The Week in Ransomware - September 29th 2023 - Dark Angels BleepingComputer
http://dlvr.it/Swp6nb
Saturday, September 30, 2023
Friday, September 29, 2023
The Dark Side of Browser Isolation – and the Next Generation Browser Security Technologies
The landscape of browser security has undergone significant changes over the past decade. While Browser Isolation was once considered the gold standard for protecting against browser exploits and malware downloads, it has become increasingly inadequate and insecure in today's SaaS-centric world.
The limitations of Browser Isolation, such as degraded browser performance and inability to tackle
http://dlvr.it/SwlhCk
The limitations of Browser Isolation, such as degraded browser performance and inability to tackle
http://dlvr.it/SwlhCk
China-Linked Budworm Targeting Middle Eastern Telco and Asian Government Agencies
Government and telecom entities have been subjected to a new wave of attacks by a China-linked threat actor tracked as Budworm using an updated malware toolset.
The intrusions, targeting a Middle Eastern telecommunications organization and an Asian government, took place in August 2023, with the adversary deploying an improved version of its SysUpdate toolkit, the Symantec Threat Hunter Team,
http://dlvr.it/Swlh6R
The intrusions, targeting a Middle Eastern telecommunications organization and an Asian government, took place in August 2023, with the adversary deploying an improved version of its SysUpdate toolkit, the Symantec Threat Hunter Team,
http://dlvr.it/Swlh6R
Thursday, September 28, 2023
Wednesday, September 27, 2023
Cyber Security Awareness Month 2023: Be cyber wise – don't ... - Business Victoria
Cyber Security Awareness Month 2023: Be cyber wise – don't ... Business Victoria
http://dlvr.it/SwfbyL
http://dlvr.it/SwfbyL
Tuesday, September 26, 2023
Monday, September 25, 2023
Sunday, September 24, 2023
Bermuda government hit by cyber attack | Loop Caribbean News - Loop News Caribbean
Bermuda government hit by cyber attack | Loop Caribbean News Loop News Caribbean
http://dlvr.it/SwX7xW
http://dlvr.it/SwX7xW
Saturday, September 23, 2023
New Variant of Banking Trojan BBTok Targets Over 40 Latin American Banks
An active malware campaign targeting Latin America is dispensing a new variant of a banking trojan called BBTok, particularly users in Brazil and Mexico.
"The BBTok banker has a dedicated functionality that replicates the interfaces of more than 40 Mexican and Brazilian banks, and tricks the victims into entering its 2FA code to their bank accounts or into entering their payment card number,"
http://dlvr.it/SwVVkN
http://dlvr.it/SwVVkN
How to Interpret the 2023 MITRE ATT&CK Evaluation Results
Thorough, independent tests are a vital resource for analyzing provider’s capabilities to guard against increasingly sophisticated threats to their organization. And perhaps no assessment is more widely trusted than the annual MITRE Engenuity ATT&CK Evaluation.
This testing is critical for evaluating vendors because it’s virtually impossible to evaluate cybersecurity vendors based on their own
http://dlvr.it/SwVVbZ
http://dlvr.it/SwVVbZ
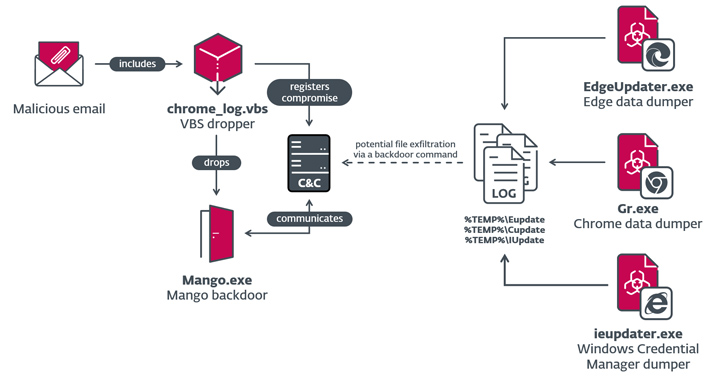
Iranian Nation-State Actor OilRig Targets Israeli Organizations
Israeli organizations were targeted as part of two different campaigns orchestrated by the Iranian nation-state actor known as OilRig in 2021 and 2022.
The campaigns, dubbed Outer Space and Juicy Mix, entailed the use of two previously documented first-stage backdoors called Solar and Mango, which were deployed to collect sensitive information from major browsers and the Windows Credential
http://dlvr.it/SwVVWh
http://dlvr.it/SwVVWh
High-Severity Flaws Uncovered in Atlassian Products and ISC BIND Server
Atlassian and the Internet Systems Consortium (ISC) have disclosed several security flaws impacting their products that could be exploited to achieve denial-of-service (DoS) and remote code execution.
The Australian software services provider said that the four high-severity flaws were fixed in new versions shipped last month. This includes -
CVE-2022-25647 (CVSS score: 7.5) - A deserialization
http://dlvr.it/SwVVRy
http://dlvr.it/SwVVRy
Friday, September 22, 2023
Unlocking the Future of Cybersecurity: Meet Us at GovWare 2023 - Security Boulevard
Unlocking the Future of Cybersecurity: Meet Us at GovWare 2023 Security Boulevard
http://dlvr.it/SwSFHN
http://dlvr.it/SwSFHN
Thursday, September 21, 2023
GitLab Releases Urgent Security Patches for Critical Vulnerability
GitLab has shipped security patches to resolve a critical flaw that allows an attacker to run pipelines as another user.
The issue, tracked as CVE-2023-5009 (CVSS score: 9.6), impacts all versions of GitLab Enterprise Edition (EE) starting from 13.12 and prior to 16.2.7 as well as from 16.3 and before 16.3.4.
"It was possible for an attacker to run pipelines as an arbitrary user via scheduled
http://dlvr.it/SwQCMK
http://dlvr.it/SwQCMK
Wednesday, September 20, 2023
Singapore: Lags in cyber security practices despite growing ... - Asia Insurance Review
Singapore: Lags in cyber security practices despite growing ... Asia Insurance Review
http://dlvr.it/SwMgcb
http://dlvr.it/SwMgcb
Tuesday, September 19, 2023
Think Your MFA and PAM Solutions Protect You? Think Again
When you roll out a security product, you assume it will fulfill its purpose. Unfortunately, however, this often turns out not to be the case. A new report, produced by Osterman Research and commissioned by Silverfort, reveals that MFA (Multi-Factor Authentication) and PAM (Privileged Access Management) solutions are almost never deployed comprehensively enough to provide resilience to identity
http://dlvr.it/SwJp1p
http://dlvr.it/SwJp1p
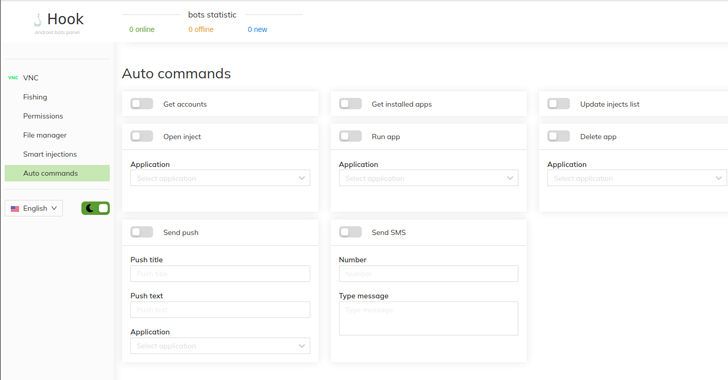
Hook: New Android Banking Trojan That Expands on ERMAC's Legacy
A new analysis of the Android banking trojan known as Hook has revealed that it's based on its predecessor called ERMAC.
"The ERMAC source code was used as a base for Hook," NCC Group security researchers Joshua Kamp and Alberto Segura said in a technical analysis published last week.
"All commands (30 in total) that the malware operator can send to a device infected with ERMAC malware, also
http://dlvr.it/SwJnqj
http://dlvr.it/SwJnqj
Retool Falls Victim to SMS-Based Phishing Attack Affecting 27 Cloud Clients
Software development company Retool has disclosed that the accounts of 27 of its cloud customers were compromised following a targeted and SMS-based social engineering attack.
The San Francisco-based firm blamed a Google Account cloud synchronization feature recently introduced in April 2023 for making the breach worse, calling it a "dark pattern."
"The fact that Google Authenticator syncs to
http://dlvr.it/SwJndW
http://dlvr.it/SwJndW
Monday, September 18, 2023
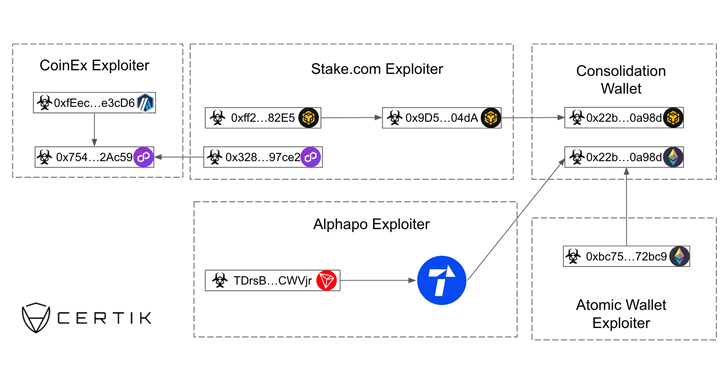
North Korea's Lazarus Group Suspected in $31 Million CoinEx Heist
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation of its hacks.
According to multiple reports from Certik, Elliptic, and ZachXBT, the infamous hacking group is said to be suspected behind the theft of $31 million in digital assets from the CoinEx exchange on September 12, 2023.
The crypto heist aimed at
http://dlvr.it/SwFy3S
http://dlvr.it/SwFy3S
Sunday, September 17, 2023
TikTok Faces Massive €345 Million Fine Over Child Data Violations in E.U.
The Irish Data Protection Commission (DPC) slapped TikTok with a €345 million (about $368 million) fine for violating the European Union's General Data Protection Regulation (GDPR) in relation to its handling of children's data.
The investigation, initiated in September 2021, examined how the popular short-form video platform processed personal data relating to child users (those between the
http://dlvr.it/SwCv24
http://dlvr.it/SwCv24
Saturday, September 16, 2023
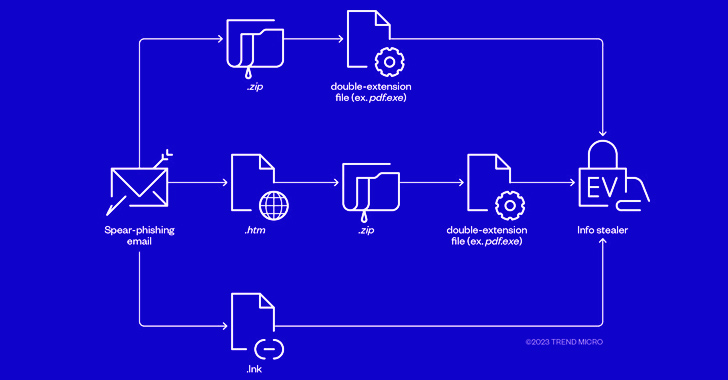
Cybercriminals Combine Phishing and EV Certificates to Deliver Ransomware Payloads
The threat actors behind RedLine and Vidar information stealers have been observed pivoting to ransomware through phishing campaigns that spread initial payloads signed with Extended Validation (EV) code signing certificates.
"This suggests that the threat actors are streamlining operations by making their techniques multipurpose," Trend Micro researchers said in a new analysis published this
http://dlvr.it/Sw9wDQ
http://dlvr.it/Sw9wDQ
Friday, September 15, 2023
Russian Journalist's iPhone Compromised by NSO Group's Zero-Click Spyware
The iPhone belonging to Galina Timchenko, a prominent Russian journalist and critic of the government, was compromised with NSO Group's Pegasus spyware, a new collaborative investigation from Access Now and the Citizen Lab has revealed.
The infiltration is said to have happened on or around February 10, 2023. Timchenko is the executive editor and owner of Meduza, an independent news publication
http://dlvr.it/Sw7K60
http://dlvr.it/Sw7K60
Thursday, September 14, 2023
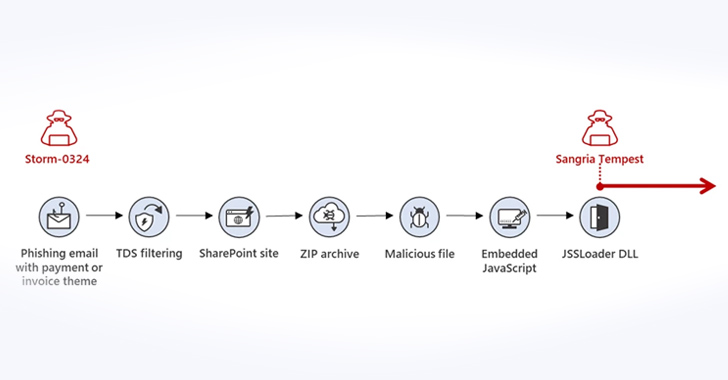
Microsoft Warns of New Phishing Campaign Targeting Corporations via Teams Messages
Microsoft is warning of a new phishing campaign undertaken by an initial access broker that involves using Teams messages as lures to infiltrate corporate networks.
The tech giant's Threat Intelligence team is tracking the cluster under the name Storm-0324, which is also known by the monikers TA543 and Sagrid.
"Beginning in July 2023, Storm-0324 was observed distributing payloads using an
http://dlvr.it/Sw4ZVz
http://dlvr.it/Sw4ZVz
Wednesday, September 13, 2023
Understanding Cyber Security Posture: Assess and Strengthen Your Organization’s Defenses - Security Boulevard
Understanding Cyber Security Posture: Assess and Strengthen Your Organization’s Defenses Security Boulevard
http://dlvr.it/Sw1q1L
http://dlvr.it/Sw1q1L
Tuesday, September 12, 2023
Crayon Fortifies 'Journey to Value' for Partners with Extended ... - Macau Business
Crayon Fortifies 'Journey to Value' for Partners with Extended ... Macau Business
http://dlvr.it/Svz2lD
http://dlvr.it/Svz2lD
Monday, September 11, 2023
New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World
A new malware loader called HijackLoader is gaining traction among the cybercriminal community to deliver various payloads such as DanaBot, SystemBC, and RedLine Stealer.
"Even though HijackLoader does not contain advanced features, it is capable of using a variety of modules for code injection and execution since it uses a modular architecture, a feature that most loaders do not have," Zscaler
http://dlvr.it/SvwP7g
http://dlvr.it/SvwP7g
Sunday, September 10, 2023
Cybercriminals Weaponizing Legitimate Advanced Installer Tool in Crypto-Mining Attacks
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021.
"The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses
http://dlvr.it/SvtTPH
http://dlvr.it/SvtTPH
Saturday, September 9, 2023
HSHS Senior VP and CFO leaves the company less than two weeks after cybersecurity incident - WAND
HSHS Senior VP and CFO leaves the company less than two weeks after cybersecurity incident WAND
http://dlvr.it/SvrTlx
http://dlvr.it/SvrTlx
Friday, September 8, 2023
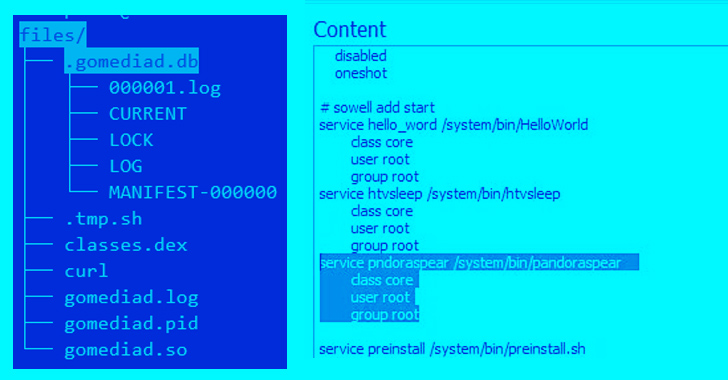
Mirai Botnet Variant 'Pandora' Hijacks Android TVs for Cyberattacks
A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as part of a botnet to perform distributed denial-of-service (DDoS) attacks.
Doctor Web said the compromises are likely to occur either during malicious firmware updates or when applications for viewing pirated video content are installed.
"It is likely that this
http://dlvr.it/Svny8Z
http://dlvr.it/Svny8Z
Outlook Hack: Microsoft Reveals How a Crash Dump Led to a Major Security Breach
Microsoft on Wednesday revealed that a China-based threat actor known as Storm-0558 acquired the inactive consumer signing key to forge tokens and access Outlook by compromising an engineer’s corporate account.
This enabled the adversary to access a debugging environment that contained information pertaining to a crash of the consumer signing system and steal the key. The system crash took place
http://dlvr.it/Svnxtj
http://dlvr.it/Svnxtj
Thursday, September 7, 2023
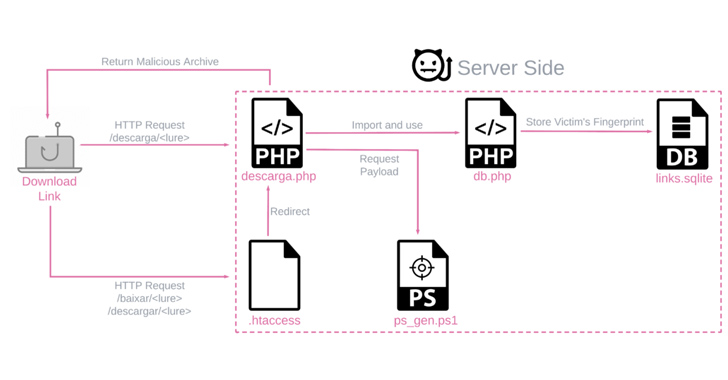
Ukraine's CERT Thwarts APT28's Cyberattack on Critical Energy Infrastructure
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday said it thwarted a cyber attack against an unnamed critical energy infrastructure facility in the country.
The intrusion, per the agency, started with a phishing email containing a link to a malicious ZIP archive that activates the infection chain.
“Visiting the link will download a ZIP archive containing three JPG images (
http://dlvr.it/SvlD4Z
http://dlvr.it/SvlD4Z
Wednesday, September 6, 2023
Rogue states using fake GPT content to hack governments - cyber ... - The Jerusalem Post
Rogue states using fake GPT content to hack governments - cyber ... The Jerusalem Post
http://dlvr.it/SvhTW0
http://dlvr.it/SvhTW0
Tuesday, September 5, 2023
Vietnamese Cybercriminals Targeting Facebook Business Accounts with Malvertising
Malicious actors associated with the Vietnamese cybercrime ecosystem are leveraging advertising-as-a-vector on social media platforms such as Meta-owned Facebook to distribute malware.
“Threat actors have long used fraudulent ads as a vector to target victims with scams, malvertising, and more,” WithSecure researcher Mohammad Kazem Hassan Nejad said. “And with businesses now leveraging the reach
http://dlvr.it/Svdn6n
http://dlvr.it/Svdn6n
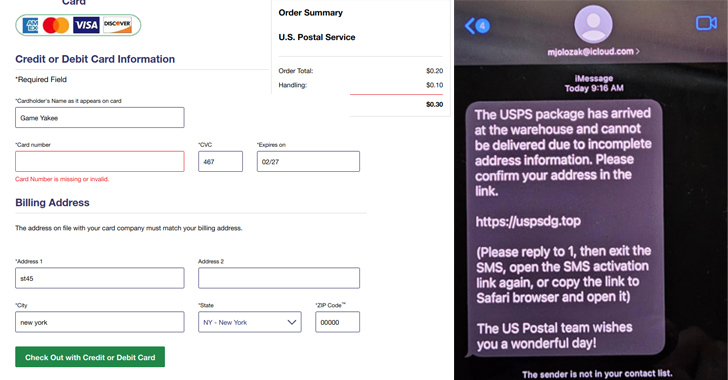
Chinese-Speaking Cybercriminals Launch Large-Scale iMessage Smishing Campaign in U.S.
A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple iCloud accounts with an aim to conduct identity theft and financial fraud.
“The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information (PII) and payment credentials from victims, in the
http://dlvr.it/SvdmzR
http://dlvr.it/SvdmzR
Monday, September 4, 2023
Sunday, September 3, 2023
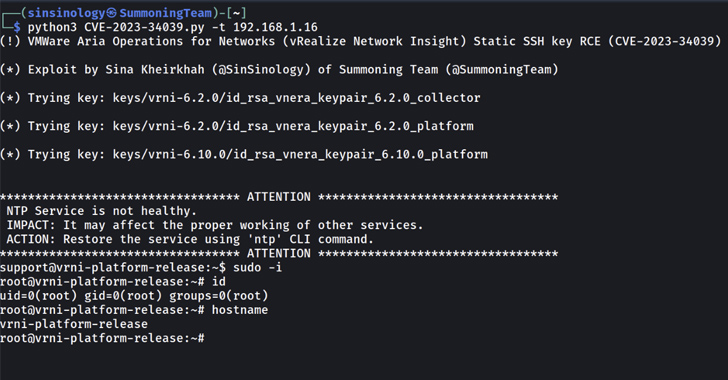
PoC Exploit Released for Critical VMware Aria's SSH Auth Bypass Vulnerability
Proof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Insight).
The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a maximum of 10 for severity and has been described as a case of authentication bypass due to a lack of unique cryptographic key generation.
“A
http://dlvr.it/SvYQc2
http://dlvr.it/SvYQc2
Saturday, September 2, 2023
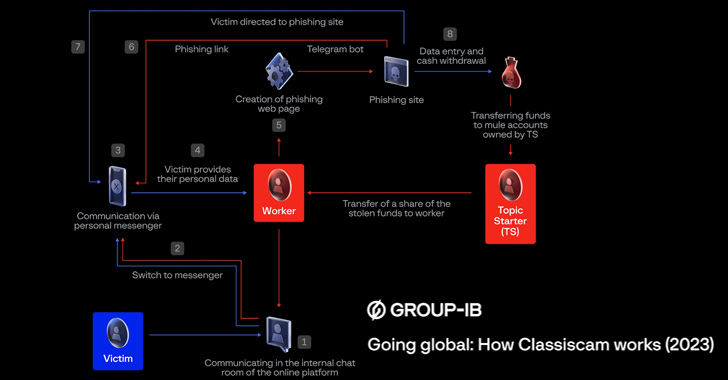
Classiscam Scam-as-a-Service Raked $64.5 Million During the COVID-19 Pandemic
The Classiscam scam-as-a-service program has reaped the criminal actors $64.5 million in illicit earnings since its emergence in 2019.
"Classiscam campaigns initially started out on classified sites, on which scammers placed fake advertisements and used social engineering techniques to convince users to pay for goods by transferring money to bank cards," Group-IB said in a new report.
"Since
http://dlvr.it/SvWb6r
http://dlvr.it/SvWb6r
Friday, September 1, 2023
Earth Estries' Espionage Campaign Targets Governments and Tech Titans Across Continents
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign targeting government and technology industries based in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the U.S.
"The threat actors behind Earth Estries are working with high-level resources and functioning with sophisticated skills and experience in cyber espionage and illicit
http://dlvr.it/SvT4Qz
http://dlvr.it/SvT4Qz
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr