DoD grants fund cybersecurity research for maritime industry SC Media
http://dlvr.it/SXZhWx
Wednesday, August 31, 2022
Apple Releases iOS Update for Older iPhones to Fix Actively Exploited Vulnerability
Apple on Wednesday backported security updates to older iPhones, iPads, and iPod touch devices to address a critical security flaw that has been actively exploited in the wild.
The issue, tracked as CVE-2022-32893 (CVSS score: 8.8), is an out-of-bounds write issue affecting WebKit that could lead to arbitrary code execution when processing maliciously crafted web content.
The tech
http://dlvr.it/SXZgYL
http://dlvr.it/SXZgYL
(ISC)² Launches Certified in Cybersecurity Entry-Level Certification to Address Global Workforce Gap - PR Newswire
(ISC)² Launches Certified in Cybersecurity Entry-Level Certification to Address Global Workforce Gap PR Newswire
http://dlvr.it/SXYPJk
http://dlvr.it/SXYPJk
Chinese Hackers Used ScanBox Framework in Recent Cyber Espionage Attacks
A months-long cyber espionage campaign undertaken by a Chinese nation-state group targeted several entities with reconnaissance malware so as to glean information about its victims and meet its strategic goals.
"The targets of this recent campaign spanned Australia, Malaysia, and Europe, as well as entities that operate in the South China Sea," enterprise security firm Proofpoint said in a
http://dlvr.it/SXXrqD
http://dlvr.it/SXXrqD
Tuesday, August 30, 2022
Tech, Cyber Companies Launch Security Standard to Monitor Hacking Attempts - The Wall Street Journal
Tech, Cyber Companies Launch Security Standard to Monitor Hacking Attempts The Wall Street Journal
http://dlvr.it/SXWFn2
http://dlvr.it/SXWFn2
FTC Sues Data Broker Over Selling Location Data for Hundreds of Millions of Phones
The U.S. Federal Trade Commission (FTC) on Monday said it filed a lawsuit against Kochava, a location data broker, for collecting and selling precise geolocation data gathered from consumers' mobile devices.
The complaint alleges that the U.S. company amasses a "wealth of information" about users by purchasing data from other data brokers to sell to its own clients.
"Kochava then sells
http://dlvr.it/SXTfD8
http://dlvr.it/SXTfD8
Monday, August 29, 2022
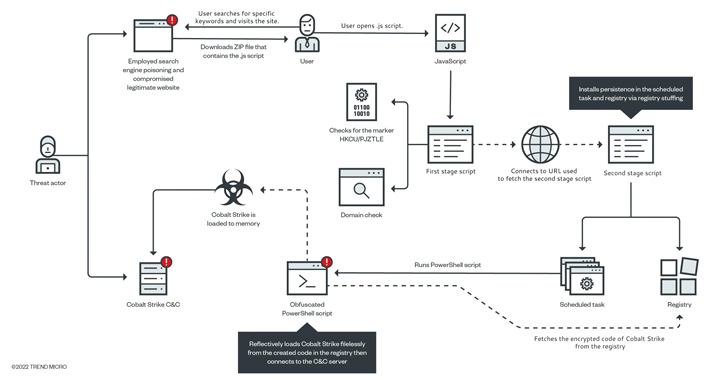
New Golang-based 'Agenda Ransomware' Can Be Customized For Each Victim
A new ransomware strain written in Golang dubbed "Agenda" has been spotted in the wild, targeting healthcare and education entities in Indonesia, Saudi Arabia, South Africa, and Thailand.
"Agenda can reboot systems in safe mode, attempts to stop many server-specific processes and services, and has multiple modes to run," Trend Micro researchers said in an analysis last week.
Qilin, the threat
http://dlvr.it/SXRTpg
http://dlvr.it/SXRTpg
Minister: Friday's cyber-attack on private media part of consistent pattern - ERR News
Minister: Friday's cyber-attack on private media part of consistent pattern ERR News
http://dlvr.it/SXR3qd
http://dlvr.it/SXR3qd
CISA Adds 10 New Known Actively Exploited Vulnerabilities to its Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added 10 new actively exploited vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, including a high-severity security flaw affecting industrial automation software from Delta Electronics.
The issue, tracked as CVE-2021-38406 (CVSS score: 7.8), impacts DOPSoft 2 versions 2.00.07 and prior. A successful
http://dlvr.it/SXQY9c
http://dlvr.it/SXQY9c
Sunday, August 28, 2022
Cedar Rapids schools make ransom payment in regard to cyber security incident - KCRG
Cedar Rapids schools make ransom payment in regard to cyber security incident KCRG
http://dlvr.it/SXP4dN
http://dlvr.it/SXP4dN
Bug bounties to become part of Swiss cyber-security arsenal - SWI swissinfo.ch in English
Bug bounties to become part of Swiss cyber-security arsenal SWI swissinfo.ch in English
http://dlvr.it/SXNs1j
http://dlvr.it/SXNs1j
Fact Sheet: DHS International Cybersecurity Efforts - Homeland Security
Fact Sheet: DHS International Cybersecurity Efforts Homeland Security
http://dlvr.it/SXNbtr
http://dlvr.it/SXNbtr
80% of firms have suffered a cyber attack in the last year. Security begins from the top - ThePrint
80% of firms have suffered a cyber attack in the last year. Security begins from the top ThePrint
http://dlvr.it/SXN0B9
http://dlvr.it/SXN0B9
Saturday, August 27, 2022
How to build a 'cybersecurity ready' organizational culture - World Economic Forum
How to build a 'cybersecurity ready' organizational culture World Economic Forum
http://dlvr.it/SXM0yD
http://dlvr.it/SXM0yD
What Cybersecurity Teams Can Learn From the US Cyber Command's 'Hunt Forward' - Security Intelligence
What Cybersecurity Teams Can Learn From the US Cyber Command's 'Hunt Forward' Security Intelligence
http://dlvr.it/SXLpWy
http://dlvr.it/SXLpWy
Cybersecurity on the board: How the CISO role is evolving for a new era - Tech Monitor
Cybersecurity on the board: How the CISO role is evolving for a new era Tech Monitor
http://dlvr.it/SXLG5V
http://dlvr.it/SXLG5V
Iranian Hackers Exploiting Unpatched Log4j 2 Bugs to Target Israeli Organizations
Iranian state-sponsored actors are leaving no stone unturned to exploit unpatched systems running Log4j to target Israeli entities, indicating the vulnerability’s long tail for remediation.
Microsoft attributed the latest set of activities to the umbrella threat group tracked as MuddyWater (aka Cobalt Ulster, Mercury, Seedworm, or Static Kitten), which is linked to the Iranian intelligence
http://dlvr.it/SXKwsQ
http://dlvr.it/SXKwsQ
Friday, August 26, 2022
VA CIO Emphasizes Role of Automation, Cybersecurity in Tech Strategy - GovernmentCIO Media & Research
VA CIO Emphasizes Role of Automation, Cybersecurity in Tech Strategy GovernmentCIO Media & Research
http://dlvr.it/SXJqC3
http://dlvr.it/SXJqC3
Critical Vulnerability Discovered in Atlassian Bitbucket Server and Data Center
Atlassian has rolled out fixes for a critical security flaw in Bitbucket Server and Data Center that could lead to the execution of malicious code on vulnerable installations.
Tracked as CVE-2022-36804 (CVSS score: 9.9), the issue has been characterized as a command injection vulnerability in multiple endpoints that could be exploited via specially crafted HTTP requests.
“An
http://dlvr.it/SXJYn0
http://dlvr.it/SXJYn0
Cyber Security Today, August 26, 2022 - Protect your Active Directory servers, a huge text-based phishing scam found and more - IT World Canada
Cyber Security Today, August 26, 2022 - Protect your Active Directory servers, a huge text-based phishing scam found and more IT World Canada
http://dlvr.it/SXJDsk
http://dlvr.it/SXJDsk
AmiViz onboards Cyber Security Works - Trade Arabia
AmiViz onboards Cyber Security Works Trade Arabia
http://dlvr.it/SXHrGC
http://dlvr.it/SXHrGC
Cybercrime Groups Increasingly Adopting Sliver Command-and-Control Framework
Nation-state threat actors are increasingly adopting and integrating the Sliver command-and-control (C2) framework in their intrusion campaigns as a replacement for Cobalt Strike.
“Given Cobalt Strike’s popularity as an attack tool, defenses against it have also improved over time,” Microsoft security experts said. “Sliver thus presents an attractive alternative for actors looking for a
http://dlvr.it/SXHLzz
http://dlvr.it/SXHLzz
Thursday, August 25, 2022
The 11 most-prevalent malware strains of 2021 fuel cybercrime - Cybersecurity Dive
The 11 most-prevalent malware strains of 2021 fuel cybercrime Cybersecurity Dive
http://dlvr.it/SXFpdc
http://dlvr.it/SXFpdc
Cyber security threats 'need very real action' following overhaul - Lawyers Weekly
Cyber security threats 'need very real action' following overhaul Lawyers Weekly
http://dlvr.it/SXFXpw
http://dlvr.it/SXFXpw
The 'Trojan Horse' and the workforce: Job threats are focus of discussion during House hearing on cybersecurity - cityandstatepa.com
The 'Trojan Horse' and the workforce: Job threats are focus of discussion during House hearing on cybersecurity cityandstatepa.com
http://dlvr.it/SXFB7c
http://dlvr.it/SXFB7c
U.S. Government Spending Billions on Cybersecurity
In recent months, the House of Representatives has been hard at work drafting various spending bills for the 2023 fiscal year. While these bills provide funding for a vast array of government programs and agencies, there was one thing that really stands out. Collectively, the bills that are making their way through the house allocate a staggering $15.6 billion to cybersecurity spending.
As you
http://dlvr.it/SXDlc9
http://dlvr.it/SXDlc9
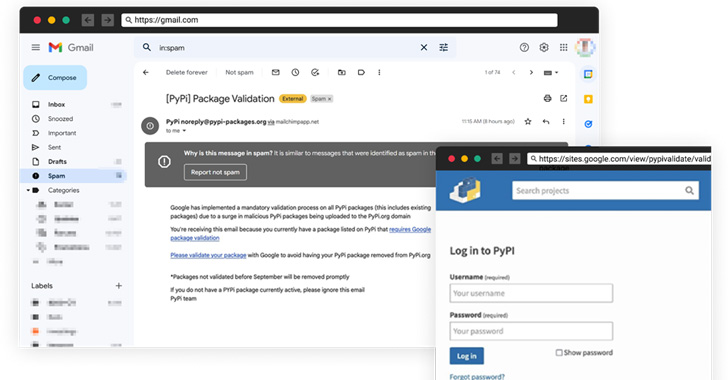
PyPI Repository Warns Python Project Maintainers About Ongoing Phishing Attacks
The Python Package Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing campaign that aims to steal developer credentials and inject malicious updates to legitimate packages.
"This is the first known phishing attack against PyPI," the maintainers of the official third-party software repository said in a series of tweets.
The social engineering attack entails sending
http://dlvr.it/SXDDLH
http://dlvr.it/SXDDLH
Wednesday, August 24, 2022
US NAIC Summer 2022 National Meeting Key Takeaways: Innovation, Cybersecurity, and Technology | Perspectives & Events - Mayer Brown
US NAIC Summer 2022 National Meeting Key Takeaways: Innovation, Cybersecurity, and Technology | Perspectives & Events Mayer Brown
http://dlvr.it/SXB1gj
http://dlvr.it/SXB1gj
Crypto Miners Using Tox P2P Messenger as Command and Control Server
Threat actors have begun to use the Tox peer-to-peer instant messaging service as a command-and-control method, marking a shift from its earlier role as a contact method for ransomware negotiations.
The findings from Uptycs, which analyzed an Executable and Linkable Format (ELF) artifact ("72client") that functions as a bot and can run scripts on the compromised host using the Tox protocol.
Tox
http://dlvr.it/SXB1VW
http://dlvr.it/SXB1VW
Guide: How Service Providers can Deliver vCISO Services at Scale
From ransomware to breaches, from noncompliance penalties to reputational damage – cyberthreats pose an existential risk to any business. But for SMEs and SMBs, the danger is compounded. These companies realize they need an in-house Chief Information Security Officer (CISO) – someone who can assess risks and vulnerabilities, create and execute a comprehensive cybersecurity plan, ensure
http://dlvr.it/SX9ZnT
http://dlvr.it/SX9ZnT
Researchers Find Counterfeit Phones with Backdoor to Hack WhatsApp Accounts
Budget Android device models that are counterfeit versions associated with popular smartphone brands are harboring multiple trojans designed to target WhatsApp and WhatsApp Business messaging apps.
The malware, which Doctor Web first came across in July 2022, were discovered in the system partition of at least four different smartphones: P48pro, radmi note 8, Note30u, and Mate40, was
"These
http://dlvr.it/SX94Pz
http://dlvr.it/SX94Pz
CVE-2022-36728
Library Management System v1.0 was discovered to contain a SQL injection vulnerability via the RollNo parameter at /staff/delstu.php. (CVSS:7.5) (Last Update:2022-08-22)
http://dlvr.it/SX94MR
http://dlvr.it/SX94MR
Wednesday, August 3, 2022
VMware Releases Patches for Several New Flaws Affecting Multiple Products
Virtualization services provider VMware on Tuesday shipped updates to address 10 security flaws affecting multiple products that could be abused by unauthenticated attackers to perform malicious actions.
The issues, tracked from CVE-2022-31656 through CVE-2022-31665 (CVSS scores: 4.7 - 9.8), impact VMware Workspace ONE Access, Workspace ONE Access Connector, Identity Manager, Identity Manager
http://dlvr.it/SVzyj0
http://dlvr.it/SVzyj0
Tuesday, August 2, 2022
Vulnerabilities in GPS tracker could put 1.5 million vehicles in danger | Cyber Security Hub - Cyber Security Hub
Vulnerabilities in GPS tracker could put 1.5 million vehicles in danger | Cyber Security Hub Cyber Security Hub
http://dlvr.it/SVxcMN
http://dlvr.it/SVxcMN
Chinese Hackers Using New Manjusaka Hacking Framework Similar to Cobalt Strike
Researchers have disclosed a new offensive framework called Manjusaka that they call a "Chinese sibling of Sliver and Cobalt Strike."
"A fully functional version of the command-and-control (C2), written in GoLang with a User Interface in Simplified Chinese, is freely available and can generate new implants with custom configurations with ease, increasing the likelihood of wider adoption of this
http://dlvr.it/SVx8Yn
http://dlvr.it/SVx8Yn
LockBit Ransomware Abuses Windows Defender to Deploy Cobalt Strike Payload
A threat actor associated with the LockBit 3.0 ransomware-as-a-service (RaaS) operation has been observed abusing the Windows Defender command-line tool to decrypt and load Cobalt Strike payloads.
According to a report published by SentinelOne last week, the incident occurred after obtaining initial access via the Log4Shell vulnerability against an unpatched VMware Horizon Server.
"Once initial
http://dlvr.it/SVwbym
http://dlvr.it/SVwbym
Monday, August 1, 2022
Vetted Software Developer & Cybersecurity Remote Staffing Service Announced - Digital Journal
Vetted Software Developer & Cybersecurity Remote Staffing Service Announced Digital Journal
http://dlvr.it/SVtyLZ
http://dlvr.it/SVtyLZ
Yale to Partner in NSF Program Advancing Cybersecurity and Privacy - Yale University
Yale to Partner in NSF Program Advancing Cybersecurity and Privacy Yale University
http://dlvr.it/SVtgGR
http://dlvr.it/SVtgGR
Two Key Ways Development Teams Can Increase Their Security Maturity
Now more than ever, organizations need to enable their development teams to build and grow their security skills. Today organizations face a threat landscape where individuals, well-financed syndicates, and state actors are actively trying to exploit errors in software. Yet, according to recent global research, 67% of developers that were interviewed said they were still shipping code they knew
http://dlvr.it/SVsv75
http://dlvr.it/SVsv75
Gootkit Loader Resurfaces with Updated Tactic to Compromise Targeted Computers
The operators of the Gootkit access-as-a-service (AaaS) malware have resurfaced with updated techniques to compromise unsuspecting victims.
"In the past, Gootkit used freeware installers to mask malicious files; now it uses legal documents to trick users into downloading these files," Trend Micro researchers Buddy Tancio and Jed Valderama said in a write-up last week.
The findings
http://dlvr.it/SVsLx4
http://dlvr.it/SVsLx4
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr













/cloudfront-us-east-1.images.arcpublishing.com/gray/WSAKYSTIQBANXNGC4TWWFVKZWU.jpg)