Samba has issued software updates to address multiple security vulnerabilities that, if successfully exploited, could allow remote attackers to execute arbitrary code with the highest privileges on affected installations.
Chief among them is CVE-2021-44142, which impacts all versions of Samba before 4.13.17 and concerns an out-of-bounds heap read/write vulnerability in the VFS module "vfs_fruit"
http://dlvr.it/SJ8yPc
Monday, January 31, 2022
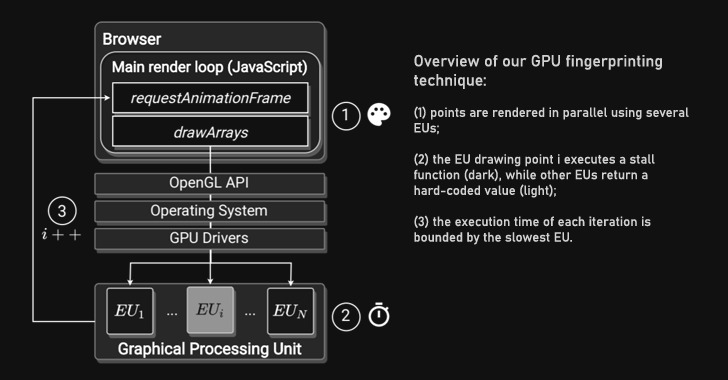
Your Graphics Card Fingerprint Can Be Used to Track Your Activities Across the Web
Researchers have demonstrated a new type of fingerprinting technique that exploits a machine's graphics processing unit (GPU) as a means to track users across the web persistently.
Dubbed DrawnApart, the method "identifies a device from the unique properties of its GPU stack," researchers from Australia, France, and Israel said in a new paper," adding " variations in speed among the multiple
http://dlvr.it/SJ7ZjS
http://dlvr.it/SJ7ZjS
Veteran FBI, Global Cybersecurity Investigations Expert Todd Renner Joins FTI Consulting - The Bakersfield Californian
Veteran FBI, Global Cybersecurity Investigations Expert Todd Renner Joins FTI Consulting The Bakersfield Californian
http://dlvr.it/SJ741V
http://dlvr.it/SJ741V
Why Developer-First Is the Future of Application Security (And How to Choose a Platform) - CPO Magazine
Why Developer-First Is the Future of Application Security (And How to Choose a Platform) CPO Magazine
http://dlvr.it/SJ6X4q
http://dlvr.it/SJ6X4q
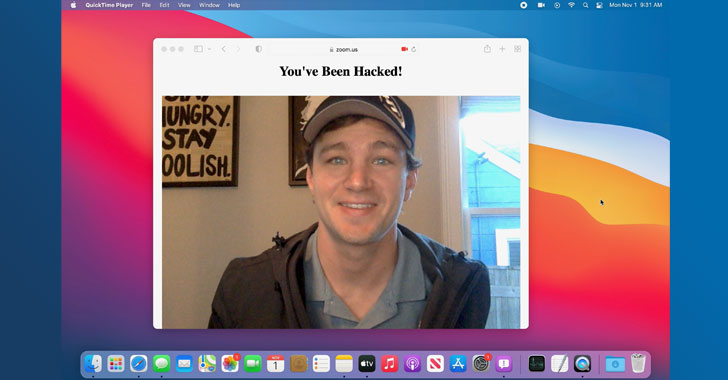
Apple Pays $100,500 Bounty to Hacker Who Found Way to Hack MacBook Webcam
Apple last year fixed a new set of macOS vulnerabilities that exposed Safari browser to attack, potentially allowing malicious actors to access users' online accounts, microphone, and webcam.
Security researcher Ryan Pickren, who discovered and reported the bugs to the iPhone maker, was compensated with a $100,500 bug bounty, underscoring the severity of the issues.
By exploiting a chain of
http://dlvr.it/SJ63SG
http://dlvr.it/SJ63SG
Sunday, January 30, 2022
DeepDotWeb News Site Operator Sentenced to 8 Years for Money Laundering
An Israeli national was sentenced to 97 months in prison in connection with operating the DeepDotWeb (DDW) clearnet website, nearly a year after the individual pleaded guilty to the charges.
Tal Prihar, 37, an Israeli citizen residing in Brazil, is said to have played the role of an administrator of DDW since the website became functional in October 2013. He pleaded guilty to money laundering
http://dlvr.it/SJ5gk0
http://dlvr.it/SJ5gk0
Security experts doubt Ukraine readiness against Russian cyber attack - KUER 90.1
Security experts doubt Ukraine readiness against Russian cyber attack KUER 90.1
http://dlvr.it/SJ4G0z
http://dlvr.it/SJ4G0z
Business calls for immediate and definite action on cybersecurity - ICC - International Chamber of Commerce
Business calls for immediate and definite action on cybersecurity - ICC International Chamber of Commerce
http://dlvr.it/SJ3xQy
http://dlvr.it/SJ3xQy
Saturday, January 29, 2022
Cyber Swachhta Kendra To maintain your cyber security - Jammu Kashmir Latest News | Tourism | Breaking News J&K - Daily Excelsior
Cyber Swachhta Kendra To maintain your cyber security - Jammu Kashmir Latest News | Tourism | Breaking News J&K Daily Excelsior
http://dlvr.it/SJ3Nzt
http://dlvr.it/SJ3Nzt
Cyber Security Today, Dec. 13, 2021 - The hunt for apps with log4j vulnerabilities continues, new threat and ransomware groups discovered and a warning to WordPress admins - IT World Canada
Cyber Security Today, Dec. 13, 2021 - The hunt for apps with log4j vulnerabilities continues, new threat and ransomware groups discovered and a warning to WordPress admins IT World Canada
http://dlvr.it/SJ20MP
http://dlvr.it/SJ20MP
Friday, January 28, 2022
CVE-2022-23852
Expat (aka libexpat) before 2.4.4 has a signed integer overflow in XML_GetBuffer, for configurations with a nonzero XML_CONTEXT_BYTES. (CVSS:7.5) (Last Update:2022-01-28)
http://dlvr.it/SJ11nx
http://dlvr.it/SJ11nx
Governor Cooper Encourages High School Students to Explore Cybersecurity Careers | NCDIT - Governor Roy Cooper
Governor Cooper Encourages High School Students to Explore Cybersecurity Careers | NCDIT Governor Roy Cooper
http://dlvr.it/SHzCVP
http://dlvr.it/SHzCVP
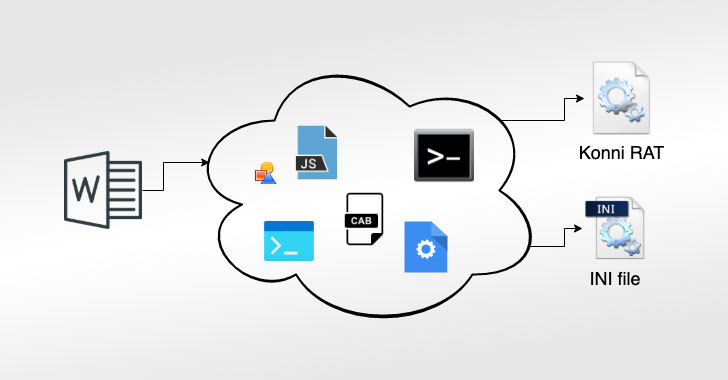
North Korean Hackers Return with Stealthier Variant of KONNI RAT Malware
A cyberespionage group with ties to North Korea has resurfaced with a stealthier variant of its remote access trojan called Konni to attack political institutions located in Russia and South Korea.
"The authors are constantly making code improvements," Malwarebytes researcher Roberto Santos said. "Their efforts are aimed at breaking the typical flow recorded by sandboxes and making detection
http://dlvr.it/SHygnt
http://dlvr.it/SHygnt
CVE-2022-23363
Online Banking System v1.0 was discovered to contain a SQL injection vulnerability via index.php. (CVSS:7.5) (Last Update:2022-01-27)
http://dlvr.it/SHyCVq
http://dlvr.it/SHyCVq
Thursday, January 27, 2022
Microsoft Mitigated Record-Breaking 3.47 Tbps DDoS Attack on Azure Customers
Microsoft this week revealed that it had fended off a record number of distributed denial-of-service (DDoS) attacks aimed at its customers in 2021, three of which surpassed 2.4 terabit per second (Tbps).
One of the DDoS attacks took place in November, targeting an unnamed Azure customer in Asia and lasted a total of 15 minutes. It hit a peak throughput of 3.47 Tbps and a packet rate of 340
http://dlvr.it/SHxr72
http://dlvr.it/SHxr72
Chaes Banking Trojan Hijacks Chrome Browser with Malicious Extensions
A financially-motivated malware campaign has compromised over 800 WordPress websites to deliver a banking trojan dubbed Chaes targeting Brazilian customers of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
First documented by Cybereason in November 2020, the info-stealing malware is delivered via a sophisticated infection chain that's engineered to harvest
http://dlvr.it/SHvqX9
http://dlvr.it/SHvqX9
Widespread FluBot and TeaBot Malware Campaigns Targeting Android Devices
Researchers from the Bitdefender Mobile Threats team said they have intercepted more than 100,000 malicious SMS messages attempting to distribute Flubot malware since the beginning of December.
"Findings indicate attackers are modifying their subject lines and using older yet proven scams to entice users to click," the Romanian cybersecurity firm detailed in a report published Wednesday. "
http://dlvr.it/SHvFVz
http://dlvr.it/SHvFVz
Resecurity Partners with ML Consulting to Advance Intelligent Cyber Security Solutions in MEA - PRNewswire
Resecurity Partners with ML Consulting to Advance Intelligent Cyber Security Solutions in MEA PRNewswire
http://dlvr.it/SHtmtT
http://dlvr.it/SHtmtT
Hackers Using New Evasive Technique to Deliver AsyncRAT Malware
A new, sophisticated phishing attack has been observed delivering the AsyncRAT trojan as part of a malware campaign that's believed to have commenced in September 2021.
"Through a simple email phishing tactic with an html attachment, threat attackers are delivering AsyncRAT (a remote access trojan) designed to remotely monitor and control its infected computers through a secure, encrypted
http://dlvr.it/SHtmLP
http://dlvr.it/SHtmLP
Wednesday, January 26, 2022
Apple Releases iOS and macOS Updates to Patch Actively Exploited 0-Day Vulnerability
Apple on Wednesday released iOS 15.3 and macOS Monterey 12.2 with a fix for the privacy-defeating bug in Safari, as well as to contain a zero-day flaw, which it said has been exploited in the wild to break into its devices.
Tracked as CVE-2022-22587, the vulnerability relates to a memory corruption issue in the IOMobileFrameBuffer component that could be abused by a malicious application to
http://dlvr.it/SHtNR4
http://dlvr.it/SHtNR4
Initial Access Broker Involved in Log4Shell Attacks Against VMware Horizon Servers
An initial access broker group tracked as Prophet Spider has been linked to a set of malicious activities that exploits the Log4Shell vulnerability in unpatched VMware Horizon Servers.
According to new research published by BlackBerry Research & Intelligence and Incident Response (IR) teams today, the cybercrime actor has been opportunistically weaponizing the shortcoming to download a
http://dlvr.it/SHrKG7
http://dlvr.it/SHrKG7
Biden Signs NDAA Relying on Voluntary Private-Sector Cybersecurity Collaboration - Nextgov
Biden Signs NDAA Relying on Voluntary Private-Sector Cybersecurity Collaboration Nextgov
http://dlvr.it/SHqJr3
http://dlvr.it/SHqJr3
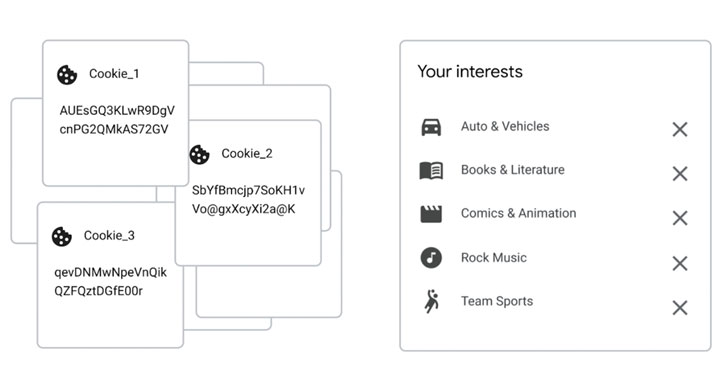
Google Drops FLoC and Introduces Topics API to Replace Tracking Cookies for Ads
Google on Tuesday announced that it is abandoning its controversial plans for replacing third-party cookies in favor of a new Privacy Sandbox proposal called Topics, which categorizes users' browsing habits into approximately 350 topics.
Thee new framework, which takes the place of FLoC (short for Federated Learning of Cohorts), slots users' browsing history for a given week into a handful of
http://dlvr.it/SHqH9B
http://dlvr.it/SHqH9B
Tuesday, January 25, 2022
The 'new normal' for cybersecurity - SecurityInfoWatch
The 'new normal' for cybersecurity SecurityInfoWatch
http://dlvr.it/SHpvlh
http://dlvr.it/SHpvlh
12-Year-Old Polkit Flaw Lets Unprivileged Linux Users Gain Root Access
A 12-year-old security vulnerability has been disclosed in a system utility called Polkit that grants attackers root privileges on Linux systems, even as a proof-of-concept (PoC) exploit has emerged in the wild merely hours after technical details of the bug became public.
Dubbed "PwnKit" by cybersecurity firm Qualys, the weakness impacts a component in polkit called pkexec, a program that's
http://dlvr.it/SHptb0
http://dlvr.it/SHptb0
Hackers Infect macOS with New DazzleSpy Backdoor in Watering-Hole Attacks
A previously undocumented cyber-espionage malware aimed at Apple's macOS operating system leveraged a Safari web browser exploit as part of a watering hole attack targeting politically active, pro-democracy individuals in Hong Kong.
Slovak cybersecurity firm ESET attributed the intrusion to an actor with "strong technical capabilities," calling out the campaign's overlaps to that of a similar
http://dlvr.it/SHmr7f
http://dlvr.it/SHmr7f
Hackers Using New Malware Packer DTPacker to Avoid Analysis, Detection
A previously undocumented malware packer named DTPacker has been observed distributing multiple remote access trojans (RATs) and information stealers such as Agent Tesla, Ave Maria, AsyncRAT, and FormBook to plunder information and facilitate follow-on attacks.
"The malware uses multiple obfuscation techniques to evade antivirus, sandboxing, and analysis," enterprise security company Proofpoint
http://dlvr.it/SHlpNY
http://dlvr.it/SHlpNY
Monday, January 24, 2022
CVE-2022-22122
In Mattermost Focalboard, versions prior to v0.7.5, v0.8.4, v0.9.5, v0.10.1 and v0.11.0-rc1; as used respectively in Mattermost, versions prior to v5.37.6, v5.39.3, v6.0.4, v6.1.1 and v6.2.0, are vulnerable to Insufficient Session Expiration. When a user initiates a logout, their session is not invalidated properly. In addition, user sessions are stored in the browser’s local storage, which by default does not have an expiration time. This makes it possible for an attacker to steal and reuse the cookies using techniques such as XSS attacks, to completely take over a victim account. (CVSS:7.5) (Last Update:2022-01-24)
http://dlvr.it/SHkrf6
http://dlvr.it/SHkrf6
CVE-2022-23227
NUUO NVRmini2 through 3.11 allows an unauthenticated attacker to upload an encrypted TAR archive, which can be abused to add arbitrary users because of the lack of handle_import_user.php authentication. When combined with another flaw (CVE-2011-5325), it is possible to overwrite arbitrary files under the web root and achieve code execution as root. (CVSS:10.0) (Last Update:2022-01-21)
http://dlvr.it/SHjQxn
http://dlvr.it/SHjQxn
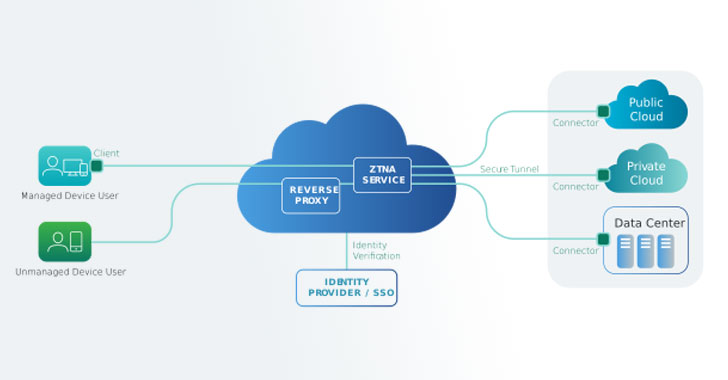
ZTNAs Address Requirements VPNs Cannot. Here's Why.
I recently hopped on the Lookout podcast to talk about virtual private networks (VPNs) and how they've been extended beyond their original use case of connecting remote laptops to your corporate network. Even in this new world where people are using personal devices and cloud apps, VPN continues to be the go-to solution for remote access and cloud access. After my conversation with Hank Schless,
http://dlvr.it/SHjNkK
http://dlvr.it/SHjNkK
Subscribe to:
Comments (Atom)
Cybersecurity needs AI as much as AI needs cybersecurity - Techzine Europe
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr
-
This statistic presents a ranking of the countries with the highest commitment to cyber security based on the Global Cybersecurity Index (GC...
-
Supply chain cyberattacks threaten healthcare. Here’s how the industry can work together to limit disruption. Healthcare Dive http://dlvr...
-
Cybersecurity needs AI as much as AI needs cybersecurity Techzine Europe http://dlvr.it/TDY1dr