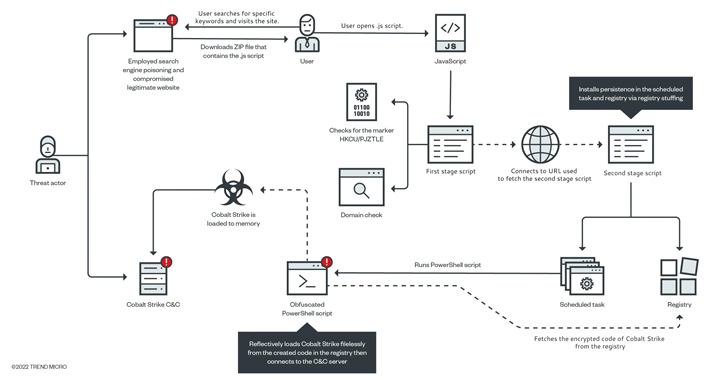
The operators of the Gootkit access-as-a-service (AaaS) malware have resurfaced with updated techniques to compromise unsuspecting victims.
"In the past, Gootkit used freeware installers to mask malicious files; now it uses legal documents to trick users into downloading these files," Trend Micro researchers Buddy Tancio and Jed Valderama said in a write-up last week.
The findings
http://dlvr.it/SVsLx4
Subscribe to:
Post Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr

No comments:
Post a Comment