Thanks to the economy, cybersecurity consolidation is coming. CISOs are more than ready. Protocol
http://dlvr.it/ST7rty
Thursday, June 30, 2022
Google Blocks Dozens of Malicious Domains Operated by Hack-for-Hire Groups
Google's Threat Analysis Group (TAG) on Thursday disclosed it had acted to block as many as 36 malicious domains operated by hack-for-hire groups from India, Russia, and the U.A.E.
In a manner analogous to the surveillanceware ecosystem, hack-for-hire firms equip their clients with capabilities to enable targeted attacks aimed at corporates as well as activists, journalists, politicians, and
http://dlvr.it/ST7rZw
http://dlvr.it/ST7rZw
CVE-2022-34006
An issue was discovered in TitanFTP (aka Titan FTP) NextGen before 1.2.1050. When installing, Microsoft SQL Express 2019 installs by default with an SQL instance running as SYSTEM with BUILTIN\Users as sysadmin, thus enabling unprivileged Windows users to execute commands locally as NT AUTHORITY\SYSTEM, aka NX-I674 (sub-issue 2). NOTE: as of 2022-06-21, the 1.2.1050 release corrects this vulnerability in a new installation, but not in an upgrade installation. (CVSS:7.2) (Last Update:2022-06-29)
http://dlvr.it/ST7NxK
http://dlvr.it/ST7NxK
What is Shadow IT and why is it so risky?
Shadow IT refers to the practice of users deploying unauthorized technology resources in order to circumvent their IT department. Users may resort to using shadow IT practices when they feel that existing IT policies are too restrictive or get in the way of them being able to do their jobs effectively.
An old school phenomenon
Shadow IT is not new. There have been countless examples of
http://dlvr.it/ST6r0L
http://dlvr.it/ST6r0L
Wednesday, June 29, 2022
Shifting the Cybersecurity Paradigm From Severity-Focused to Risk-Centric - DARKReading
Shifting the Cybersecurity Paradigm From Severity-Focused to Risk-Centric DARKReading
http://dlvr.it/ST4T4v
http://dlvr.it/ST4T4v
Long-time Cybersecurity Leader John Watters Joins Metabase Q's Board of Directors - Business Wire
Long-time Cybersecurity Leader John Watters Joins Metabase Q's Board of Directors Business Wire
http://dlvr.it/ST4Slf
http://dlvr.it/ST4Slf
SEC Proposes New Cybersecurity Rules for Public Companies - Security Intelligence
SEC Proposes New Cybersecurity Rules for Public Companies Security Intelligence
http://dlvr.it/ST4Sgt
http://dlvr.it/ST4Sgt
CVE-2022-33750
CA Automic Automation 12.2 and 12.3 contain an authentication error vulnerability in the Automic agent that could allow a remote attacker to potentially execute arbitrary commands. (CVSS:7.5) (Last Update:2022-06-28)
http://dlvr.it/ST40cT
http://dlvr.it/ST40cT
CISA Warns of Active Exploitation of 'PwnKit' Linux Vulnerability in the Wild
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) this week moved to add a Linux vulnerability dubbed PwnKit to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation.
The issue, tracked as CVE-2021-4034 (CVSS score: 7.8), came to light in January 2022 and concerns a case of local privilege escalation in polkit's pkexec utility, which allows an
http://dlvr.it/ST3ScY
http://dlvr.it/ST3ScY
Tuesday, June 28, 2022
Effective communication key to cybersecurity success - The Financial Express
Effective communication key to cybersecurity success The Financial Express
http://dlvr.it/ST0cHD
http://dlvr.it/ST0cHD
Minnesota cybersecurity company working towards accessible services for businesses across the country - EIN News
Minnesota cybersecurity company working towards accessible services for businesses across the country EIN News
http://dlvr.it/ST0cCW
http://dlvr.it/ST0cCW
ZuoRAT Malware Hijacking Home-Office Routers to Spy on Targeted Networks
A never-before-seen remote access trojan dubbed ZuoRAT has been singling out small office/home office (SOHO) routers as part of a sophisticated campaign targeting North American and European networks.
The malware "grants the actor the ability to pivot into the local network and gain access to additional systems on the LAN by hijacking network communications to maintain an undetected foothold,"
http://dlvr.it/ST0bb9
http://dlvr.it/ST0bb9
CVE-2022-33175
Power Distribution Units running on Powertek firmware (multiple brands) before 3.30.30 have an insecure permissions setting on the user.token field that is accessible to everyone through the /cgi/get_param.cgi HTTP API. This leads to disclosing active session ids of currently logged-in administrators. The session id can then be reused to act as the administrator, allowing reading of the cleartext password, or reconfiguring the device. (CVSS:7.5) (Last Update:2022-06-27)
http://dlvr.it/ST022C
http://dlvr.it/ST022C
Monday, June 27, 2022
Kugler Maag Cie and Argus Cyber Security Complete One of the World’s 1st Automotive SPICE® Assessment for - EIN News
Kugler Maag Cie and Argus Cyber Security Complete One of the World’s 1st Automotive SPICE® Assessment for EIN News
http://dlvr.it/SSxCZG
http://dlvr.it/SSxCZG
In-Vehicle Infotainment Cyber Security Market Size & Revenue Analysis – Designer Women - Designer Women
In-Vehicle Infotainment Cyber Security Market Size & Revenue Analysis – Designer Women Designer Women
http://dlvr.it/SSxC64
http://dlvr.it/SSxC64
87% of executives have no cybersecurity tools on personal devices - Security Magazine
87% of executives have no cybersecurity tools on personal devices Security Magazine
http://dlvr.it/SSxC3s
http://dlvr.it/SSxC3s
Researchers Warn of 'Matanbuchus' Malware Campaign Dropping Cobalt Strike Beacons
A malware-as-a-service (Maas) dubbed Matanbuchus has been observed spreading through phishing campaigns, ultimately dropping the Cobalt Strike post-exploitation framework on compromised machines.
Matanbuchus, like other malware loaders such as BazarLoader, Bumblebee, and Colibri, is engineered to download and execute second-stage executables from command-and-control (C&C) servers on infected
http://dlvr.it/SSwfw5
http://dlvr.it/SSwfw5
Sunday, June 26, 2022
Critical Analysis of Cybersecurity in the Government Sector - Analytics Insight
Critical Analysis of Cybersecurity in the Government Sector Analytics Insight
http://dlvr.it/SStC1c
http://dlvr.it/SStC1c
Russia's War Is Elevating Cybersecurity Concerns For Emerging Markets - OilPrice.com
Russia's War Is Elevating Cybersecurity Concerns For Emerging Markets OilPrice.com
http://dlvr.it/SStBZ6
http://dlvr.it/SStBZ6
Saturday, June 25, 2022
Improve Cyber Security with SIEM as Part of an Overall Security Solution - PR Web
Improve Cyber Security with SIEM as Part of an Overall Security Solution PR Web
http://dlvr.it/SSqrpl
http://dlvr.it/SSqrpl
Glorin Sebastian, first Keralite to be on list of world’s top cyber-security experts - Onmanorama
Glorin Sebastian, first Keralite to be on list of world’s top cyber-security experts Onmanorama
http://dlvr.it/SSqrm7
http://dlvr.it/SSqrm7
CVE-2022-32101
kkcms v1.3.7 was discovered to contain a SQL injection vulnerability via the cid parameter at /template/wapian/vlist.php. (CVSS:7.5) (Last Update:2022-06-24)
http://dlvr.it/SSqT2F
http://dlvr.it/SSqT2F
Friday, June 24, 2022
CVE-2022-32230
Microsoft Windows SMBv3 suffers from a null pointer dereference in versions of Windows prior to the April, 2022 patch set. By sending a malformed FileNormalizedNameInformation SMBv3 request over a named pipe, an attacker can cause a Blue Screen of Death (BSOD) crash of the Windows kernel. For most systems, this attack requires authentication, except in the special case of Windows Domain Controllers, where unauthenticated users can always open named pipes as long as they can establish an SMB session. Typically, after the BSOD, the victim SMBv3 server will reboot. (CVSS:7.8) (Last Update:2022-06-23)
http://dlvr.it/SSmmDY
http://dlvr.it/SSmmDY
CVE-2022-32251
A vulnerability has been identified in SINEMA Remote Connect Server (All versions < V3.1). There is a missing authentication verification for a resource used to change the roles and permissions of a user. This could allow an attacker to change the permissions of any user and gain the privileges of an administrative user. (CVSS:7.5) (Last Update:2022-06-22)
http://dlvr.it/SSmlld
http://dlvr.it/SSmlld
CVE-2022-32262
A vulnerability has been identified in SINEMA Remote Connect Server (All versions < V3.1). The affected application contains a file upload server that is vulnerable to command injection. An attacker could use this to achieve arbitrary code execution. (CVSS:7.5) (Last Update:2022-06-22)
http://dlvr.it/SSmkv6
http://dlvr.it/SSmkv6
CVE-2022-32272
OPSWAT MetaDefender Core before 5.1.2, MetaDefender ICAP before 4.12.1, and MetaDefender Email Gateway Security before 5.6.1 have incorrect access control, resulting in privilege escalation. (CVSS:7.5) (Last Update:2022-06-21)
http://dlvr.it/SSmkT7
http://dlvr.it/SSmkT7
CVE-2022-32511
jmespath.rb (aka JMESPath for Ruby) before 1.6.1 uses JSON.load in a situation where JSON.parse is preferable. (CVSS:7.5) (Last Update:2022-06-17)
http://dlvr.it/SSmkQ9
http://dlvr.it/SSmkQ9
Saturday, June 4, 2022
National Cybersecurity Preparedness Consortium Act Signed into Law - HS Today - HSToday
National Cybersecurity Preparedness Consortium Act Signed into Law - HS Today HSToday
http://dlvr.it/SRbmdT
http://dlvr.it/SRbmdT
Friday, June 3, 2022
CVE-2022-30595
libImaging/TgaRleDecode.c in Pillow 9.1.0 has a heap buffer overflow in the processing of invalid TGA image files. (CVSS:7.5) (Last Update:2022-06-03)
http://dlvr.it/SRb3Xx
http://dlvr.it/SRb3Xx
Cyber Security careers - a young person's guide - Department for the Economy
Cyber Security careers - a young person's guide Department for the Economy
http://dlvr.it/SRZkV0
http://dlvr.it/SRZkV0
GitLab Issues Security Patch for Critical Account Takeover Vulnerability
GitLab has moved to address a critical security flaw in its service that, if successfully exploited, could result in an account takeover.
Tracked as CVE-2022-1680, the issue has a CVSS severity score of 9.9 and was discovered internally by the company. The security flaw affects all versions of GitLab Enterprise Edition (EE) starting from 11.10 before 14.9.5, all versions starting from 14.10
http://dlvr.it/SRZJPs
http://dlvr.it/SRZJPs
Researchers Uncover Malware Controlling Thousands of Sites in Parrot TDS Network
The Parrot traffic direction system (TDS) that came to light earlier this year has had a larger impact than previously thought, according to new research.
Sucuri, which has been tracking the same campaign since February 2019 under the name "NDSW/NDSX," said that "the malware was one of the top infections" detected in 2021, accounting for more than 61,000 websites.
Parrot TDS was documented in
http://dlvr.it/SRYphS
http://dlvr.it/SRYphS
Hackers Exploiting Unpatched Critical Atlassian Confluence Zero-Day Vulnerability
Atlassian has warned of a critical unpatched remote code execution vulnerability impacting Confluence Server and Data Center products that it said is being actively exploited in the wild.
The Australian software company credited cybersecurity firm Volexity for identifying the flaw, which is being tracked as CVE-2022-26134.
"Atlassian has been made aware of current active exploitation of a
http://dlvr.it/SRXqdr
http://dlvr.it/SRXqdr
Thursday, June 2, 2022
CVE-2022-31245
mailcow before 2022-05d allows a remote authenticated user to inject OS commands and escalate privileges to domain admin via the --debug option in conjunction with the ---PIPEMESS option in Sync Jobs. (CVSS:9.0) (Last Update:2022-06-02)
http://dlvr.it/SRWvfv
http://dlvr.it/SRWvfv
Threat Detection Software: A Deep Dive
As the threat landscape evolves and multiplies with more advanced attacks than ever, defending against these modern cyber threats is a monumental challenge for almost any organization.
Threat detection is about an organization’s ability to accurately identify threats, be it to the network, an endpoint, another asset or an application – including cloud infrastructure and assets. At scale, threat
http://dlvr.it/SRWXtc
http://dlvr.it/SRWXtc
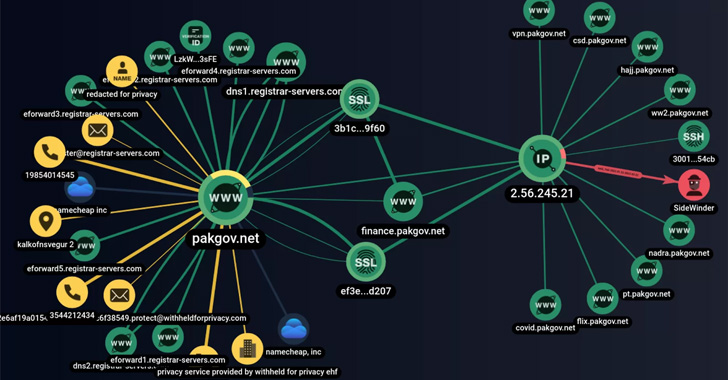
SideWinder Hackers Use Fake Android VPN Apps to Target Pakistani Entities
The threat actor known as SideWinder has added a new custom tool to its arsenal of malware that's being used in phishing attacks against Pakistani public and private sector entities.
"Phishing links in emails or posts that mimic legitimate notifications and services of government agencies and organizations in Pakistan are primary attack vectors of the gang," Singapore-headquartered cybersecurity
http://dlvr.it/SRVbvY
http://dlvr.it/SRVbvY
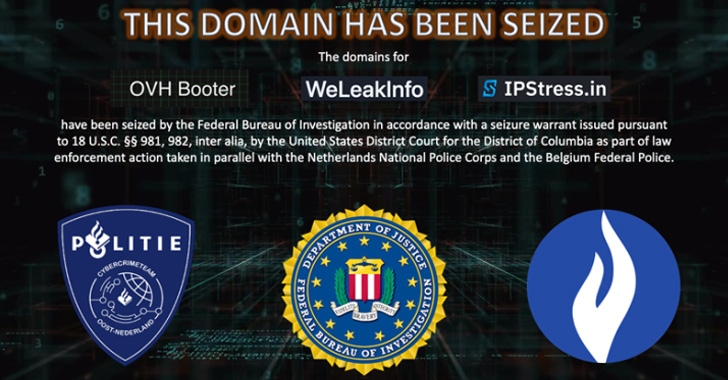
DOJ Seizes 3 Web Domains Used to Sell Stolen Data and DDoS Services
The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of three domains used by cybercriminals to trade stolen personal information and facilitate distributed denial-of-service (DDoS) attacks for hire.
This includes weleakinfo[.]to, ipstress[.]in, and ovh-booter[.]com, the former of which allowed its users to traffic hacked personal data and offered a searchable database
http://dlvr.it/SRTbSN
http://dlvr.it/SRTbSN
Wednesday, June 1, 2022
Email remains top cyberattack vector, more cybersecurity pros needed – Fortinet - Rappler
Email remains top cyberattack vector, more cybersecurity pros needed – Fortinet Rappler
http://dlvr.it/SRSgWj
http://dlvr.it/SRSgWj
Commonwealth Cyber Initiative researchers at Virginia Tech explore how quantum networks could transform cybersecurity - Virginia Tech Daily
Commonwealth Cyber Initiative researchers at Virginia Tech explore how quantum networks could transform cybersecurity Virginia Tech Daily
http://dlvr.it/SRSJ2Q
http://dlvr.it/SRSJ2Q
New Unpatched Horde Webmail Bug Lets Hackers Take Over Server by Sending Email
A new unpatched security vulnerability has been disclosed in the open-source Horde Webmail client that could be exploited to achieve remote code execution on the email server simply by sending a specially crafted email to a victim.
"Once the email is viewed, the attacker can silently take over the complete mail server without any further user interaction," SonarSource said in a report shared
http://dlvr.it/SRRqy6
http://dlvr.it/SRRqy6
Chinese Hackers Begin Exploiting Latest Microsoft Office Zero-Day Vulnerability
An advanced persistent threat (APT) actor aligned with Chinese state interests has been observed weaponizing the new zero-day flaw in Microsoft Office to achieve code execution on affected systems.
"TA413 CN APT spotted [in-the-wild] exploiting the Follina zero-day using URLs to deliver ZIP archives which contain Word Documents that use the technique," enterprise security firm Proofpoint said in
http://dlvr.it/SRRH8b
http://dlvr.it/SRRH8b
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr