Cybersecurity AI: Pioneering the new norm of zero trust Tech Wire Asia
http://dlvr.it/SrS9wd
Friday, June 30, 2023
Thursday, June 29, 2023
Critical SQL Injection Flaws Expose Gentoo Soko to Remote Code Execution
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution (RCE) on vulnerable systems.
"These SQL injections happened despite the use of an Object-Relational Mapping (ORM) library and prepared statements," SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a "misconfiguration of the database.
http://dlvr.it/SrPQ9z
http://dlvr.it/SrPQ9z
Wednesday, June 28, 2023
Tuesday, June 27, 2023
Microsoft Warns of Widescale Credential Stealing Attacks by Russian Hackers
Microsoft has disclosed that it's detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard.
The intrusions, which made use of residential proxy services to obfuscate the source IP address of the attacks, target governments, IT service providers, NGOs, defense, and critical manufacturing sectors, the tech giant's threat
http://dlvr.it/SrHlsN
http://dlvr.it/SrHlsN
Monday, June 26, 2023
Chinese Hackers Using Never-Before-Seen Tactics for Critical Infrastructure Attacks
The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to never-before-seen tradecraft to retain remote access to targets of interest.
The findings come from CrowdStrike, which is tracking the adversary under the name Vanguard Panda.
"The adversary consistently employed ManageEngine
http://dlvr.it/SrDscW
http://dlvr.it/SrDscW
Sunday, June 25, 2023
Saturday, June 24, 2023
New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices
Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency.
"The threat actors behind the attack use a backdoor that deploys a wide array of tools and components such as rootkits and an IRC bot to steal device resources for mining operations," Microsoft threat intelligence researcher Rotem Sde-Or said.
http://dlvr.it/Sr8nX6
http://dlvr.it/Sr8nX6
Friday, June 23, 2023
Thursday, June 22, 2023
Wednesday, June 21, 2023
Tuesday, June 20, 2023
Monday, June 19, 2023
Doubling Down on Email Security with Data Sovereignty - Australia Cyber Security Magazine
Doubling Down on Email Security with Data Sovereignty Australia Cyber Security Magazine
http://dlvr.it/SqtbgP
http://dlvr.it/SqtbgP
The UK-Singapore Cyber Dialogue - GOV.UK
The UK-Singapore Cyber Dialogue GOV.UK
http://dlvr.it/SqtbQQ
http://dlvr.it/SqtbQQ
Sunday, June 18, 2023
Saturday, June 17, 2023
20-Year-Old Russian LockBit Ransomware Affiliate Arrested in Arizona
The U.S. Department of Justice (DoJ) on Thursday unveiled charges against a Russian national for his alleged involvement in deploying LockBit ransomware to targets in the U.S., Asia, Europe, and Africa.
Ruslan Magomedovich Astamirov, 20, of Chechen Republic has been accused of perpetrating at least five attacks between August 2020 and March 2023. He was arrested in the state of Arizona last
http://dlvr.it/SqpYww
http://dlvr.it/SqpYww
Friday, June 16, 2023
Text 'scam' losses total $330 million in 2022, FBI and UWF cybersecurity expert weigh in - WEAR
Text 'scam' losses total $330 million in 2022, FBI and UWF cybersecurity expert weigh in WEAR
http://dlvr.it/SqltBv
http://dlvr.it/SqltBv
Thursday, June 15, 2023
Microsoft Releases Updates to Patch Critical Flaws in Windows and Other Software
Microsoft has rolled out fixes for its Windows operating system and other software components to remediate major security shortcomings as part of Patch Tuesday updates for June 2023.
Of the 73 flaws, six are rated Critical, 63 are rated Important, two are rated Moderate, and one is rated Low in severity. This also includes three issues the tech giant addressed in its Chromium-based Edge browser.
http://dlvr.it/Sqj2GP
http://dlvr.it/Sqj2GP
Wednesday, June 14, 2023
Two Russian Nationals Charged for Masterminding Mt. Gox Crypto Exchange Hack
The U.S. Department of Justice (DoJ) has charged two Russian nationals in connection with masterminding the 2014 digital heist of the now-defunct cryptocurrency exchange Mt. Gox.
According to unsealed indictments released last week, Alexey Bilyuchenko, 43, and Aleksandr Verner, 29, have been accused of conspiring to launder approximately 647,000 bitcoins stolen from September 2011 through at
http://dlvr.it/Sqf7Zn
http://dlvr.it/Sqf7Zn
Critical FortiOS and FortiProxy Vulnerability Likely Exploited - Patch Now!
Fortinet on Monday disclosed that a newly patched critical flaw impacting FortiOS and FortiProxy may have been "exploited in a limited number of cases" in attacks targeting government, manufacturing, and critical infrastructure sectors.
The vulnerability, tracked as CVE-2023-27997 (CVSS score: 9.2), concerns a heap-based buffer overflow vulnerability in FortiOS and FortiProxy SSL-VPN that could
http://dlvr.it/Sqf7Pj
http://dlvr.it/Sqf7Pj
Tuesday, June 13, 2023
Monday, June 12, 2023
Sunday, June 11, 2023
Saturday, June 10, 2023
Cybersecurity Insights with Contrast CISO David Lindner | 6/9 - Security Boulevard
Cybersecurity Insights with Contrast CISO David Lindner | 6/9 Security Boulevard
http://dlvr.it/SqSB0f
http://dlvr.it/SqSB0f
Friday, June 9, 2023
How to Improve Your API Security Posture
APIs, more formally known as application programming interfaces, empower apps and microservices to communicate and share data. However, this level of connectivity doesn't come without major risks. Hackers can exploit vulnerabilities in APIs to gain unauthorized access to sensitive data or even take control of the entire system. Therefore, it's essential to have a robust API security posture to
http://dlvr.it/SqPKyF
http://dlvr.it/SqPKyF
Thursday, June 8, 2023
Wednesday, June 7, 2023
Top 10 risky employee cyber security behaviours revealed - Cyber Security Connect
Top 10 risky employee cyber security behaviours revealed Cyber Security Connect
http://dlvr.it/SqH9qZ
http://dlvr.it/SqH9qZ
Tuesday, June 6, 2023
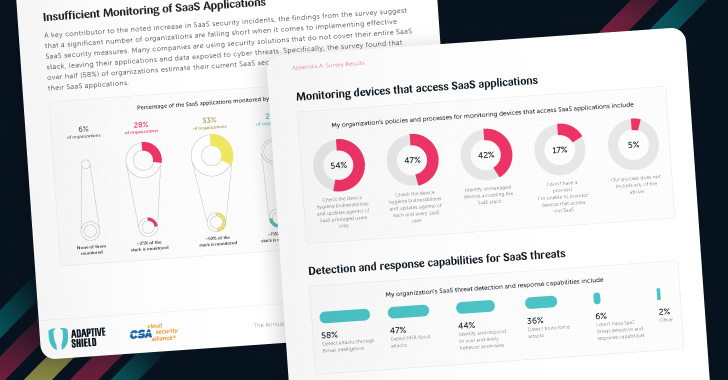
The Annual Report: 2024 Plans and Priorities for SaaS Security
Over 55% of security executives report that they have experienced a SaaS security incident in the past two years — ranging from data leaks and data breaches to SaaS ransomware and malicious apps (as seen in figures 1 and 2).
Figure 1. How many organizations have experienced a SaaS security incident within the past two years
The SaaS Security Survey Report: Plans and Priorities for 2024,
http://dlvr.it/SqD1jH
http://dlvr.it/SqD1jH
Monday, June 5, 2023
Bringing the cyber security lessons of 2022 into 2023 - Promoted ... - CRN Australia
Bringing the cyber security lessons of 2022 into 2023 - Promoted ... CRN Australia
http://dlvr.it/Sq8xZg
http://dlvr.it/Sq8xZg
Sunday, June 4, 2023
Cyber Security Deal Tracker Market May See a Big Move | FireEye ... - Digital Journal
Cyber Security Deal Tracker Market May See a Big Move | FireEye ... Digital Journal
http://dlvr.it/Sq6jcK
http://dlvr.it/Sq6jcK
Saturday, June 3, 2023
Camaro Dragon Strikes with New TinyNote Backdoor for Intelligence Gathering
The Chinese nation-state group known as Camaro Dragon has been linked to yet another backdoor that's designed to meet its intelligence-gathering goals.
Israeli cybersecurity firm Check Point, which dubbed the Go-based malware TinyNote, said it functions as a first-stage payload capable of "basic machine enumeration and command execution via PowerShell or Goroutines."
What the malware lacks in
http://dlvr.it/Sq4Vnd
http://dlvr.it/Sq4Vnd
Friday, June 2, 2023
N. Korean ScarCruft Hackers Exploit LNK Files to Spread RokRAT
Cybersecurity researchers have offered a closer look at the RokRAT remote access trojan that's employed by the North Korean state-sponsored actor known as ScarCruft.
"RokRAT is a sophisticated remote access trojan (RAT) that has been observed as a critical component within the attack chain, enabling the threat actors to gain unauthorized access, exfiltrate sensitive information, and potentially
http://dlvr.it/Sq1cP0
http://dlvr.it/Sq1cP0
Thursday, June 1, 2023
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr