 21, 2023
NSO Group Used 3 Zero-Click iPhone Exploits Against Human Rights Defenders
Israeli spyware maker NSO Group deployed at least three novel "zero-click" exploits against iPhones in 2022 to infiltrate defenses erected by Apple and deploy Pegasus, according to the latest findings from Citizen Lab.
"NSO Group customers widely deployed at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets around the world," the interdisciplinary laboratory
http://dlvr.it/SmqyTl
http://dlvr.it/SmqyTl
Thursday, April 20, 2023
Iranian Government-Backed Hackers Targeting U.S. Energy and Transit Systems
An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022.
"This Mint Sandstorm subgroup is technically and operationally mature, capable of developing bespoke tooling and quickly weaponizing N-day vulnerabilities, and has demonstrated agility in its operational focus, which appears to align
http://dlvr.it/SmmvqF
http://dlvr.it/SmmvqF
Wednesday, April 19, 2023
LockBit Ransomware Now Targeting Apple macOS Devices
Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices running Apple's macOS operating system.
The development, which was reported by the MalwareHunterTeam over the weekend, appears to be the first time a big-game ransomware crew has created a macOS-based payload.
Additional samples identified by vx-underground show that the macOS
http://dlvr.it/SmjqGX
http://dlvr.it/SmjqGX
Tuesday, April 18, 2023
Balancing cybersecurity with business priorities: Advice for Boards - Help Net Security
Balancing cybersecurity with business priorities: Advice for Boards Help Net Security
http://dlvr.it/SmfmC1
http://dlvr.it/SmfmC1
Monday, April 17, 2023
Shivaa Nandini R, Author at GBHackers - Latest Cyber Security ... - GBHackers
Shivaa Nandini R, Author at GBHackers - Latest Cyber Security ... GBHackers
http://dlvr.it/Smbpp4
http://dlvr.it/Smbpp4
Sunday, April 16, 2023
The new weakest link in the cybersecurity chain - Help Net Security
The new weakest link in the cybersecurity chain Help Net Security
http://dlvr.it/SmYhTG
http://dlvr.it/SmYhTG
Saturday, April 15, 2023
Webinar: Tips from MSSPs to MSSPs – Building a Profitable vCISO Practice
In today's fast-paced and ever-changing digital landscape, businesses of all sizes face a myriad of cybersecurity threats. Putting in place the right people, technological tools and services, MSSPs are in a great position to ensure their customers' cyber resilience.
The growing need of SMEs and SMBs for structured cybersecurity services can be leveraged by MSPs and MSSPs to provide strategic
http://dlvr.it/SmWbqn
http://dlvr.it/SmWbqn
Friday, April 14, 2023
NCCoE Outlines 6 Steps for Cybersecurity Segmentation in Small ... - Executive Gov
NCCoE Outlines 6 Steps for Cybersecurity Segmentation in Small ... Executive Gov
http://dlvr.it/SmSrPd
http://dlvr.it/SmSrPd
Thursday, April 13, 2023
Urgent: Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit
It's the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been actively exploited in ransomware attacks in the wild.
Seven of the 97 bugs are rated Critical and 90 are rated Important in severity. Interestingly, 45 of the shortcomings are remote code execution flaws, followed by 20
http://dlvr.it/SmPswr
http://dlvr.it/SmPswr
Wednesday, April 12, 2023
Cryptocurrency Stealer Malware Distributed via 13 NuGet Packages
Cybersecurity researchers have detailed the inner workings of the cryptocurrency stealer malware that was distributed via 13 malicious NuGet packages as part of a supply chain attack targeting .NET developers.
The sophisticated typosquatting campaign, which was uncovered by JFrog late last month, impersonated legitimate packages to execute PowerShell code designed to retrieve a follow-on binary
http://dlvr.it/SmLtwW
http://dlvr.it/SmLtwW
Tuesday, April 11, 2023
Protecting your business with Wazuh: The open source security platform
Today, businesses face a variety of security challenges like cyber attacks, compliance requirements, and endpoint security administration. The threat landscape constantly evolves, and it can be overwhelming for businesses to keep up with the latest security trends. Security teams use processes and security solutions to curb these challenges. These solutions include firewalls, antiviruses, data
http://dlvr.it/SmHy4G
http://dlvr.it/SmHy4G
Monday, April 10, 2023
CISA Warns of 5 Actively Exploited Security Flaws: Urgent Action Required
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added five security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild.
This includes three high-severity flaws in the Veritas Backup Exec Agent software (CVE-2021-27876, CVE-2021-27877, and CVE-2021-27878) that could lead to the execution of privileged commands
http://dlvr.it/SmFKtq
http://dlvr.it/SmFKtq
Sunday, April 9, 2023
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation.
That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed
http://dlvr.it/SmCNjc
http://dlvr.it/SmCNjc
Saturday, April 8, 2023
Researchers Uncover Thriving Phishing Kit Market on Telegram Channels
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help set up phishing campaigns.
"To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type
http://dlvr.it/Sm9Q4D
http://dlvr.it/Sm9Q4D
Friday, April 7, 2023
2022 Cybersecurity Annual Earnings Recap (Part 2) - Security Boulevard
2022 Cybersecurity Annual Earnings Recap (Part 2) Security Boulevard
http://dlvr.it/Sm6t7v
http://dlvr.it/Sm6t7v
City strengthens cyber security, enlisting help of employees - Spectrum News NY1
City strengthens cyber security, enlisting help of employees Spectrum News NY1
http://dlvr.it/Sm6svf
http://dlvr.it/Sm6svf
Thursday, April 6, 2023
Typhon Reborn Stealer Malware Resurfaces with Advanced Evasion Techniques
The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and resist analysis.
The new version is offered for sale on the criminal underground for $59 per month, $360 per year, or alternatively, for $540 for a lifetime subscription.
"The stealer can harvest and exfiltrate
http://dlvr.it/Sm44sS
http://dlvr.it/Sm44sS
Wednesday, April 5, 2023
Think Before You Share the Link: SaaS in the Real World
Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in the top two headlines on Google Workspace’s homepage. It can be found six times on Microsoft 365’s homepage, three times on Box, and once on Workday. Visit nearly any SaaS site, and odds are ‘collaboration’ will appear as part of the app’s key selling point.
By sitting on the cloud, content within
http://dlvr.it/Sm1QK2
http://dlvr.it/Sm1QK2
Tuesday, April 4, 2023
Crypto-Stealing OpcJacker Malware Targets Users with Fake VPN Service
A piece of new information-stealing malware called OpcJacker has been spotted in the wild since the second half of 2022 as part of a malvertising campaign.
"OpcJacker's main functions include keylogging, taking screenshots, stealing sensitive data from browsers, loading additional modules, and replacing cryptocurrency addresses in the clipboard for hijacking purposes," Trend Micro researchers
http://dlvr.it/SlyPFG
http://dlvr.it/SlyPFG
Monday, April 3, 2023
TCC Offering Free 6-Month Cybersecurity Training Program - News On 6
TCC Offering Free 6-Month Cybersecurity Training Program News On 6
http://dlvr.it/SlvSqK
http://dlvr.it/SlvSqK
Sunday, April 2, 2023
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps
Microsoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access management service that exposed several "high-impact" applications to unauthorized access.
"One of these apps is a content management system (CMS) that powers Bing.com and allowed us to not only modify search results, but also launch high-impact XSS attacks on Bing users," cloud security
http://dlvr.it/SlsFvC
http://dlvr.it/SlsFvC
Saturday, April 1, 2023
3CX Supply Chain Attack — Here's What We Know So Far
Enterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for Windows and macOS are affected by a supply chain attack.
The version numbers include 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS.
The company said it's engaging the services of Google-owned Mandiant to review the incident. In the
http://dlvr.it/Slq85s
http://dlvr.it/Slq85s
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr